db
@whokilleddb
Maldev @bhinfosecurity | Opinions my own | Politics | Maths | Computers | Arts
It's actually pretty easy to evade floss even on single byte XOR obfuscation functions by doing as little as adding a single line of code. I want to write a blog on the bypass but the FLOSS internals looks complicated 😵💫 If anyone knows how to make vivisect work, hmu please 🙏
FLOSS v1.7.0 released to deobfuscate strings found in malware. Dev ramping back up. Share your ideas and/or issues! github.com/fireeye/flare-…
Gonna work my way through GOAD to relearn AD and maybe create a write up and some custom tools. Wish me luck.
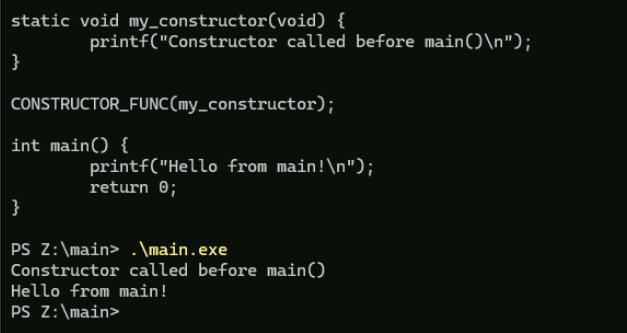
Saw someone analysing malware setting a breakpoint at `main()` instead of something like $exentry or `mainCRTStartup()` and to that I say - heard of ✨constructors✨ in C/Cpp? gist.github.com/whokilleddb/db…
Doing a Toolshed talk about something really cool and customisable for Red Teams ;) Sign up today folks.
Behold the threats. Beware the breaches. Believe in the defenses. The gate is now open to Wild West Hackin' Fest @ Mile High 2026! Grab yer tickets today! wildwesthackinfest.com/wild-west-hack…
"Proof or did not happen" gist.github.com/whokilleddb/14… The trick? Just insert a `RDSEED rax` instruction in there to throw off the program ;)
It's actually pretty easy to evade floss even on single byte XOR obfuscation functions by doing as little as adding a single line of code. I want to write a blog on the bypass but the FLOSS internals looks complicated 😵💫 If anyone knows how to make vivisect work, hmu please 🙏
Been seeing this LinkedIn slop of late: > Someone talks about a SuperSecretEDRKiller they built > Looks inside > Its just a driver > Requires Test Signing > Requires System Reboot > Tested against: Normal Defender

Been thinking about this for a while and realised that I technically the Function Fluctuation technique can be used to do almost the same stuff minus the "overwrite previously executed stub" part. Maybe I will implement that next. Ref: github.com/whokilleddb/fu…
chinese.polymorphic.shellcode.
Research published. Its almost 6am. The sun is rising. Weekend is here chaps. Gonna read some Gabriel Garcia Marquez. Here is a poem for anyone who might want to read one: poetryfoundation.org/poems/53219/ma…

Published a blog/repo inspired by one of @MDSecLabs's research on VSCode extensions. In this repo, we put Rust and Javascript together and backdoor a popular microsoft extension while preserving the blue checkmark and all. Read more here: github.com/whokilleddb/si…
One of these is malicious. One of these is not. Blog coming soon.
People who work in cybersecurity, how do you all deal with stress?
People who work in cybersecurity, how do you all deal with stress?
I hate how poorly dotnet is documented for Linux (or cross compilation) - you want to do something and the only ancient wisdom guiding your way is a half baked article from 2021 written in russian.
Just released a small project to create multi-bitness x86 shellcode :) github.com/winterknife/EV… Starting bytes as decoded by an x86 processor in IA-32 mode vs. IA-32e mode.
C2 friendly fork of @NetSPI's EvilSqlClient project which you can run from the comfort of your fav Command-and-Control framework github.com/whokilleddb/ES…

Published a little technique where we take a page out of Shellcode fluctuations and apply it to functions to have a program's functionality hidden during runtime. github.com/whokilleddb/fu…