![[email protected] / PurpleLabs / EDRmetry's banner](https://pbs.twimg.com/profile_banners/335283366/1447324478)
[email protected] / PurpleLabs / EDRmetry
@cr0nym
Focus on Linux/Kubernetes Attack/Detection/Forensics/Incident Response/Threat Hunting. Active Defense. PurpleLabs Cyber Range. Learning hard every single day.
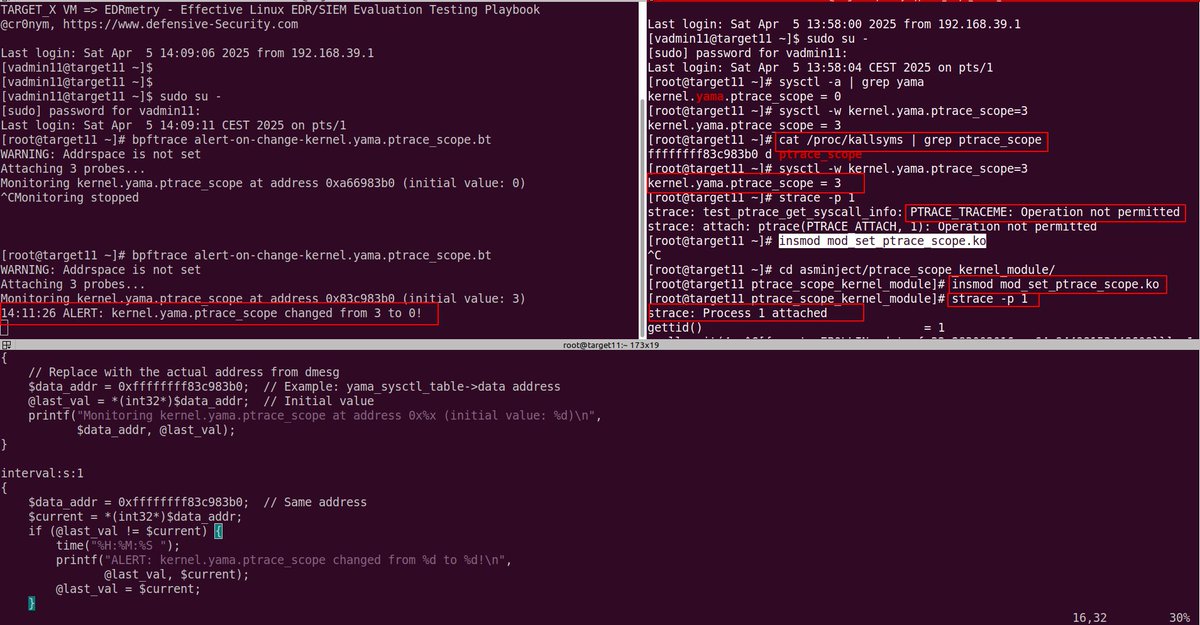
My short blog post about detecting in-memory modification of Linux kernel.yama.ptrace_scope with bpftrace edu.defensive-security.com/blog/detecting…
EDR is rmm on steroids
EDR-on-EDR Violence 1/🧵 @BushidoToken called out that EDR products were being abused by threat actors. @Shammahwoods & I realized a free trial of an attacker controlled EDR can be used to kill the existing EDR. @techspence @UK_Daniel_Card @Jhaddix github.com/CroodSolutions…
Yet another bloodhound ingestor for Linux based system and using ADWS as the main interface. Built with @Sant0rryu , meet github.com/j4s0nmo0n/Soap…. You may check out the short blog post for more details. j4s0nmo0n.github.io/belettetimoree…
EDR-on-EDR Violence 1/🧵 @BushidoToken called out that EDR products were being abused by threat actors. @Shammahwoods & I realized a free trial of an attacker controlled EDR can be used to kill the existing EDR. @techspence @UK_Daniel_Card @Jhaddix github.com/CroodSolutions…
Reforging Sliver: How Simple Code Edits Can Outmaneuver EDR fortbridge.co.uk/research/refor…
New website of Linux EDRmetry Pulse is Live! I hope that the proposed approach and values are clear 🩵❤️✌️ check it out here: defensive-security.com/edrmetry/
EDRmetry Pulse - first demo published 🔥EDRmetry Pulse is a user-friendly, automated tool for simulating adversary behavior on corporate #Linux networks. It enables cybersecurity professionals to test Linux telemetry collection, evaluate detection capabilities, verify security…
For those like me who prefer to stay in the terminal and want to call REST APIs like the Microsoft Graph without complicated commands or copy/pasting tokens: roadtx now has a graphrequest command to perform simple requests against these APIs and parse the JSON.
A few weeks ago, I was responding to a cybersecurity incident - $500,000 have been stolen from a #blockchain developer. The infected operating system was freshly installed, and the victim was vigilant about cybersecurity. How could this happen? New supply chain attack? [1/6]
Kind of C2 over EDR :-)
1. cloud.google.com/blog/topics/th… 2. aon.com/en/insights/cy… 3. securelist.com/miner-campaign…
230k GPUs, including 30k GB200s, are operational for training Grok @xAI in a single supercluster called Colossus 1 (inference is done by our cloud providers). At Colossus 2, the first batch of 550k GB200s & GB300s, also for training, start going online in a few weeks. As Jensen…
Nvidia CEO Jensen Huang on Elon Musk and @xAI “Never been done before – xAI did in 19 days what everyone else needs one year to accomplish. That is superhuman – There's only one person in the world who could do that – Elon Musk is singular in his understanding of engineering.”
My CISO wants me to force my employees to get a security certification so I'm getting them all TLS certificates from letsencrypt Checked the checkbox, boss
RingReaper can easily bypass Linux Sophos EDR. src: github.com/MatheuZSecurit… Currently, using this technique is FUD against (what I've tested); - TrendMicro EDR - Cortex XDR - Sophos EDR #ringreaper #io_uring #malware #c2 #poc #edr
Another quck and dirty Linux hunt for Velocriaptor. 🔎 LD_PRELOAD is well known technique to hijack execution flow and inject malicious code into every dynamically linked process. ATT&CK - attack.mitre.org/techniques/T15… Linux.Persistence.LdPreload - docs.velociraptor.app/exchange/artif… 1. Parses…
Capturing passwords from Password Managers via a BOF without using CTRL+C... Successfully tested on 1Password and KeePass.
I'm very excited about where this is going 😍 EDRmetry Pulse: Defense Evasion/EDR-T6188 Sliver C2 MTLS Fileless Execution with PERL memexec #linux youtube.com/watch?v=1Tmlu7…
EDRmetry Pulse - first demo published 🔥EDRmetry Pulse is a user-friendly, automated tool for simulating adversary behavior on corporate #Linux networks. It enables cybersecurity professionals to test Linux telemetry collection, evaluate detection capabilities, verify security…
When I was saying you can put basically anything in splunk I meant it. I do all of my memory analysis using a custom search command (in python) that automatically runs all volatility plugins and outputs the results back to an index.
Linux bpftrace MCP Server: generate eBPF to trace linux kernel 🔥🔥 github.com/eunomia-bpf/MC…

We found a new container escape affecting all container runtimes using @NVIDIA GPUs. The crazy part? The exploit is just three lines long 🤯 This is the story of #NVIDIAScape 🧵👇
Quick and dirty kernel module hunt for Velocriaptor. 🔎 Linux.Sys.Modinfo - docs.velociraptor.app/exchange/artif… 1. Enumerate loaded modules at /proc/modules 2. Run modinfo to enumerate details 3. Kernel events in Journal Files #dfir @velocidex