Abdulkadir | Cybersecurity
@cyber_razz
Purple Teamer | InfoSec |Documenting My Journey into Cybersecurity & I Post Educative Content relating to IT(it) | Turn on Post Notis 🔔
Cybersecurity Roadmap: Step-by-Step Guide for Aspiring Professionals Embarking on a cybersecurity journey can be challenging, but with the right plan, you can progress steadily and achieve your goals. Based on my personal journey as a penetration tester in training, here’s a…
✅ Correct Answer: B) DNS server is down Explanation: •The user can ping internal IPs, so physical connectivity and local routing are working fine. •But since the user can’t connect to websites, which rely on domain names, it’s a DNS issue. •If the DNS server is down or…
Networking Knowledge Checkpoint A network technician receives a report that a user cannot connect to any websites, but can ping internal IP addresses such as 192.168.1.1. What is the most likely cause? A) Default gateway is unreachable B) DNS server is down C) Network cable is…
🧵 T1003.001 – OS Credential Dumping: LSASS Memory Let me show you how I built a robust detection rule to catch attackers trying to dump LSASS memory often used for credential theft. @ireteeh @cyber_rekk @segoslavia @TemitopeSobulo @cyber_razz @Omotafede
Networking Knowledge Checkpoint A network technician receives a report that a user cannot connect to any websites, but can ping internal IP addresses such as 192.168.1.1. What is the most likely cause? A) Default gateway is unreachable B) DNS server is down C) Network cable is…
Aaaah na now I dey wake ooo
NEPO babies don dey sleep 😌
Networking Knowledge Checkpoint You’re given the IP block 192.168.10.0/24 and need to create 5 subnets with at least 30 usable host addresses each. Which subnet mask should you use? A) /25 B) /26 C) /27 D) /28
You don_meannit
Cybersecurity Una...!! I don leave una run for now boss I think say Kali Linux dey chop my data until I jam burp suite. Lemme use crypto and accumulate funds for starlink first.
✅ Correct Answer: C) Mandatory Access Control (MAC) Explanation: •MAC (Mandatory Access Control) is used in environments requiring strict access controls based on classifications (like in military or government systems). •Users cannot change permissions; access is determined…
Security+ Knowledge Checkpoint Which access control model enforces access based on security labels such as “Confidential” or “Top Secret” and cannot be changed by users? A) Discretionary Access Control (DAC) B) Role-Based Access Control (RBAC) C) Mandatory Access Control (MAC)…
To stay afloat in your cybersecurity journey you’d need an alternate source of income What is yours ?
Security+ Knowledge Checkpoint Which access control model enforces access based on security labels such as “Confidential” or “Top Secret” and cannot be changed by users? A) Discretionary Access Control (DAC) B) Role-Based Access Control (RBAC) C) Mandatory Access Control (MAC)…
1.2 billion views
Share a piece of lore about yourself
Wireshack Metasploit Metasploitable
what’s ‘the big 3’
You see I’ve been saying this
Nah heartbreak drive me reach my breakthrough better have yours today, you may just become the richest person ever
I’m healed now I need another short medical student with a beautiful smile to redo the work My motivation’s low again
The motivation that comes fresh off a heartbreak >>>>>>>
Ramdon thought How does one get his existence in Wikipedia?
Work rate increased by 100 😩😂
The motivation that comes fresh off a heartbreak >>>>>>>
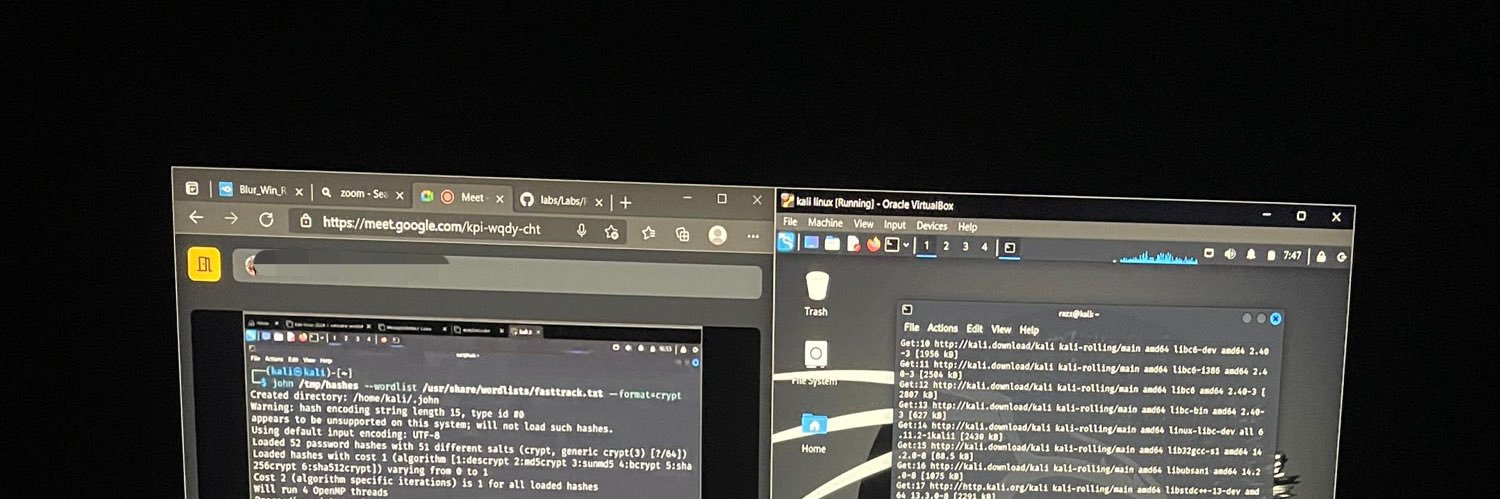
My laptop Spec for those asking I can run 3-4 machines on it without experiencing any lag
This is for those asking about my laptop spec This would run perfectly for anything cybersecurity A slightly lower spec would do too & obviously anything higher would be way better


