
𝙽𝙴𝚃𝚁𝙴𝚂𝙴𝙲
@netresec
Experts in Network Forensics and Network Security Monitoring. Creators of #NetworkMiner, #CapLoader, #PacketCache, #PolarProxy and #RawCap.
Comparison of tools that extract files from #PCAP 📖 Chaosreader ⛏️ NetworkMiner 🐿️ Suricata 🌊 tcpflow 🦈 Wireshark 👁️ Zeek netresec.com/?b=255329f

Two more #PureLogs Stealer DLL files found on vastkupan[.]com. The original blog post has been updated.
💧 Dropper connects to legitimate website 📄 Fake PDF is downloaded over HTTPS 💾 Fake PDF is decrypted to a #PureLogs DLL ⚙️ InstallUtil.exe or RegAsm.exe is started 💉 PureLogs DLL is injected into the running process 👾 PureLogs connects to C2 server netresec.com/?b=257eead
IOCs in blog post: 📡 91.92.120.101:62520 📡 91.92.120.101:65535 💾 711d9cbf1b1c77de45c4f1b1a82347e6 💾 6ff95e302e8374e4e1023fbec625f44b 💾 e6d7bbc53b718217b2de1b43a9193786 💾 a9bc0fad0b1a1d6931321bb5286bf6b7 💾 09bb5446ad9055b9a1cb449db99a7302 💾 38d29f5ac47583f39a2ff5dc1c366f7d
💧 Dropper connects to legitimate website 📄 Fake PDF is downloaded over HTTPS 💾 Fake PDF is decrypted to a #PureLogs DLL ⚙️ InstallUtil.exe or RegAsm.exe is started 💉 PureLogs DLL is injected into the running process 👾 PureLogs connects to C2 server netresec.com/?b=257eead
💧 Dropper connects to legitimate website 📄 Fake PDF is downloaded over HTTPS 💾 Fake PDF is decrypted to a #PureLogs DLL ⚙️ InstallUtil.exe or RegAsm.exe is started 💉 PureLogs DLL is injected into the running process 👾 PureLogs connects to C2 server netresec.com/?b=257eead

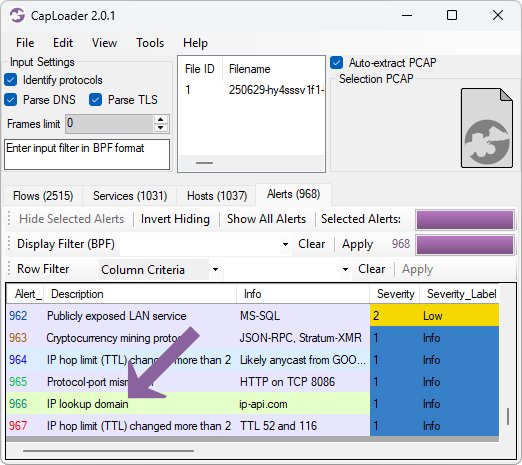
CapLoader 2.0.1 Released ⚠️ IP lookup alert 🔎 Better protocol identification 🐛 Bug fixes netresec.com/?b=2571527
Just published a new blog post on how Microsoft’s “Mouse Without Borders” can be abused for data exfiltration & lateral movement. Features KAPE Target, C# scripts, and a BOF as a poc: 0xsultan.github.io/dfir/Exfiltrat…
"cup.msi": eb2688341917d739b2048e39c9913c0c5e0e0d82346757970883c5098a0b77f3 From: https://dnsg-microsoftds-data[.]com/sign/cup.msi configedge-assets[.]org lakes-veteran-mpg-stanford.trycloudflare[.]com comprehensive-cabin-spend-organic.trycloudflare[.]com 🤔
There's some unknown but interesting C2 to 104.16.0.0/13 (@CloudFlare). C2 domains: 🔥event-time-microsoft[.]org 🔥windows-msgas[.]com 🔥event-datamicrosoft[.]live 🔥eventdata-microsoft[.]live Does anyone know malware malware this is? infosec.exchange/@netresec/1147…

Are you using Meta Pixel to track visitors on your website? Please stop! Here’s why infosec.exchange/@netresec/1146…

Video: Detecting #PureLogs C2 traffic with #CapLoader netresec.com/?b=256a8c4
CapLoader 2.0 released today! 🔎 Identifies over 250 protocols in #PCAP 🎨 Define protocols from example traffic 🇶 Extracts JA3, JA4 and SNI from QUIC 💻 10x faster user interface netresec.com/?b=256dbbc
Thank you @CISACyber, @NCSC, BSI et al. for publishing the advisory on Russian GRU Targeting Western Logistics Entities and Technology Companies. This list of mocking services is great for threat hunting! infosec.exchange/@netresec/1145…

Did you know that NetworkMiner parses the #njRAT protocol? The following artefacts are extracted from njRAT C2 traffic: 🖥️ Screenshots of victim computer 📁 Transferred files 👾 C2 commands and replies 🔑 Stolen credentials/passwords ⌨️ Keylog data netresec.com/?b=2541a39
#AutorunStealer is encrypting the config with ChaCha20 and ZLIB compression👀 Samples: f29bed66484cb23c58302c62b93fcf7d d89ea4a110c36c13ec46e80d0c9bc2ef 2c03124489072c5e0290f6ef138f39c3 39eda0b2986f484abf3567f2f5e1866d ef0e5882c8bcad3643d51d16c2f5500c…
Thanks for that great writeup on StealC v2! In addition to the HTTP based C2 there seems to be another C2 that also uses base64, but directly over TCP (no HTTP). Any ideas what this could be and how to parse this data?
Take @netresec course if you are interested in learning the dark magic of analyzing PCAPs and understanding malware protocols