
LuemmelSec
@theluemmel
I speak BloodHound. Husband, Father, IT-Guy, Security-Noob Blog: http://luemmelsec.de GitHub: http://github.com/LuemmelSec
I can finally release my work on Amazon Cognito Ratelimit Bypassing as the fix is now globally deployed. luemmelsec.github.io/Amazon-Cognito… Huge shoutout to James Kettle who discovered this attack vector and made the info public. Let me know what you think in the comments.

Classic NTLM relay problem: Stuck on port 445/TCP, can't use WMI (needs 135/TCP), and dumping hashes triggers EDR alerts. So what's a stealthy attacker to do? 🤔 Our latest blog post explores evasive alternatives beyond the old techniques. ghst.ly/3ILR1l0
This week I discovered we couldn't use my Entra Operational Group to create the per-user MFA groups because GCC doesn't allow Graph PowerShell to get tokens that work with this API endpoint This technique worked around this limitation, very cool! :) github.com/nathanmcnulty/…
My first @SpecterOps blog! Ever wanted to collect Active Directory information from LDAP for a Red Team? Using LDAP's more OPSEC-considerate cousin: ADWS can be used to improve upon the already present advantages of using smaller-scaling LDAP queries. specterops.io/blog/2025/07/2…
What is OAuth Consent Phishing? It’s a social engineering trick where the user grants access to a malicious app. What is Token Replay? It’s when you reuse stolen OAuth tokens to access cloud services without logging in again even after the user changes their password.
This is seriously cool. Thanks @testanull While it can be super useful to get your old shit updated it also shows how threat actors are working to get their next bypass or vulnerability up to speed.
testbnull.medium.com/no-one-thing-w… A nasty hack to save your exiled server from being pwn Not a recommended way, but it can save your work sometime Have a good read!
Friendly reminder to set up (or review) your security.txt securitytxt.org
Some companies really make it hard to do the right thing. Found a neat "feature" and want to report it. Have tried contact form on their site, emails to IT staff I've enumerated, even tried messaging employees on LinkedIn. Maybe the WHOIS contact will work.
New Chrome App-Bound Encryption Decryption, centered on a new evasion paradigm: Direct Syscall-Based Reflective Hollowing. 👻 Hollowing > Attaching: The entire injection workflow now targets CREATE_SUSPENDED processes. This gives uncontested control of the address space,…
I will be soon hiring a Senior Security Researcher. Pre-requisite: Strong knowledge in Active Directory, Entra ID, and doing security research, as well as willing to present the research at conferences.
Finally someone with really helpful recommendations. Much appreciated guys.
alert and recommendations viettelsecurity.com/microsoft-shar…
Blog for ToolShell Disclaimer: The content of this blog is provided for educational and informational purposes only. blog.viettelcybersecurity.com/sharepoint-too… #SharePoint #ToolShell
We updated our blog with expanded analysis and threat intelligence from newly observed activity by Storm-2603 leading to the deployment of Warlock ransomware. msft.it/6011s132J
This might be useful for enumerating the SaaS products companies use, but it was more of an exercise in seeing how many DNS patterns I could get public LLMs to generate. github.com/HackingLZ/saas…
We now have a (draft) @metasploit exploit module in the pull queue for the recent Microsoft SharePoint Server unauthenticated RCE zero-day (CVE-2025-53770), based on the in-the-wild exploit published a few days ago. Check it out here: github.com/rapid7/metaspl…
As promised, our #SharePoint adventure with CVE-2025-53770 and CVE-2025-53771, including payloads and vulnerability checker! blog.leakix.net/2025/07/using-…
Had an environment that after blocking access to toolpane.aspx, still works. While rotating keys broke the app. Maybe a viable option to block it in front of your SP or even do it via IIS Rewrite rules. Maybe interesting for <=SP2013 users to go online without a patch.
Update on the SharePoint saga: First samples seen bypassing AMSI (lnkd.in/eTC9UWPM) Fist samples seen completely operating fileless, still extracting your machine keys. Please do not rely on AMSI nor that files need to be dropped first before shit happens.

Just a heads-up, attackers found a way to leak information, including keys entirely from memory. Checking for "the file" is not enough to assess compromise and warrant key rotation anymore. Just rotate your keys if you were exposed, period.
sharepoint.pwned.json gist.github.com/gboddin/bf6ff3…
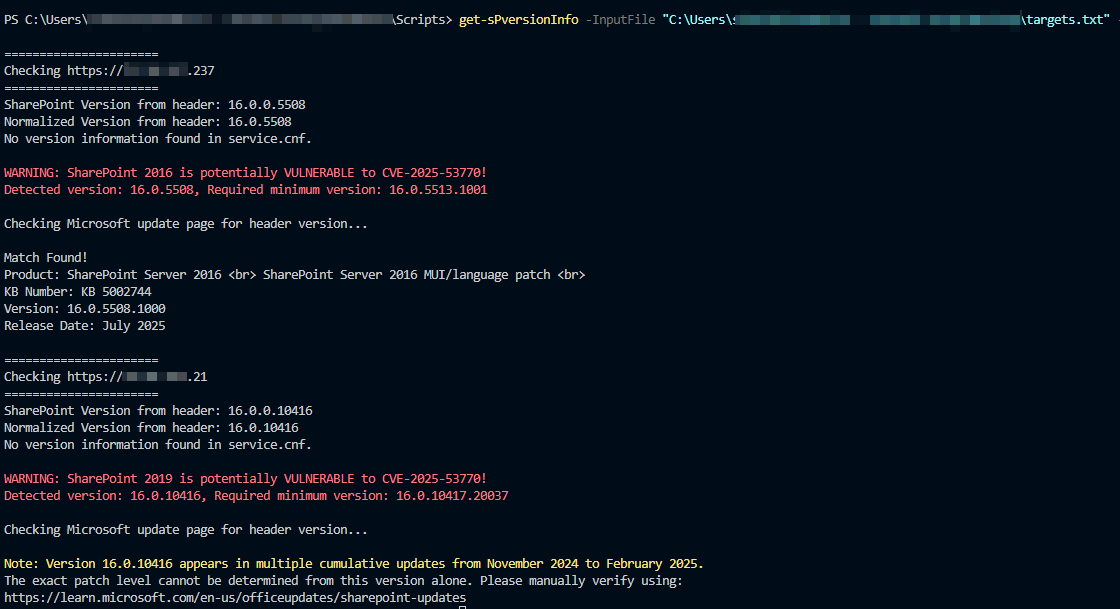
Added ToolChain check. Reliably works for 2016, partly works for 2019 and Subscription as sometimes only Revision numbers change. Anyways, it is still a first indicator if you see a patch status of January 2025. Added batch support and range support. github.com/LuemmelSec/Pen…
Why the fuck was / is MS not mentioning to protect the ToolPane.aspx endpoint at all? Wouldn't that help? Is this breaking fundamental things in SP if it's not externally available? I mean "people" will now patchdiff a lot. Maybe find bypasses and the shitshow starts all over.
