pygrum
@spygrum
opinions are not my own, im being controlled
First time sharing progress on something I've been developing since the start of the year - a C2 framework with a focus on modularity. Keen to hear suggestions on features, ideas, research to implement - bearing in mind its at an early development stage
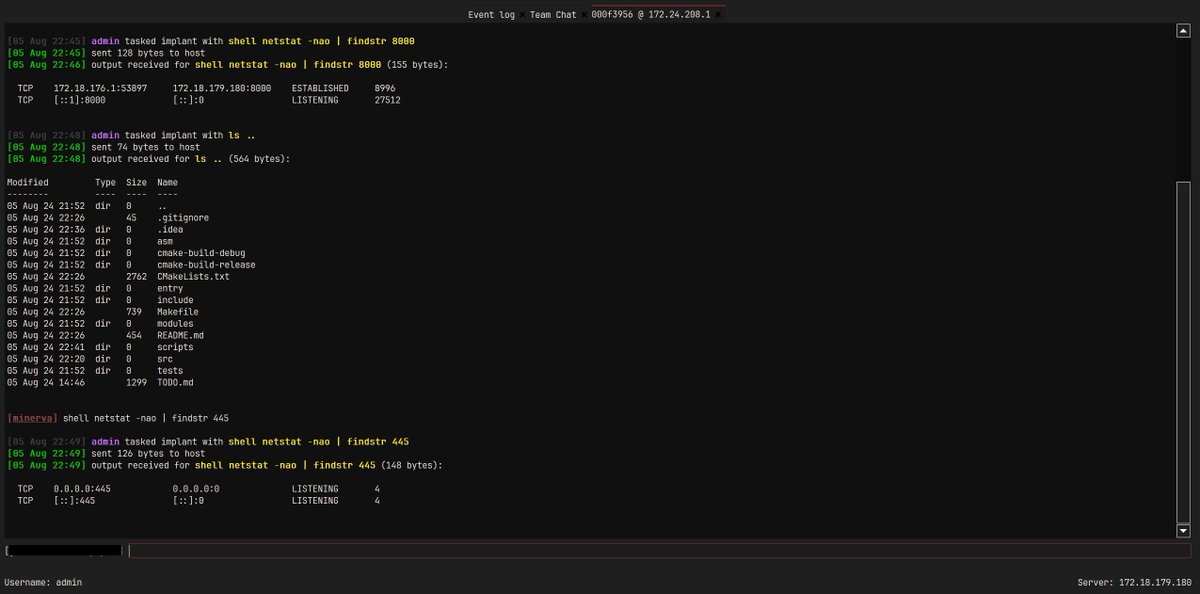
I've most recently added liveness info for registers / flags. No more pushf / popf pairs to make things a bit harder for analysts \( -_-)/ github.com/badhive/stitch
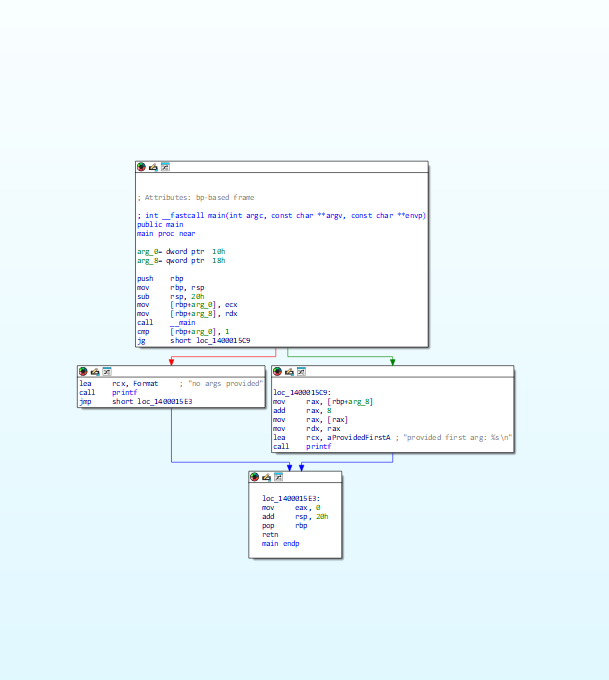
Wrote a cross-platform library for rewriting / modifying code in executable files on a function level. Pretty simple to write advanced binary obfuscators using it. github.com/badhive/stitch Below shows what ~30 LOC using Stitch transforms a function into:
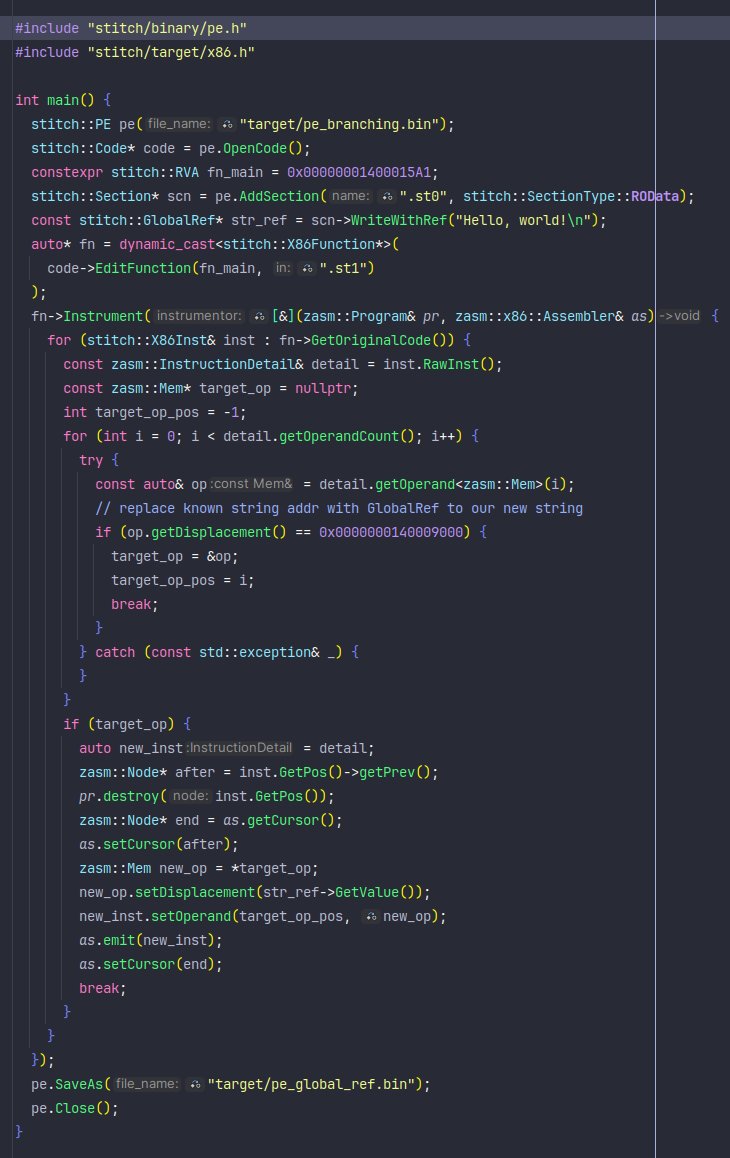
You can use stitch's GlobalRefs to write arbitrary data to sections and reference them in the same or later sections - github.com/badhive/stitch. Here's some code replacing a known string with a GlobalRef to my own:
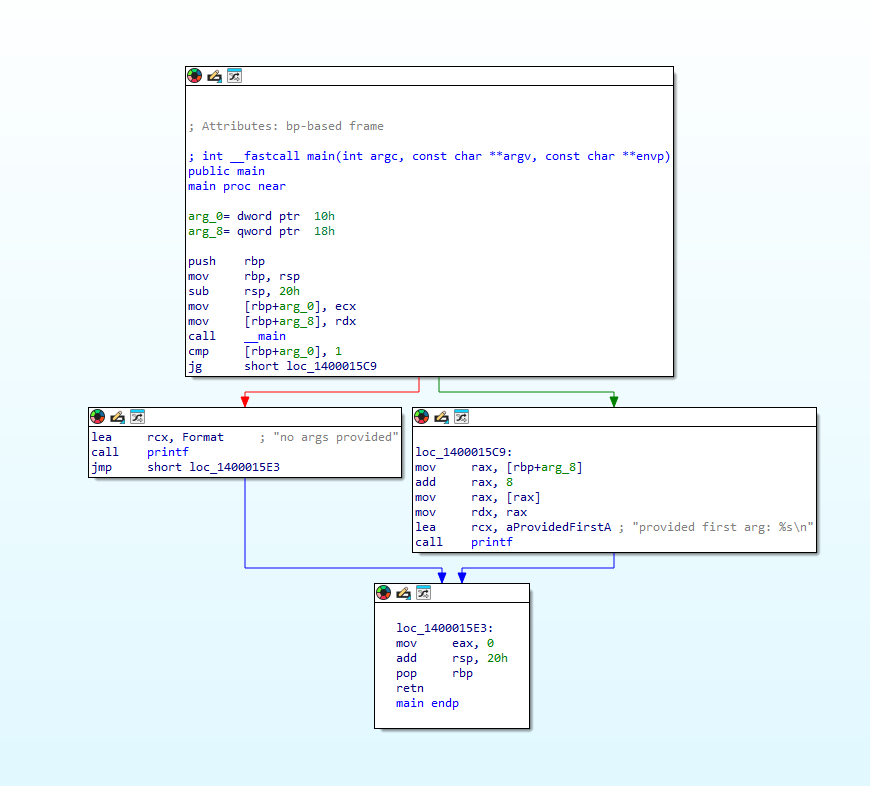

Wrote a cross-platform library for rewriting / modifying code in executable files on a function level. Pretty simple to write advanced binary obfuscators using it. github.com/badhive/stitch Below shows what ~30 LOC using Stitch transforms a function into:

I've finished most of the development for Governor, the flagship Windows 'sensor' / telemetry source for the ALCA engine. Governor can now be used alongside ALCA for dynamic signaturing of Windows malware github.com/badhive/alca github.com/badhive/govern…
Been working on a rule engine for dynamic malware analysis - ingests telemetry from a 'sensor' and runs rules and sequences of rules on event data it receives. Currently writing the flagship sensor, but the library itself is available to experiment with: github.com/badhive/alca

Gimmick - an in-memory payload obfuscation technique & POC via thread-safe, on-demand section decryption github.com/pygrum/gimmick