
Renzon
@r3nzsec
IR/Forensics @Unit42_Intel | Co-Founder @guidemtraining | Contributor/Analyst @TheDFIRReport @XintraOrg | CTF member @_hackstreetboys
I recently co-authored a @Unit42_Intel blog about a unique IR case in which a threat actor’s custom EDR bypass (using #BYOVD) exposed their toolkit, methods, and even identity. Check out how we unmasked them through an opsec slip-up! #dfir unit42.paloaltonetworks.com/edr-bypass-ext…
Fantastic project that can be used to visualize your SOD!! Great stuff @Arimb00R! 🔥
🚀 **Kanvas** - my new open-source project !! If you're in IR, Forensics, or part of a SOC dealing with security incidents/ breaches, , Give it a spin and let me know what you think 🤞 Quick writeup 📌 findevil.io/Kanvas-page/ Github Repo 📌 github.com/WithSecureLabs…
Anyone going to SANS #dfirsummit in Salt Lake, Utah this week? See you all!! 🫶🏻

Attackers love RDP for sneaky lateral moves—but every pixel leaves a clue! 🕵️♂️ Check out my latest blog on tracking attackers through logs, bitmap caches, and clipboard trails (plus a printer tale too funny to miss). #DFIR #BlueTeam #CyberSecurity medium.com/@mathias.fuchs…
Become a contributor at XINTRA @XintraOrg 🔎 We're looking for RED and BLUE team contributors 🔴Red Team – Emulate real APT groups 🔵Blue Team – Investigate & respond to emulations What you get: - Challenging, realistic emulations - Hack & forensicate vendor devices -…
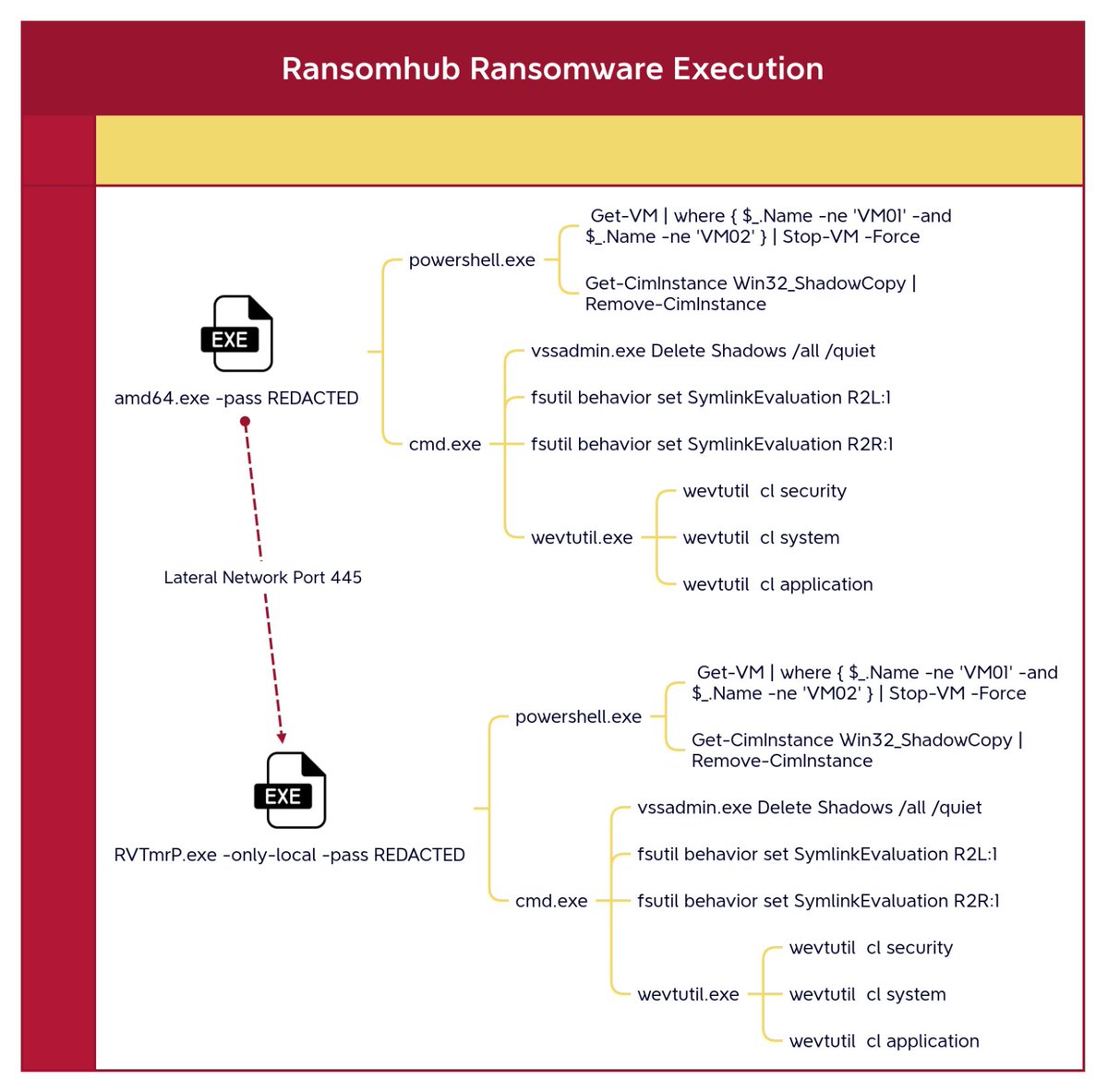
Classic #ransomhub execution baked into the encryptor itself. Check out the latest report here and learn how that exposed RDP on your network can trigger a massive ransomware attack. #dfir thedfirreport.com/2025/06/30/hid… @TheDFIRReport
AMAZING keynote coming up at the @SANSInstitute | @sansforensics #RansomwareSummit 2025! @TheDFIRReport's @_pete_0 & @angelo_violetti are presenting "Adapting Tradecraft: Examining #Ransomware Attacks in 2024 - Insights from The DFIR Report"! FREE reg @: sans.org/u/1yCa
🌟New report out today!🌟 Another Confluence Bites the Dust: Falling to ELPACO-team Ransomware Analysis and reporting completed by @pcsc0ut.bsky.social, @irishdeath.bsky.social & @0xtornado 🔊Audio: Available on Spotify, Apple, YouTube and more! thedfirreport.com/2025/05/19/ano…
The Active Directory Project 2.0 is fully released! For those wanting to get some hands on practice, feel free to follow along and learn how to setup your own AD/Splunk environment and create an automation & response workflow in Shuffle. Cybersecurity Project: Active Directory…
Unit 42 researchers uncovered a Lampion malware campaign targeting Portuguese government, finance & transport sectors. The threat actor aims to steal sensitive banking info, has impacted dozens of organizations & now has added ClickFix lures to its arsenal unit42.paloaltonetworks.com/lampion-malwar…
Fortinet dropped an APT34 report just days after we launched our APT34/OilRig lab: fortinet.com/content/dam/fo… Our emulation covers the exact TTPs: ✔️ Kernel elevation ✔️ Malicious JS payloads ✔️ Password Filter DLL ✔️ In-memory keyloggers Try it yourself 👉…
NEW LAB: Abu Jibal (APT34 / OilRig) 🔍💻 Iranian APT34 targets the oil and gas sector across the Middle East. Test your blue team skills on: 👀 Password Filter DLL Attacks 👀 RunPE In-Memory Execution 👀 Windows Kernel Elevation 👀 Malicious JavaScript Payloads 👀 Custom…
🫶🏻
Back in the day, when people asked me how to get into Threat Intel or IR, I always said: read APT reports! The real ones. Not the fluffy exec summaries. Digest what these actors actually do. Replicate stuff. Spot patterns. Build mental TTP maps. Because back then, all we had…
Check this out! #APT34 @XintraOrg
NEW LAB: Abu Jibal (APT34 / OilRig) 🔍💻 Iranian APT34 targets the oil and gas sector across the Middle East. Test your blue team skills on: 👀 Password Filter DLL Attacks 👀 RunPE In-Memory Execution 👀 Windows Kernel Elevation 👀 Malicious JavaScript Payloads 👀 Custom…
This is really bad. We’re not talking home users or mom-and-pop shops here - the systems affected are the backbone of major companies and orgs. People started scanning for helper.jsp and cache.jsp and found almost 600 compromised servers within hours. Big names among them. Tried…
This is a serious problem I processed this report with IOCs today: reliaquest.com/blog/threat-sp…
I’m so proud on all the folks at @XintraOrg - They work incredibly hard to put out quality content! If you’re looking for useful courses or training. Xintra is a great choice!
Feedback we received this week on courses and labs 😍 Happy Easter everyone! New lab coming in a few days!


