
Virus Bulletin
@virusbtn
Security information portal, testing and certification body. Organisers of the annual Virus Bulletin conference. @[email protected]
A little taste of what’s coming up at VB2025 🎬 Can’t wait to see so many of you in Berlin this September. If you haven’t registered yet, now’s the time: Early Bird ends this week 🎟️ Secure your place now 👉tinyurl.com/a2edw4jh #vb2025 #cybersecurity #berlin
eSentire's Threat Response Unit (TRU) look into Cyber Stealer, a newly developing multi-purpose malware that combines information stealing capabilities with botnet functionality to create a versatile attack platform. esentire.com/blog/cyber-ste…
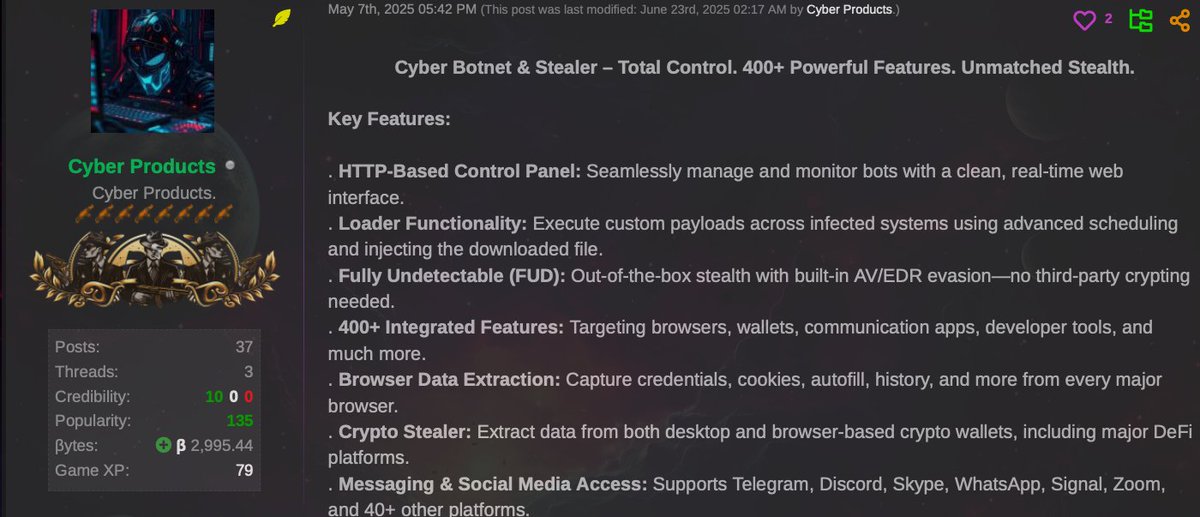
Acronis researchers Jozsef Gegeny & Ilia Dafchev explore recent stealer campaigns built on top of the Electron framework, such as Leet Stealer, RMC Stealer (a modified version of Leet Stealer) and Sniffer Stealer. acronis.com/en-us/tru/post…
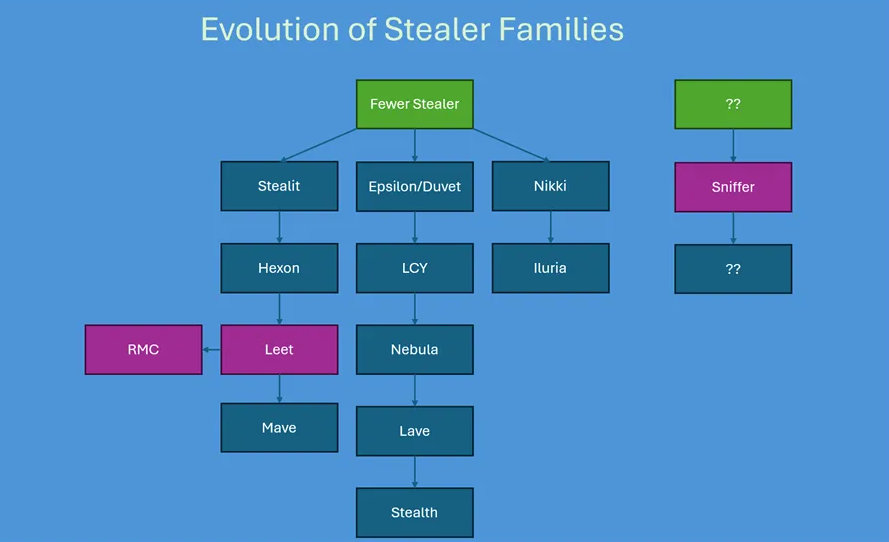
In a Hybrid Analysis blog post Vlad Pasca analyses SHUYAL - an infostealer that can grab credentials from 19 different web browsers but also use evasion tactics such as automatic Task Manager disablement. hybrid-analysis.blogspot.com/2025/07/new-ad…
Cisco Talos researchers unmask recent Chaos RaaS attacks. The threat group uses low-effort spam flooding, escalating to voice-based social engineering for access; RMM tool abuse for persistent connection; & legitimate file-sharing software for exfiltration blog.talosintelligence.com/new-chaos-rans…

In H1 2025, #ESETResearch telemetry recorded a 160% surge in #Android adware & clicker detections. Leading this spike is a colorfully branded threat #Kaleidoscope, responsible for 28% of all Android #adware detections in H1. 1/6
The FBI has put out a much more nuanced explanation of what CTI researchers have been tracking for years: ic3.gov/PSA/2025/PSA25… Completely different from what CISA put out in 2023 on “Scattered Spider” here: cisa.gov/news-events/cy… One is holistic, the other is DFIR focused.
🚨Job seekers, watch out! 🚨 @Proofpoint found threat actors targeting job seekers to distribute remote management tools that can lead to data or financial theft, or potentially to install follow-on malware like ransomware. 🧵⤵️
Leading security companies are sending their teams to #VB2025, and not without reason. Research-first content, real-world relevance, and networking that actually helps. 📍 Berlin | 24–26 Sept See the top 5 reasons in our blog post 👇 tinyurl.com/576fxm2u

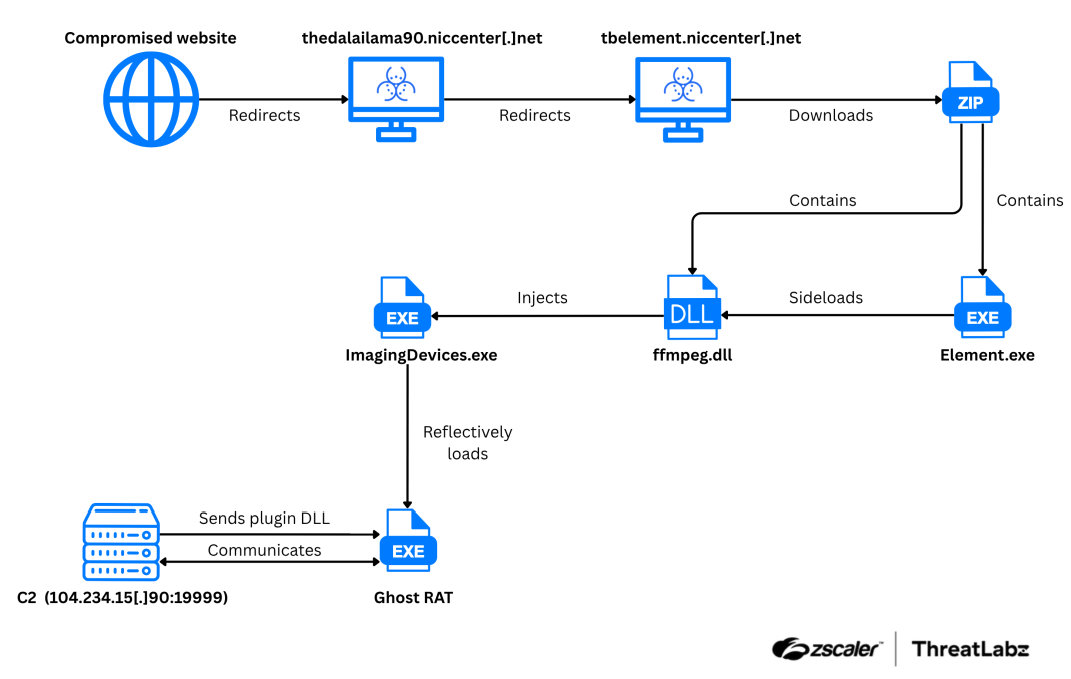
Zscaler ThreatLabz collaborated with TibCERT to investigate two campaigns targeting the Tibetan community. Operation GhostChat & Operation PhantomPrayers relied on multi-stage infection chains to deploy the Ghost RAT and PhantomNet backdoors, respectively. zscaler.com/blogs/security…
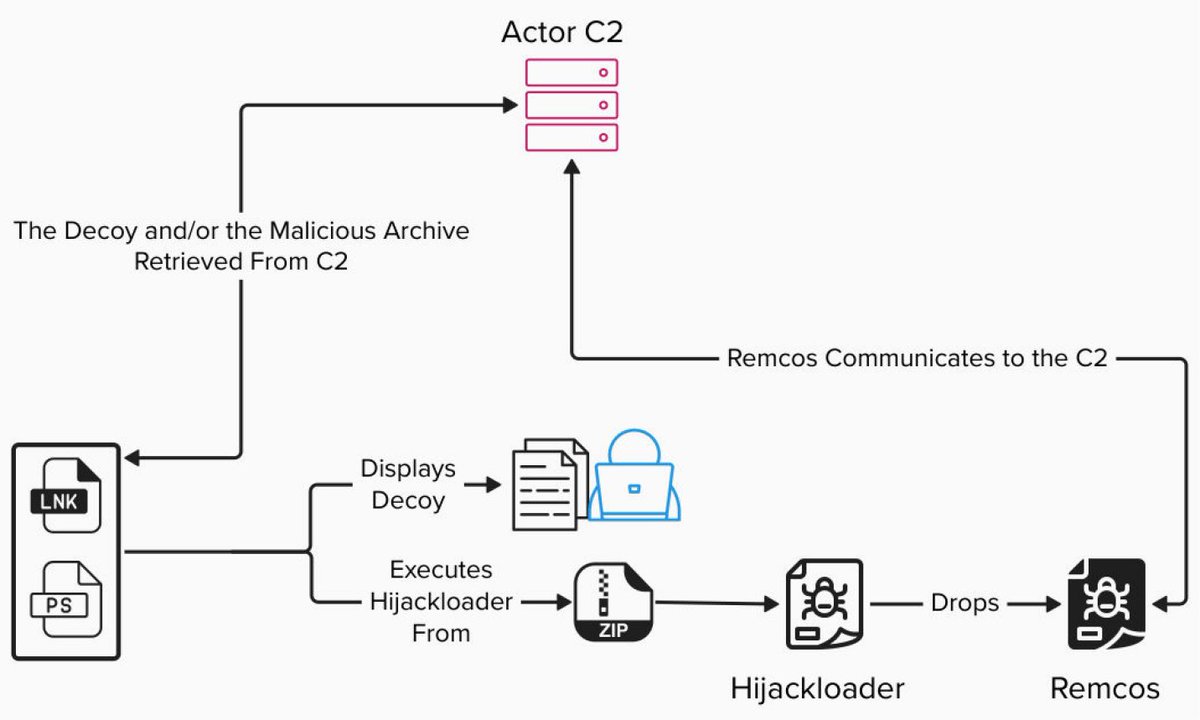
IBM X-Force researchers Joe Fasulo & Aaron Gdanski look into active Hive0156 Remcos RAT campaigns targeting victims in Ukraine using military themes for decoy documents. ibm.com/think/x-force/…
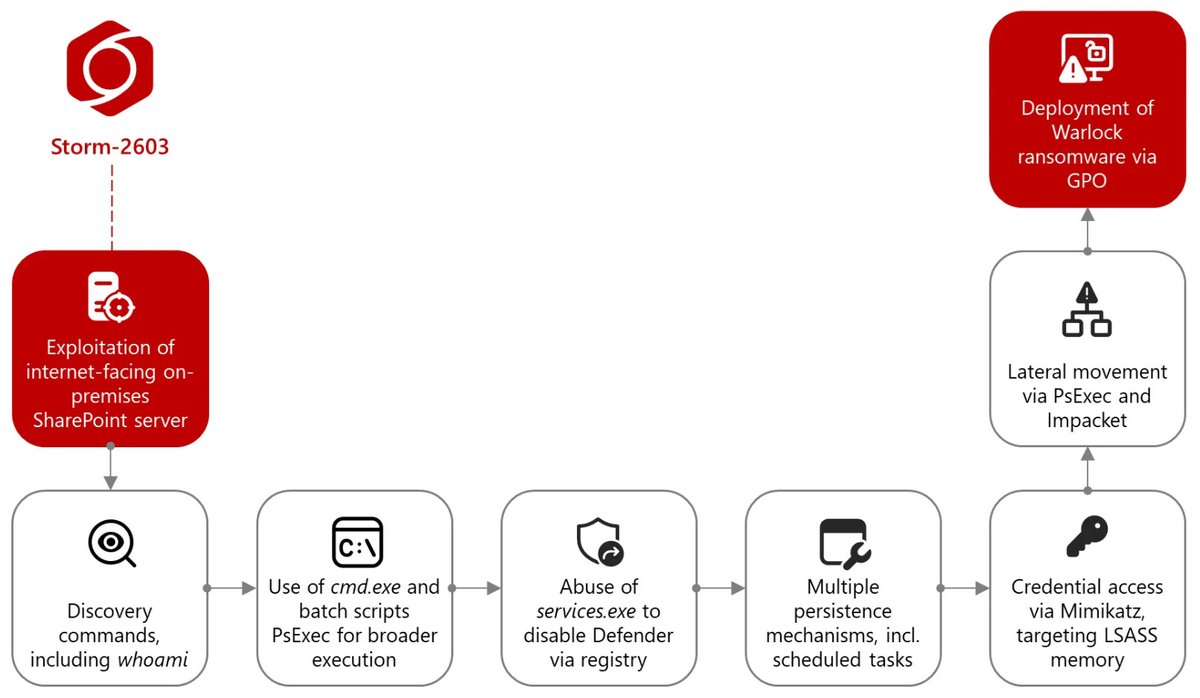
Microsoft Threat Intelligence team share details of Storm-2603 activity that leads to the deployment of Warlock ransomware by exploitation of on-premises SharePoint vulnerabilities CVE-2025-49706 & CVE-2025-49704. microsoft.com/en-us/security…
Mandiant has observed an increasing number of attacks targeting VMware vSphere in recent years, notably for deploying ransomware. Dive deep into what specifically is fueling this trend and get actionable guidance to defend your VMware vSphere estate in our latest blog posts. 👇
100 Days of YARA, YARA Rule Tips and The Current State of Email borne Threats with Greg Lesnewich x.com/i/broadcasts/1…
Hey :) My @SLEUTHCON talk on bulletproof hosting & proxy "bundle offers" is now live! If you need your daily dose of turbo speed "frenglish," here's your chance. All about the growing threat from proxy providers. 📺 Watch here: youtube.com/watch?v=A1_YbC… Feedback welcome! :)
A 2025 version of #SoulStealer, an #infostealer released for educational purposes, is available, featuring updated infrastructure and additional functionality compared to the 2024 version. More info at bit.ly/3IWJEHu
💡 Just a small tool tip for the best parsing and verifying of embedded #authenticode signatures (certificates) in #PE files: just use the #signify tool - trust me (recommended to use the code in examples folder): github.com/ralphje/signify ☑️ It gives you the most detailed verbose…
AI integration may seem very recent, but has been woven into the fabric of cybersecurity for many years. However, there are still improvements to be made. In our industry, models are often deployed on a massive scale, processing billions of events a day.
Welcome our newest #VB2025 partners: 🌟 @amazon (Gold Partner) 🥈 @GenDigitalInc (Silver Partner) 🥉 @SoftwareClean (CSA), @Fortinet & Varist (Bronze Partners) 🤝 @totalavcom (Getting Connected tier) Join them & showcase your brand in Berlin: 👉 tinyurl.com/4w7m4uak

NCC Group’s Molly Dewis delves into a recent incident in which the Lumma infostealer was distributed via a fake CAPTCHA verification page. nccgroup.com/us/research-bl…
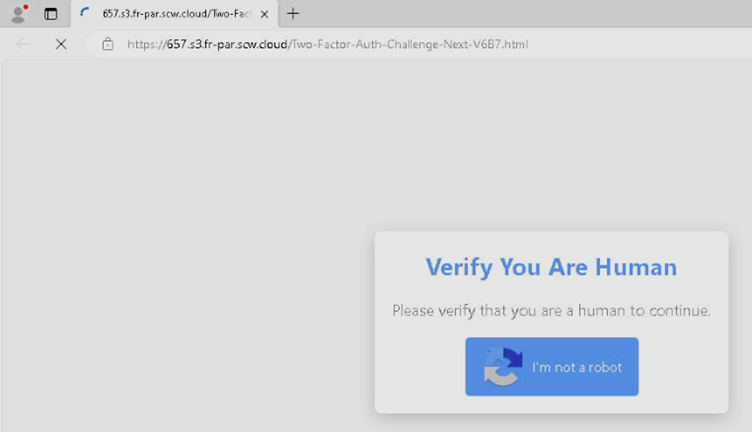
Trend Micro's Junestherry Dela Cruz shares the latest methods used in Lumma Stealer distribution. Lumma Stealer re-emerged shortly after its takedown; the group behind it appears to be intent on employing covert tactics while steadily expanding its reach. trendmicro.com/en_us/research…
