
Joshua Wright
@joswr1ght
Hacker for @counterhacksec and SANS Faculty Fellow. Pirata informático. Photography at http://instagram.com/joswr1ght. He/him.
I’m an Incident Responder on the AWS Customer Incident Response Team (CIRT). And I get asked a lot of questions, like: “Where do I even start with incident response in the cloud?” Here’s a beginner-friendly thread on AWS IR tips — with a few lessons I learned 🧵👇
The AI hype cycle is exhausting, but I'm trying to devote time to writing each week on what I learn. TechTarget just published my article on prompt injection attacks here: techtarget.com/searchsecurity… #AI
Here's a GREAT article by @joswr1ght about attackers shifting their tactics, exploiting "authorization sprawl." Very insightful! A must-read. techtarget.com/searchsecurity…
A concerning trend I'm seeing in attacks is not exciting, novel exploits. It's not zero-days. It's not never-before-seen endpoint bypass. It's just using the resources given to an authorized user, and it's leading to devastating compromises. techtarget.com/searchsecurity…

TIL: You can scan ports commonly associated with a protocol with @nmap like this, which scans common HTTP ports: $ nmap -p*http* host You can see the ports it will scan with the following: $ nmap -v -p*http* -oG -
Super pumped to share that Concierge has been nominated for Innovation of the Year for the SANS Difference Maker Awards. Voting ends Oct 4th... so please vote! survey.sans.org/jfe/form/SV_e3… 1
I’m looking for success or horror stories from people or orgs that have tried to disable IPv6 in Windows across the enterprise. Aaaaand…GO!
Round 3 of #EdsMagicalMysteryTour - Today, I drove to @joswr1ght’s home to hang out with Josh and his wife. We chatted about @CounterHackSec, discussed the cyber security industry, walked along the coast, had a tasty lunch in New Bedford, visited the Whaling Museum, did some…
That's me in the top-right corner. It's been great to see so many amazing people face-to-face!
That's a wrap on Day 3️⃣ of #SANS2024. Highlights from the day include: ✅ AlumNight Powered by @CertifyGIAC + #OffensiveOps ✅ SANS@Night w/ @joswr1ght & @Steph3nSims ✅ Intro to C for Windows w/ @jon__reiter Learn about #SANS2024: sans.org/u/1v9u #SANSLiveTraining
Man today I had to configure a bunch of AWS roles using policies. I thought it was going to be complicated but @SANSInstitute #HolidayHack has prepared me well for this! "I know this"
When @SANSInstitute asked me to come to Austin, I immediately said yes. Can't wait to be back in this amazing city! Planning a photography night if anyone wants to join. 📸
This year's SANS Pen Test Austin 2024 goes full #KeepHackingWeird, led by chair and course author, #SEC504, @joswr1ght. Get ready for a week of training, night talks, workshops, and networking receptions you won't forget → sans.org/u/1uX9
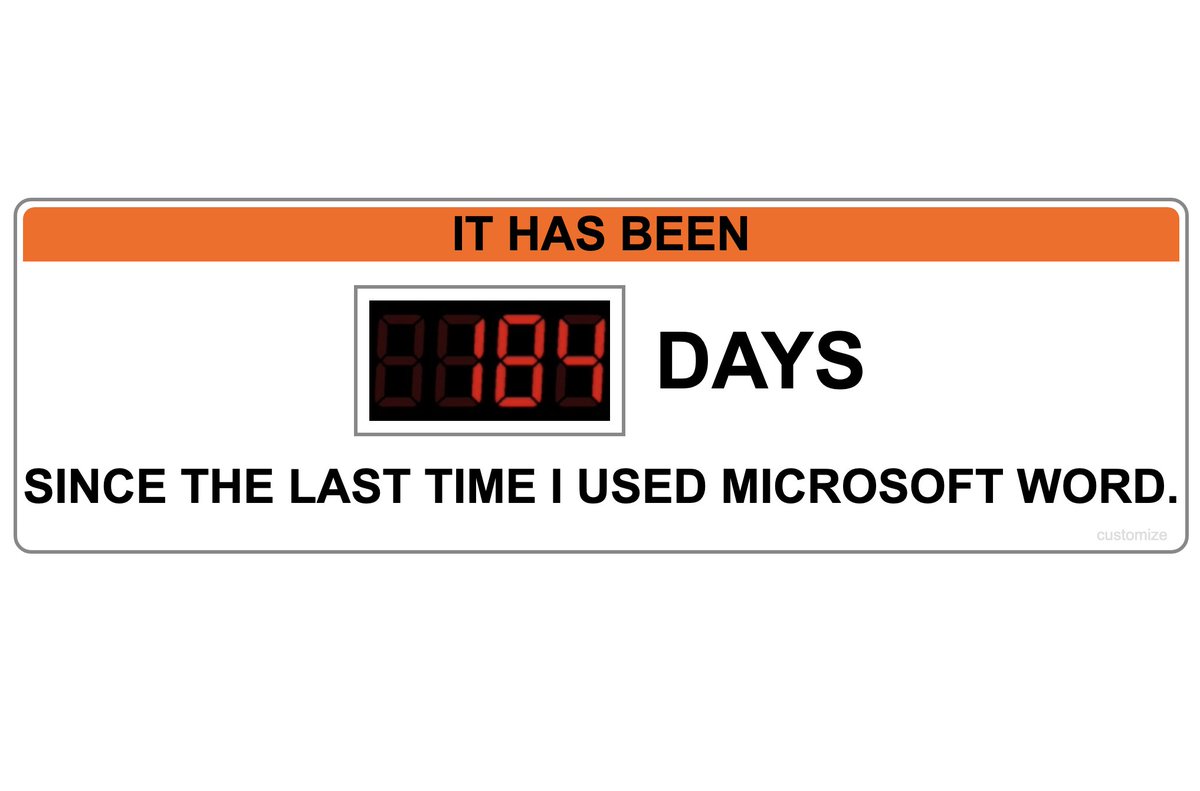
All the benefits of working with plain text. None of the inconsistencies in Markdown renderers. All the smug satisfaction in not struggling with Microsoft Word's nonsense. Thank you to @mojavelinux for the open-source gift that is @asciidoctor. asciidoctor.org
everyone with a working phone right now in the US be like
I am excited to see this presentation by these awesome analysts! Drop me a note if you’re planning on being at #HackSpaceCon!
Join us for "Navigating New Waters" with @Inscyght @CraHan @JanuszJasinski Mark D & team @CounterHackSec ! Overcome imposter syndrome in pentesting with practical tips and inspiring stories. Discover how being the 'new person' is your superpower. #Cybersecurity #ImposterSyndrome