
Denis Laskov 🇮🇱
@it4sec
Cybersecurity & Technology, Hacker, Father. Today: Chief Hacker at EY IL. ex-Mercedes-Benz, ex-IBM, ex-IDF. On LinkedIn, Mastodon and Bluesky as well.
Cloning and emulating HID SEOS cards: a step-by-step guide to hacking the second most popular smart card architecture. 🎫🐬၊၊||၊🔓 More details on: LinkedIn: linkedin.com/posts/dlaskov_… Substack: it4sec.substack.com/p/cloning-and-…

A great idea for hardware hacking training: spotting fake chip components in products (yes, they’re already here). 🪲👨🔧🏴☠💵 More details on: LinkedIn: linkedin.com/posts/dlaskov_… Substack: it4sec.substack.com/p/a-great-idea…

Bluetooth and its privacy issues: Practical discovery of non-discoverable Bluetooth devices. 🔵🦷🔎😈 More details on: LinkedIn: linkedin.com/posts/dlaskov_… Substack: it4sec.substack.com/p/bluetooth-an…

New attack vector for Android infotainment: Quick Share is coming to Android for cars, so here are the protocol details and RCE chain. 🚗 👻 📱🚨 More details on: LinkedIn: linkedin.com/posts/dlaskov_… Substack: it4sec.substack.com/p/new-attack-v…

Hacking a proprietary ATM security suite - and accidentally, casino equipment too: 6 vulnerabilities and how to find them. 🏧🎰 👨🏻💻 💸 More details on: LinkedIn: linkedin.com/posts/dlaskov_… Substack: it4sec.substack.com/p/hacking-a-pr…

Cybersecurity of Power Line Communications (PLC): the basics you need to know about the protocol, the hardware, and how to attack it. ⚡🔌🚽 ☠️ More details on: LinkedIn: linkedin.com/posts/dlaskov_… Substack: it4sec.substack.com/p/cybersecurit…

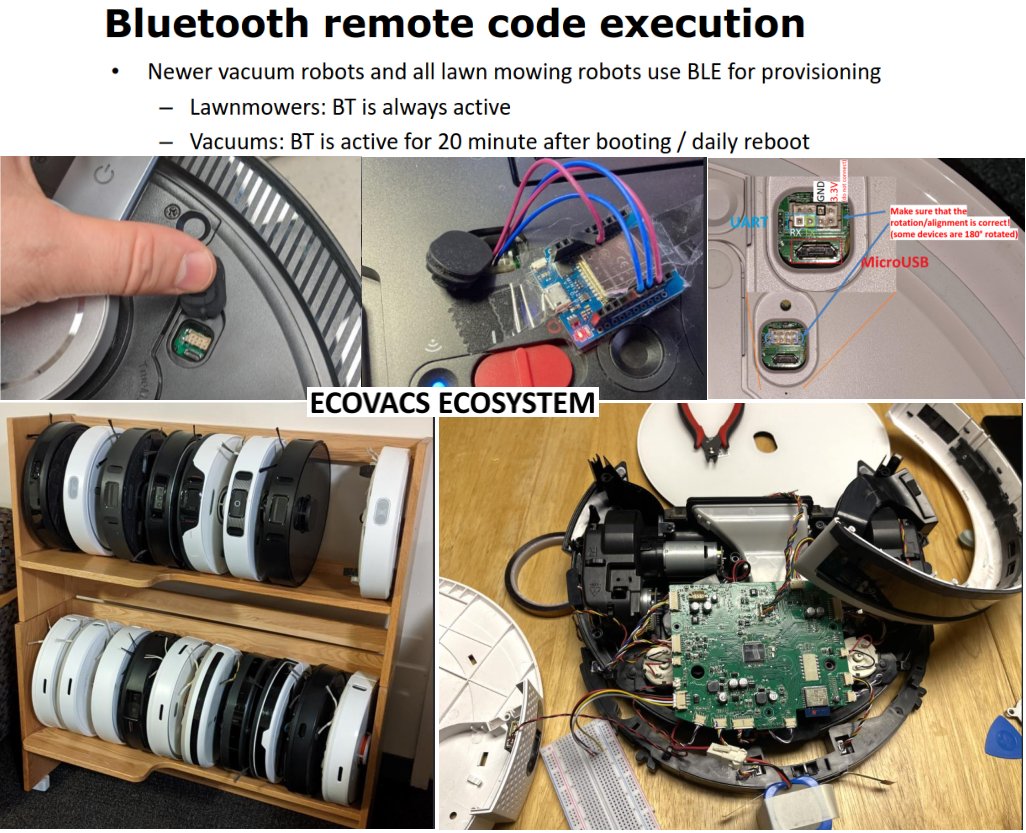
Reverse engineering Ecovacs vacuum and lawn mowing robots and using Bluetooth RCE to turn them into moving webcams. 👩🏽🦯💥👁️🥷 More details on: LinkedIn: linkedin.com/posts/dlaskov_… Substack: it4sec.substack.com/p/reverse-engi…
Hacking the Chipolo One Bluetooth tracker: remote code execution via melody update. 🐱🥇၊၊||၊👨🏻💻 More details on: LinkedIn: linkedin.com/posts/dlaskov_… Substack: it4sec.substack.com/p/hacking-the-…

Hacking an ECU from an undisclosed (maybe your?) car: Using glitching to extract MPC5566 firmware via CAN. 🥷🏻🫨🚗🔐 More details on: LinkedIn: linkedin.com/posts/dlaskov_… Substack: it4sec.substack.com/p/hacking-an-e…

A Mexican drug cartel hired a hacker to break into phones and CCTV cameras; they were looking for FBI informants. 💉 👨🏻💻 🖲 ☠️ More details on: LinkedIn: linkedin.com/posts/dlaskov_… Substack: it4sec.substack.com/p/a-mexican-dr…

Key fob cloning caught on camera: One thief breaks the driver's window, another connects to the OBD port, and the car is gone. 🚘🔨💻😈 More details on: LinkedIn: linkedin.com/posts/dlaskov_… Substack: it4sec.substack.com/p/key-fob-clon…
DJI drone security analysis: reverse engineering communication, firmware extraction, and fuzzing for vulnerabilities. 𖥂🎮 ၊၊||၊ 💥 More details on: LinkedIn: linkedin.com/posts/dlaskov_… Substack: it4sec.substack.com/p/dji-drone-se…

Critical chain of vulnerabilities in the Bluetooth stack enables 1-click RCE (remote code execution) on German cars. 🚘 🔵🦷💥 More details on: LinkedIn: linkedin.com/posts/dlaskov_… Substack: it4sec.substack.com/p/critical-cha…

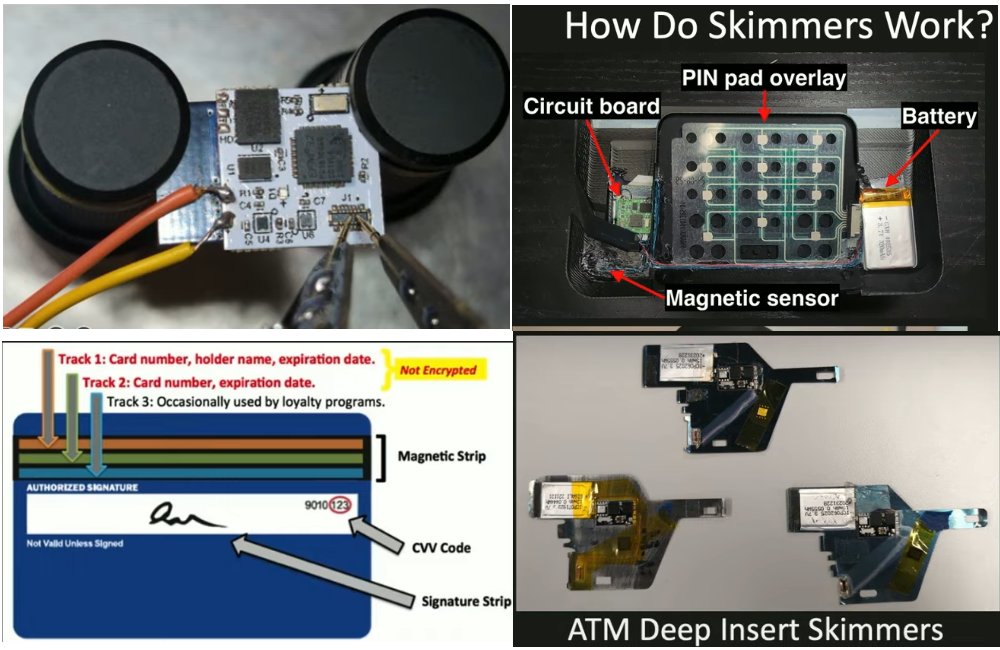
How credit card skimmers work: reverse engineering skimmers to recover stolen data (and much more!) 💳🏧💸🥺 More details on: LinkedIn: linkedin.com/posts/dlaskov_… Substack: it4sec.substack.com/p/how-credit-c…
Security analysis of airplane datalink apps: "spoof-and-jam" attacks on plane communication systems (CPDLC and ADS-C). 📡 ၊၊||၊ 💀✈️ More details on: LinkedIn: linkedin.com/posts/dlaskov_… Substack: it4sec.substack.com/p/security-ana…

$4 for a cellular hacking device: cheap, reliable, and DIY equipment for SIM card vulnerability research. 👨🏻💻 💲📳 🐞 More details on: LinkedIn: linkedin.com/posts/dlaskov_… Substack: it4sec.substack.com/p/4-for-a-cell…

Finding vulnerabilities in industrial equipment at scale: the first native ICS fuzzer with scan-cycle awareness. 🏭🫨🍮🌟 More details on: LinkedIn: linkedin.com/posts/dlaskov_… Substack: it4sec.substack.com/p/finding-vuln…

EU streetlights are controlled by low-frequency radio signals - here’s how to turn that into an art installation (or a blackout). ⚡၊၊||၊ 👨💻၊၊||၊ 💡 More details on: LinkedIn: linkedin.com/posts/dlaskov_… Substack: it4sec.substack.com/p/eu-streetlig…

$60,000 for a 2-bug chain to exploit the Autel MaxiCharger: RCE via Bluetooth plus authentication bypass. ⛽🔵🦷💥🔫 More details on: LinkedIn: linkedin.com/posts/dlaskov_… Substack: it4sec.substack.com/p/60000-for-a-…


