Xappy
@theXappy
Security Researcher 🩺 Into Windows(.NET)/iOS/protocols reversing and forensics.
I figured out a generic way to generate those polyglots! Introducing: bppb! github.com/theXappy/bppb This PoC takes 2 files, a bplist and a protobuf, and merges them into one unholy abomination. #bplist #protobuf #polyglot #dfir #digitalforensics
Annoyingly, I created a bplist-protobuf polyglot. This one is a valid protobuf containing 2 LengthValues in an array. As a bplist, it's a dictionary with 2 Key-Value-Pairs. Hex here: pastebin.com/d4Vva8aV #DFIR #MobileForensics #DigitalForensics
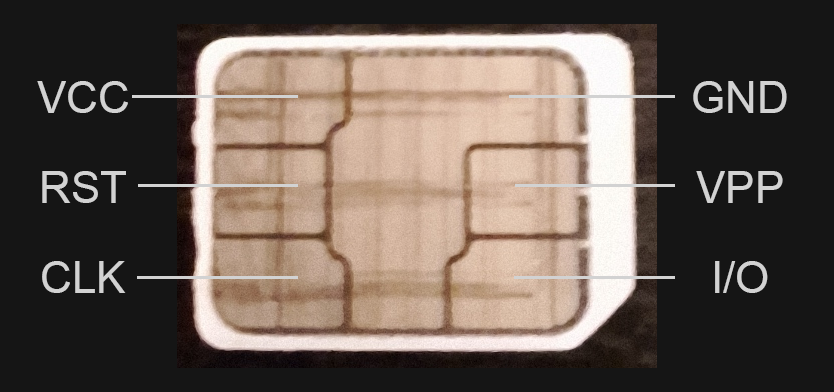
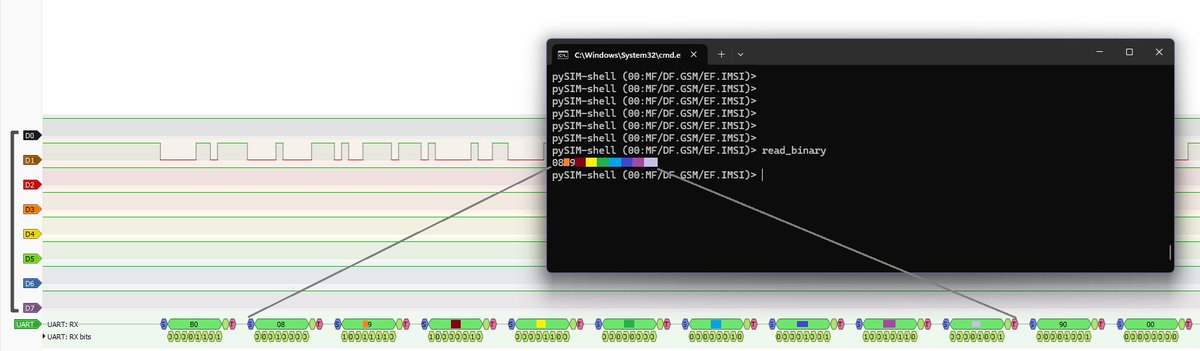
Ever wondered what your modem really says to your SIM card? I sniffed raw APDU traffic off the SIM pins, decoded the UART based on the ATR, and piped it into Wireshark. Full guide: how to wire it, decode it, and see the bytes for yourself. 🔎💥📶 github.com/theXappy/trace…


stuxnet on its way to make some spinny things spin faster
𝙽𝚎𝚝 𝚁𝚒𝚍𝚎𝚛 𝙸𝙸 🪱🌵🏜️✨💫🌟
Centralized resource for listing and organizing known injection techniques and POCs #malware #dfir github.com/itaymigdal/awe…
After #flareon11 challenge 7, I got inspired to build tooling for #dotnet Native AOT reverse engineering. As such, I built a #Ghidra Analyzer that can automatically recover most .NET types, methods and frozen objects (e.g., strings). Blog:👉blog.washi.dev/posts/recoveri…
Adding to my ETW research toolkit, a tiny program to consume information from a provider with as little overhead as possible. PockETWatcher, a tool to get the essential information from a ETW provider to the CLI or a JSON file github.com/olafhartong/Po…
Or is it Apple delaying patch of actively exploited kernel bugs, as usual