
Jaron Bradley
@jbradley89
MacOS Intrusion Analyst, APT Smiter , Haole. Author of OS X Incident Response Scripting and Analysis Owner of http://themittenmac.com
excited bc today @HuntressLabs is releasing our analysis of a gnarly intrusion into a web3 company by the DPRK's BlueNoroff!! 🤠 we've observed 8 new pieces of macOS malware from implants to infostealers! and they're actually good (for once)! huntress.com/blog/inside-bl…
My next book is open for pre-orders!!! I have included the first two chapters in audiobook form for free. You can listen to them now on my website or you can listen and read the sample on Apple Books. Looking forward to getting it into your hands. themittenmac.com/threat-hunting…

Santa delivered my brand new book: “The Art of Mac Malware Vol II: Detecting Malicious Software” 🍎🛡️🐛👨🏻💻📚🥰 Three years in the making(!) this 2nd volume in the TAOMM series covers the heuristic-based detection of macOS malware Buy direct via @nostarch: nostarch.com/art-mac-malwar…
I’m working on a new book Thank you to all those who told me my first book has helped them in the macOS world in some way This book focuses on the internals necessary to build detections and perform analysis of intrusions on macOS Any shares to help measure interest helps!

Join me at 3:00ish pm HST to see some fun machO research. Lots of amazing talks before and after too!
Today is the day! #OBTS 🤩 Join us live: youtube.com/watch?v=LKzJuE…
Today we released a blog post detailing how threat actors are using the Flutter Engine to build malware for macOS. This results in a very complex app architecture that is difficult to reverse. Check out the details here... jamf.com/blog/jamf-thre…

My bug CVE-2024-44131 got patched on iOS 18.0. It’s an iOS TCC bypass bug that lets third-party apps access data stored on iCloud Drive. I’ll be sharing the technical details, along with demo screenshots of leaking (encrypted) WhatsApp backup data, on the Jamf Blog.
I finished Snake&Apple VIII, an introduction to #Apple #App #Sandbox on #macOS. Inside, you will find info about kernel extension and how Sandbox Profiles are enforced to mitigate the risks of successful macOS #malware #infection. karol-mazurek.medium.com/snake-apple-vi… Enjoy reading! 👨💻
The FBI recently sent a warning out regarding DPRK activity against the crypto industry. Today, we documented attacks we've seen on macOS. Attacks start with social engineering and deliver a piece of malware that we call ThiefBucket. jamf.com/blog/jamf-thre… #malware

This was very good last year, @jbradley89 is an excellent trainer
Jaron Bradley's (@jbradley89) training, "Threat Hunting macOS" provides an in-depth and hands experience, for those looking for a deep dive into using macOS internals to their advantage for threat hunting! 🔎🍎🖥️ More info/to sign up: themittenmac.com/macos-threat-h…
Honored to speak on the makers track at #FTSCon with some of these great presenters
We have another speaker to announce in our #FTSCon lineup: Jaron Bradley (@jbradley89) will present “Grafting Trees on macOS” in the MAKER Track! For event details, see the #FTSCon event page: volatilityfoundation.org/from-the-sourc… You can also register here: events.humanitix.com/from-the-sourc… #dfir
Some awesome Gatekeeper vulnerability research from @malwarezoo that lead to the discovery of vulnerabilities in other products. Check it out on our blog when you get time.
Our latest research details a Gatekeeper bug we reported to Apple that affects Launch Services. While exploring this issue, we also found ways to bypass Gatekeeper using the “The Unarchiver”, a popular archiving application on macOS. Check out our blog: jamf.com/blog/gatekeepe…
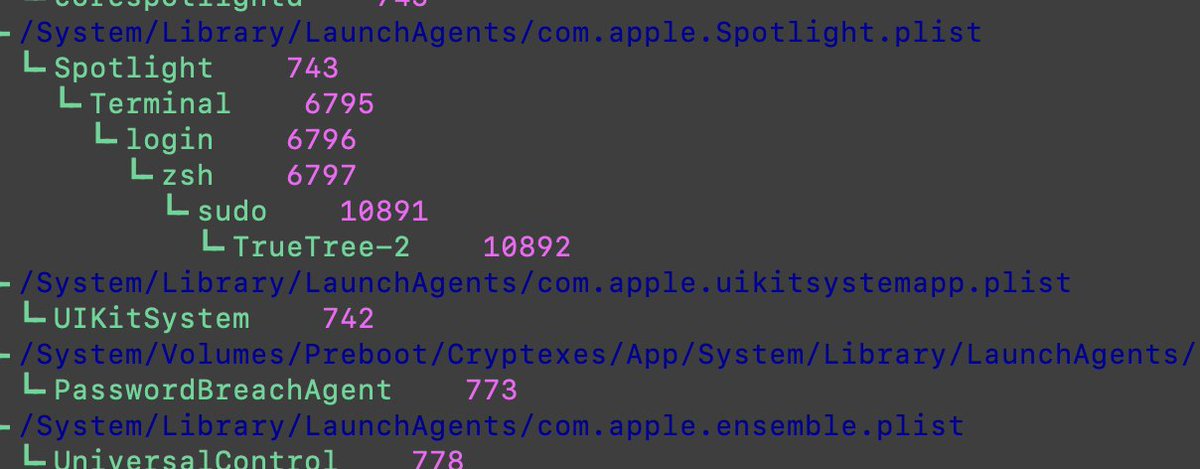
TrueTree 0.8 is out. Its primary difference is that when displaying the tree , it will attempt to use other pids only if the parent process of that given process id is launchd. You also now have the ability to display only the process name with --nopath github.com/themittenmac/T…
Join as at the Objective by the Sea conference where I'll be talking about how our team has been working on some new and intuitive ways of analyzing and categorizing macOS malware using data science and 3D visualization! Also, it's Hawaii
#OBTS v7 talks have been announced: objectivebythesea.org/v7/talks.html 🤗 With over 20 talks (from many of the world's top researchers), covering macOS/iOS bugs & exploits, malware, internals, tools, and much more, this is a can't miss event! Which talks are you most excited about?
Come join my RSA talk tomorrow on dynamic malware analysis using a tool titled SpriteTree!
Stop by our @RSAConference booth tomorrow at 8:30am PT to catch @jbradley89's session: Dynamic Analysis of MacOS Malware Using SpriteTree. This talk will focus on a community tool titled SpriteTree. Details here: rsaconference.com/usa/agenda/ses…
Been digging into some interesting macOS malware with @birchb0y recently. Check out the new blog!
my first blog post since starting at @HuntressLabs just dropped! 🔥 @stuartjash and I take a look at the recently discovered macOS #LightSpy variant and highlight some of the major differences between it and the iOS version!🍎 huntress.com/blog/lightspy-…
Last year, I attended Jaron Bradley's training about MacOS thread hunting where we learned how to hunt down malicious activity using various tools. I enjoyed the training and getting to chat with experts like Jaron/other speakers was a real bonus.
Rustbucket Malware still showing signs of being updated...
We've found a payload that appears as if attackers have taken a stage-3 RustBucket malware (originally written in Rust) and converted it to compiled AppleScript. virustotal.com/gui/file/70404… 1/n
Stoked to announce "Objective by the Sea" v7.0: objectivebythesea.org/v7/index.html #OBTS v7: 📍 Maui, Hawai'i 🗓️ Dec. 2nd - 6th '24 ...hope to see you all there! 🌞🌴