mbg
@mbrg0
Breaking AI. Building @zenitysec, lead @owaspnocode.
we got an ~RCE on M365 Copilot by sending an email by ~RCE I mean full remote control over its actions - search for sensitive content (sharepoint, email, calendar, teams), execute plugins and outputs - bypass DLP controls, manipulate references, social engineer its users on our…
⚠️ Someone hacked the Amazon AI coding assistant to inject a data-wiping prompt! It was merged via a pull request due to misconfigured GitHub workflows, it went live on the VSC marketplace and it stayed undetected for 6 days. The prompt was designed to "clear a system to a…
hey look ma I'm a source
Amazon AI coding agent hacked to inject data wiping commands - @billtoulas bleepingcomputer.com/news/security/…
😐
Amazon AI coding agent hacked to inject data wiping commands - @billtoulas bleepingcomputer.com/news/security/…
hypothesis: aws had codebuild (not github actions) misconfigured s.t. it triggered internal workflows on pr triggers from forks w/o approval details now leads to 403 so can't confirm but if this is correct we should be able to find the malicious pr thx @Frichette_n
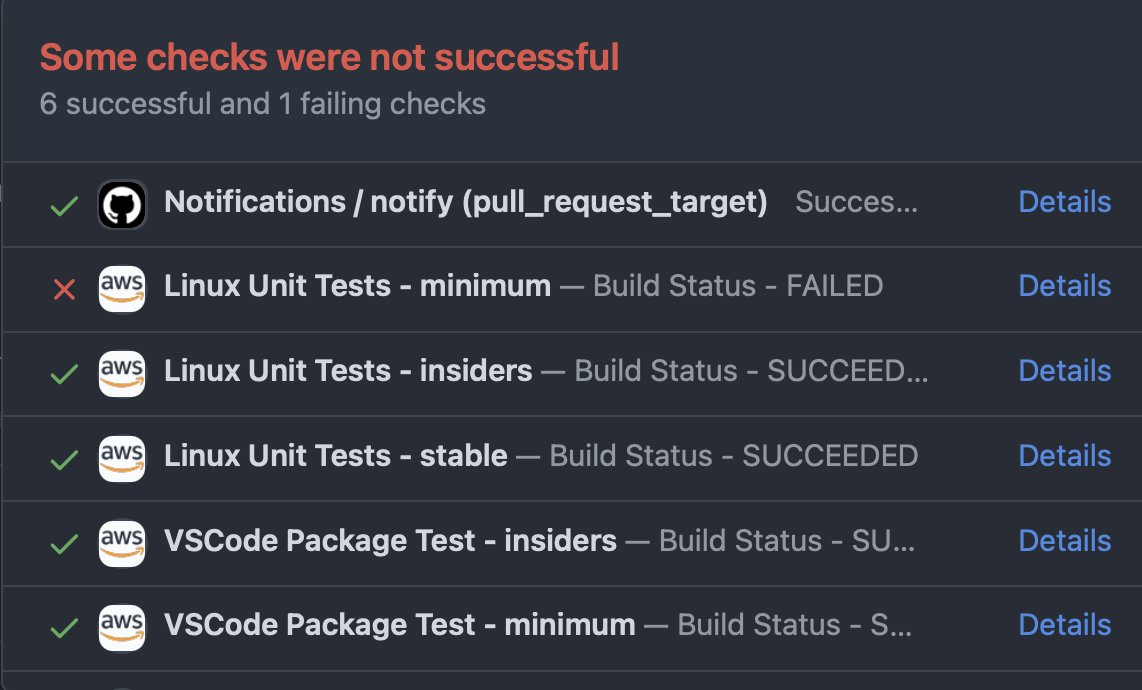
If there is anything to learn from the Q Developer incident it’s that you need to review your CI/CD pipelines for attack vectors. Who can submit PRs, what automation runs on them, how are you securing identities tied to them, etc.
New development in the Q Developer extension backdoor: An open question was, how did the threat actor get write permissions to the repo? Turns out they stole a token via this technique. aws.amazon.com/security/secur…