vmprotect
@setThreatTitle
ACR Stealer acrstealer[.]top justlittleluxuriedrs[.]shop longstoryshortdesigndes[.]shop magneticcitizen[.]shop 116.202.44.220 83.147.255.219
![setThreatTitle's tweet image. ACR Stealer
acrstealer[.]top
justlittleluxuriedrs[.]shop
longstoryshortdesigndes[.]shop
magneticcitizen[.]shop
116.202.44.220
83.147.255.219](https://pbs.twimg.com/media/GwkTyHjXAAA1fzB.jpg)
hi threat hunters and malware analysts! I’ve shared my new C2 hunting, reporting, and visualization tool, "Keklick," on github! It helps you discover and manage potential domains/IPs related to C2 infrastructure. Happy hunting! keklick: github.com/0x6rss/keklick
Expading your hunting with domainhunter.pro craxs-rat-seller[.]xyz craxs-rat[.]com craxsrat[.]work craxsratbuy[.]store craxstore[.]shop craxsahnesi[.]xxx craxsratandroid[.]com craxs-rat-selller[.]com craxsrat-craxs-rat[.]com avscraxs[.]xyz craxsrat[.]sbs craxsrat[.]org…
CraxsRAT Panels: craxsrat7[.]com craxsrat8[.]com craxs-rat[.]shop craxsrat[.]info craxsrat[.]club craxsrat9[.]shop craxsrat8[.]shop craxsrat7[.]shop craxsrat[.]cfd craxsrat[.]buzz craxsrats[.]vip craxsrat[.]live craxsrat[.]life @500mk500 @ViriBack #CraxsRAT #Panels #CTI
Brazil was among the top targets of IconAds, a large-scale mobile ad fraud campaign that abused 350+ Android apps to serve hidden, out-of-context ads. Android ad fraud is getting stealthier, layered obfuscation, icon cloaking, and runtime DEX loading are the new normal.
HUMAN's Satori team uncovered and disrupted IconAds, a massive mobile ad fraud scheme involving 352 Android apps. These stealthy apps hid icons & loaded ads out-of-context, peaking at 1.2B ad bid requests/day. Main targets: 🇧🇷 Brazil, 🇲🇽 Mexico, 🇺🇸 U.S. humansecurity.com/learn/blog/sat…
A recent phishing campaign is abusing the Anydesk brand: anydesktenewo[.]com anydeskxxvvza[.]top anydeskxxvvzb[.]top anydeskxxvvzc[.]top anydeskxxvvzd[.]top anydeskxxvvzm[.]top anydeskxxvvzn[.]top anydeskxxvvzs[.]top anydeskxxvvzv[.]top anydeskxxvvzx[.]top anydeskxxvvzz[.]top…
![setThreatTitle's tweet image. A recent phishing campaign is abusing the Anydesk brand:
anydesktenewo[.]com
anydeskxxvvza[.]top
anydeskxxvvzb[.]top
anydeskxxvvzc[.]top
anydeskxxvvzd[.]top
anydeskxxvvzm[.]top
anydeskxxvvzn[.]top
anydeskxxvvzs[.]top
anydeskxxvvzv[.]top
anydeskxxvvzx[.]top
anydeskxxvvzz[.]top…](https://pbs.twimg.com/media/Gu8PUCPWwAADJZE.jpg)
![setThreatTitle's tweet image. A recent phishing campaign is abusing the Anydesk brand:
anydesktenewo[.]com
anydeskxxvvza[.]top
anydeskxxvvzb[.]top
anydeskxxvvzc[.]top
anydeskxxvvzd[.]top
anydeskxxvvzm[.]top
anydeskxxvvzn[.]top
anydeskxxvvzs[.]top
anydeskxxvvzv[.]top
anydeskxxvvzx[.]top
anydeskxxvvzz[.]top…](https://pbs.twimg.com/media/Gu8QOxdXsAAcOGs.png)
Recent domains for fake @GooglePlay googleplayasd[.]com googleplaybhj[.]com googleplayct[.]com googleplaycvb[.]com googleplaydyh[.]com googleplayfgh[.]com googleplaygd[.]com googleplayiop[.]com googleplayja[.]com googleplayjkl[.]com googleplayjp[.]com googleplaykhg[.]com…
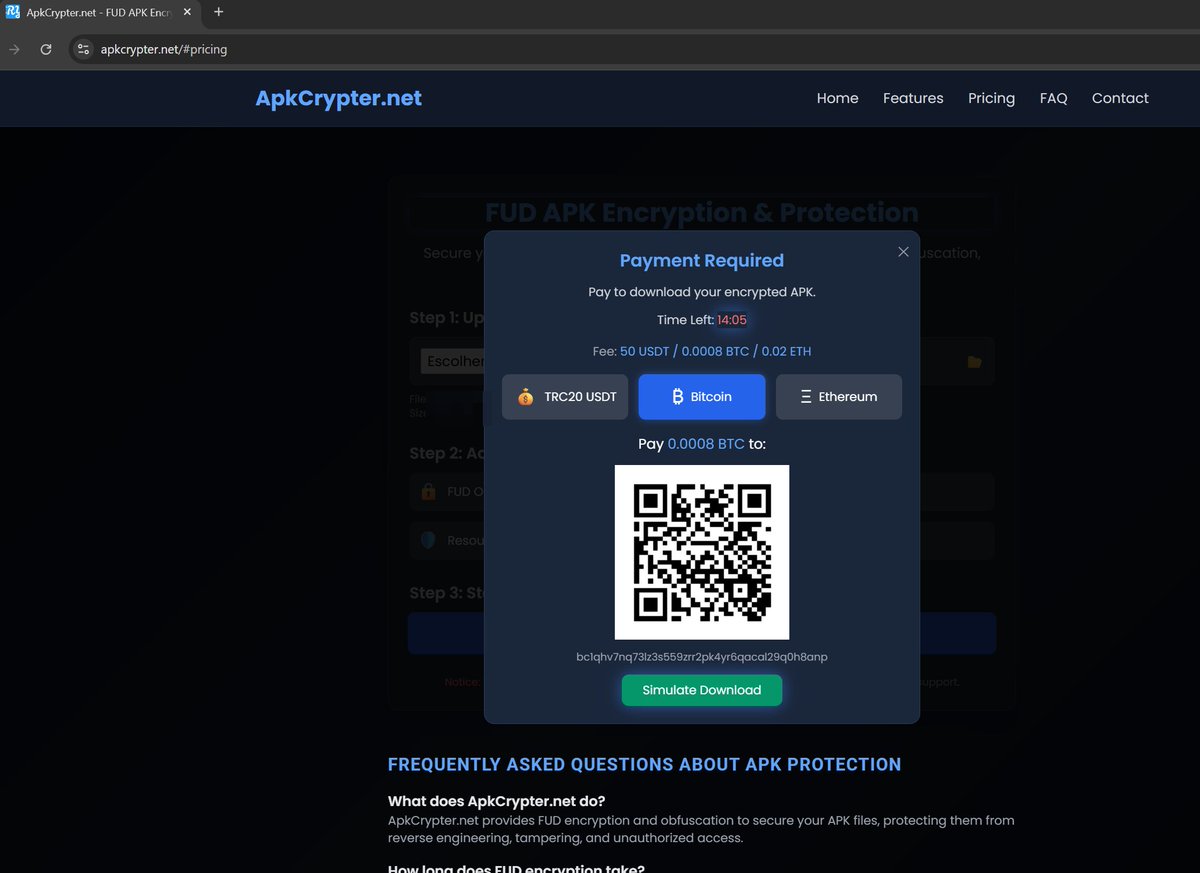
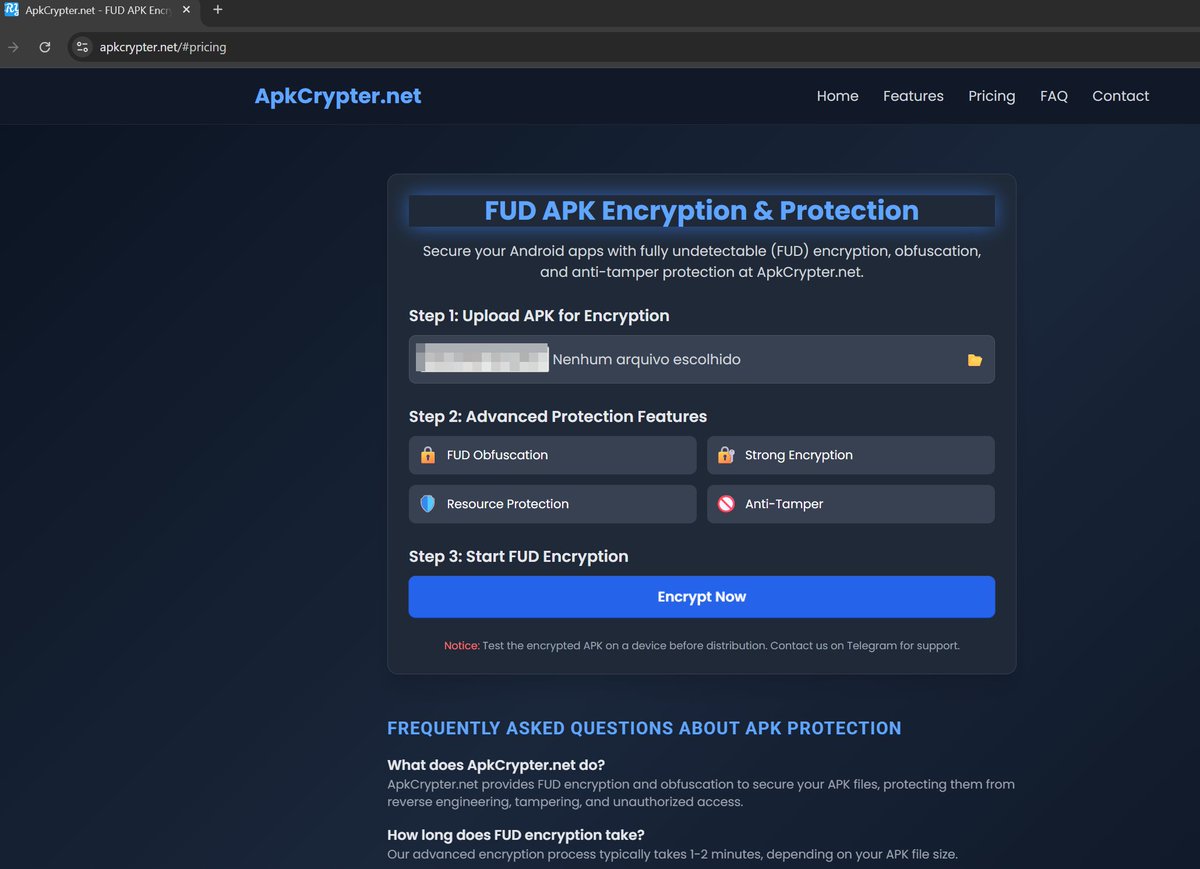
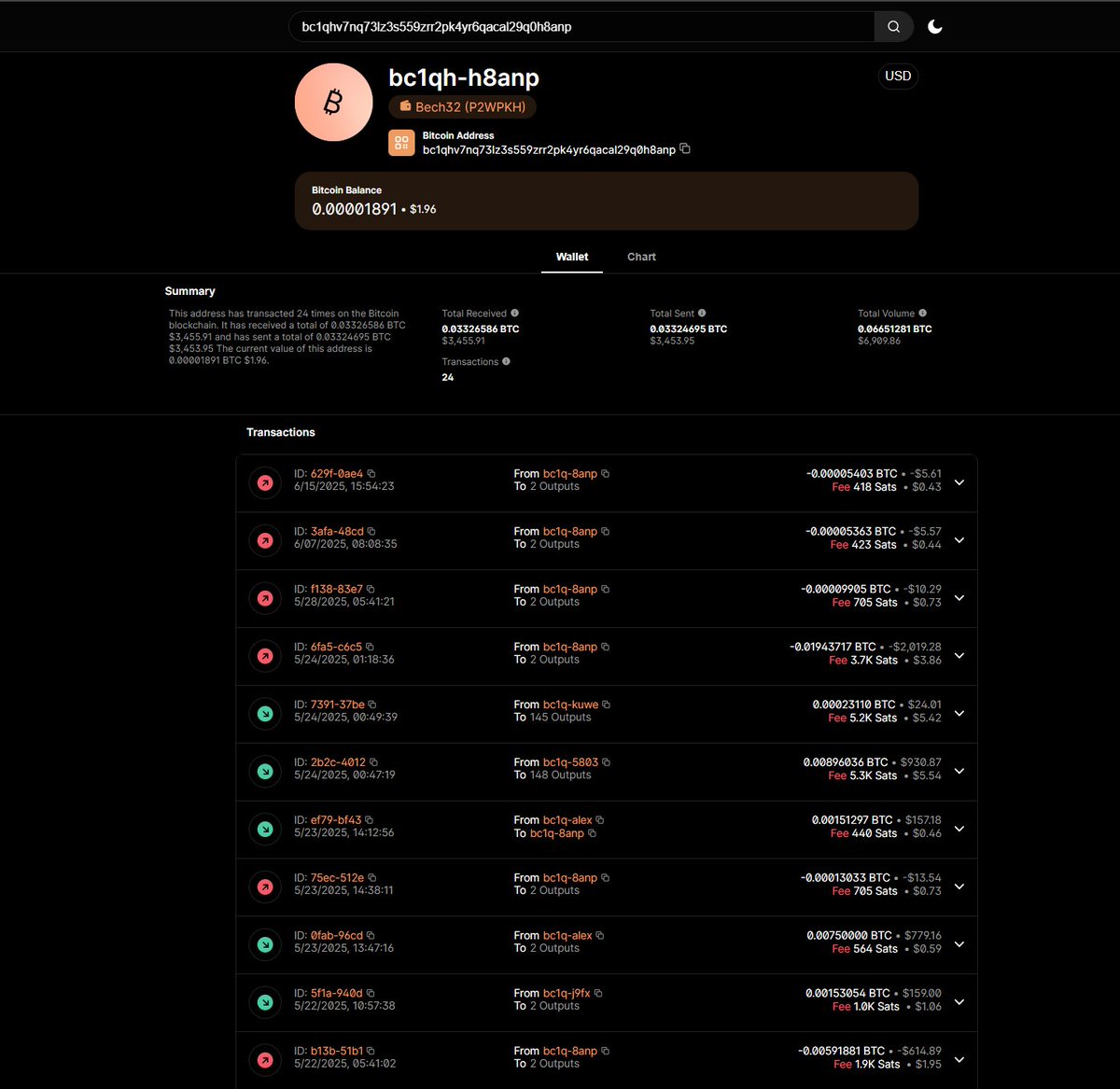
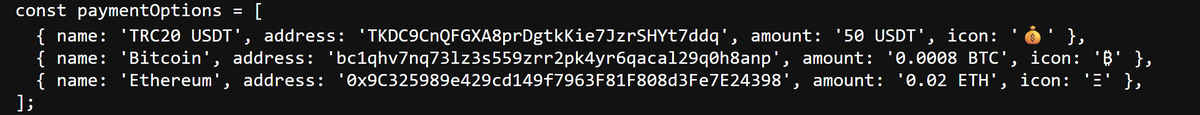
hxxps://apkcrypter.net (Advanced Malware Crypter) Suspicious wallets: 'Bitcoin', address: 'bc1qhv7nq73lz3s559zrr2pk4yr6qacal29q0h8anp 'Ethereum', address: '0x9C325989e429cd149f7963F81F808d3Fe7E24398 'TRC20 USDT', address: 'TKDC9CnQFGXA8prDgtkKie7JzrSHYt7ddq