Scanner
@scanner_dev
Scanner makes data lakes fast and easy to use, giving teams more detection and response power. Schemaless log search indexing, all in the user’s S3 buckets.
Big news: Scanner.dev is hitting the stage at @BlueTeamCon 2025 Cliff’s heading to Chicago this Sept to talk AI + SecOps — specifically, how modern security teams can boost productivity without burning out. Let’s connect IRL: 🔗 blueteamcon.com/directory/ai-a…

Legacy SIEMs: all noise, no signal. Scanner: built for teams who actually want to fix things. - 1,000s of useless alerts? Nope. - Context first. Triage in seconds. That’s why @tryramp, @getpostman & @Lemonade_Inc ditched the bloat. 🔗 blog.scanner.dev/why-fast-movin…

Resetting MFA at 3AM? Logging in from two continents in an hour? If it's in your Okta logs, it's worth investigating. New guide: How to build a real detection pipeline from Okta → Grove → Substation → Scanner. Here is the full guide: blog.scanner.dev/monitoring-okt…

Awesome product, @cotoolai! And thanks for the shoutout at 0:34! 😀 Teamwork makes the dream work
Cotool (@cotoolai) is an agentic security platform that eliminates manual and repetitive work for security teams. It helps teams investigate faster, automates common tasks, and documents work in seconds. ycombinator.com/launches/NW2-c… Congrats on the launch, @maxpollard415,…
Changelog: You can now transform your logs as they flow into your Scanner indexes. - Add normalized Elastic Common Schema (ECS) fields to popular log source types. - Auto-parse JSON strings and "key=value" pairs. - And more... Transformers - more than meets the eye.
anyone using data lakes for their logs? doing an info session next week about good methods we're seeing these days, particularly what detection & response teams are doing. come share how you do things! scanner.dev/events/data-la…
New Feature Announcement: 🔍Visual Query Builder – Build & switch between visual & text queries seamlessly. Auto-complete & easy visualization included! 🛡️ MITRE-Tagged Detection Rules – Organize & analyze rules with built-in & custom tags. Learn more: bit.ly/40Msfql

Join our hands-on webinar Jan 30 to learn how to streamline and deploy security detections with Scanner's schemaless log search index in your S3 bucket. UI & code-first approaches, GitHub integration—no complex schemas or heavy engineering. bit.ly/4h3h6IH

Announcing a major expansion of Scanner's detection capabilities with ready-to-use rules across 12 critical log sources bringing our total to 214 detection rules, covering 11 MITRE ATT&CK tactics and 45 techniques. bit.ly/4jjriyb
Explore the key benefits of Security Data Lakes, including advanced use cases for threat hunting, streamlined detection and response workflows, and their role in GenAI-powered analysis. bit.ly/40coiuO

Struggling with Datadog log costs? Security teams face challenges balancing Standard Logs, Flex Logs & Cloud SIEM. Learn how @scanner_dev helps optimize performance and detections, cuts costs, and enhances @datadoghq's power & efficiency. bit.ly/4fwSqHD

The @scanner_dev Playground is live! Dive into an interactive demo with AWS CloudTrail logs to experience a full threat investigation scenario. Sign up now and start exploring at scanner.dev/demo. bit.ly/4fKBlde

Congrats to the Scanner team for launching Detection Rules As Code! Our users can now manage detection rules directly in their own GitHub repos, improving collaboration, change management, continuous delivery, and streamlining threat detection development bit.ly/3XgZbqE

Announcing the release of Scanner for @ProjectJupyter, allowing users to analyze & visualize years of logs using Jupyter notebooks via the Scanner Python SDK for Response-as-Code and Advanced threat hunting on historical logs bit.ly/3W2KdCu

Our co-founders @CliftonCrosland and Steven Wu kicked off our first day at #RSAC with so many great conversations with security leaders from all over the globe that came to learn more about @scanner_dev. Come visit us at the Early Stage Expo tomorrow or Thursday. See you there!

Announcing Scanner for Splunk which makes it easy to leverage logs in S3 for advanced threat hunting and detection - all while staying entirely within the Splunk UI. Teams can now gain visibility into historical & high-volume logs while saving up to 80-90% bit.ly/3UkebRD

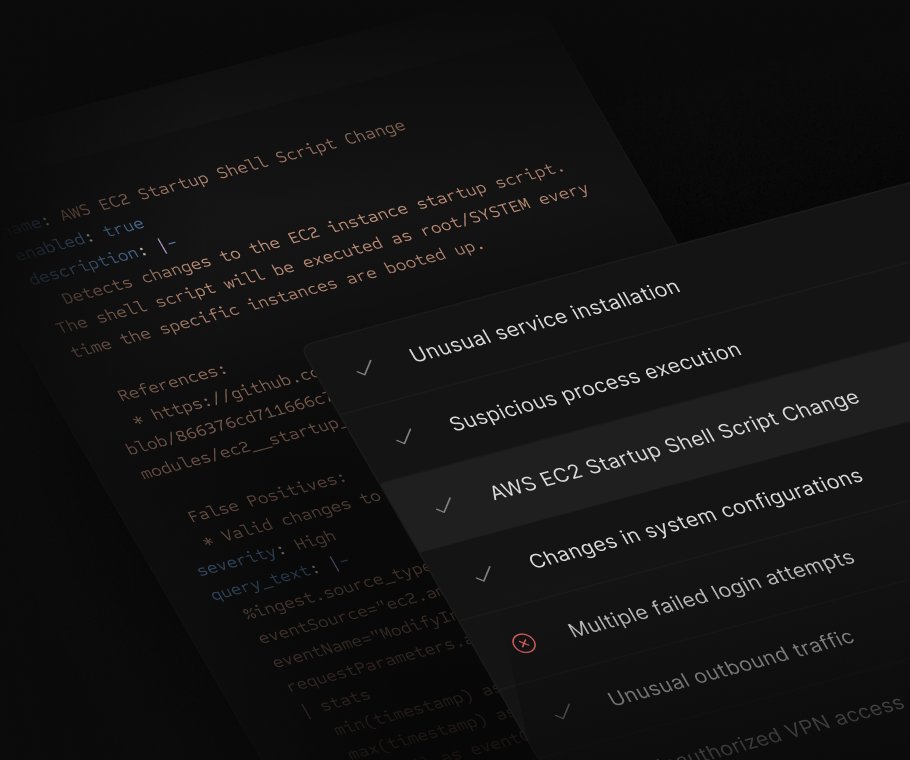
Introducing our new Threat Detection Rules to help alert teams whenever there are misconfigs, indicators of compromise, and various kinds of threat activity. Teams can even chain detections together w/ Jupyter notebooks to investigate advanced threats bit.ly/3VQ37Ow

whatever you do this year, please try not to spend half a million dollars on logs bit.ly/3tx0A0b