
Janggggg
@testanull
Kẻ soi mói, Re-searcher @dfsec_com
testbnull.medium.com/no-one-thing-w… A nasty hack to save your exiled server from being pwn Not a recommended way, but it can save your work sometime Have a good read!

Viettel Cyber Security Press Release for Customer alert, Latest research and Recommendations. Blog is comming viettelsecurity.com/microsoft-shar… #SharePoint #ToolShell
My research on CVE-2025-49113 is out. fearsoff.org/research/round…. Happy reading! #CVE #roundcube #poc @FearsOff
A new @rapid7 Analysis of CVE-2024-58136 was just published to AttackerKB, courtesy of Calum Hutton 🔥 Affecting the Yii framework, this analysis details the root cause and how it can be leveraged for RCE via a dirty file write to a log file: attackerkb.com/topics/U2Ddokj…
Outstanding! Nguyen Hoang Thach (@hi_im_d4rkn3ss) of STARLabs SG used a single integer overflow to exploit #VMware ESXi - a first in #Pwn2Own history. He earns $150,000 and 15 Master of Pwn points. #P2OBerlin
w00t!! Dinh Ho Anh Khoa (@_l0gg) of Viettel Cyber Security needed two attempts, but he successfully demonstrated his exploit of #Microsoft SharePoint. If confirmed, he'll win $100,000 for his efforts. Off to the disclosure room! #Pwn2Own #P2OBerlin
Write-up cho bài đăng của anh @tuo4n8. Chuyện đã lâu rồi có nhiều thứ mình không còn nhớ. - No outbound Gadgets for CVE-2019-16891. - New JDBC attack chain. For English speakers, please use Google Translate. l0gg.substack.com/p/journey-into…
My new blog for Check Point Research - check it out! 💙 // #ProcessInjection : #WaitingThreadHijacking
Thread Execution Hijacking is one of the well-known methods that can be used to run implanted code. In this blog we introduce a new injection method, that is based on this classic technique, but much stealthier - Waiting Thread Hijacking. Read More : research.checkpoint.com/2025/waiting-t…
Poc for 35587 btw,
Retweet due to so many people asked for the gadgetchain of CVE-2021-35587 in OAM 10g, The step to reproduce it has already been provided in section "Universal gadget chain for 10.3.x" Detail: peterjson.medium.com/miracle-one-vu…
They deserved this :) Responsible disclosure is a joke!
So, rose87168 said he used CVE-2021-35587 to compromise the login[.]us2[.]oraclecloud[.]com server. Oracle then denied the attack and remains silent but quickly disconnected the server from the Internet (probably to investigate? also unknown). The problem is that Oracle has, at…
testbnull.medium.com/bypass-gitlab-… A quick note while analyzing CVE-2025-25291 gitlab saml auth bypass
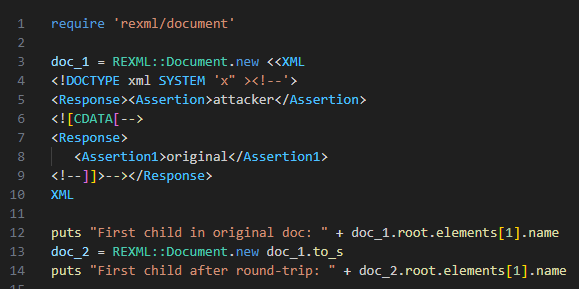
You might have noticed that the recent SAML writeups omit some crucial details. In "SAML roulette: the hacker always wins", we share everything you need to know for a complete unauthenticated exploit on ruby-saml, using GitLab as a case-study. portswigger.net/research/saml-…
🥳The latest !exploitable is here! We're sharing all the joy that comes with exploiting an arbitrary file write in GitLab, while cruising the Mediterranean. 🚢 Everything from onerous configurations to spotty internet! Enjoy! #doyensec #appsec #security blog.doyensec.com/2025/03/18/exp…
A few notes learnt while working with patch diffing! Hope it can help everyone working in this field! 👉 testbnull.medium.com/a-quick-note-o…
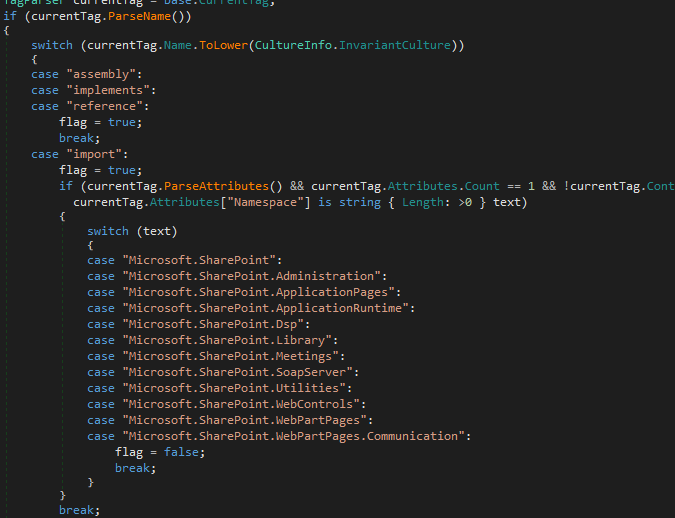
Just finished my writeup about CVE-2025-23369, an interesting SAML authentication bypass on GitHub Enterprise Server I reported last year. you can read about it here: repzret.blogspot.com/2025/02/abusin…
sec.vnpt.vn/2025/01/canh-b… A full chained Pre-Auth RCE on WSO2 Identity Manager and API Manager with default config by my old colleague. Do something before it’s getting burned 🔥
If you are using YSoSerial .Net, we have accepted a few PRs and patched several bugs & improved the ViewState plugin! Merry Christmas 🎅 github.com/pwntester/ysos… @pwntester
