inzo
@inzo____
always hunting for the unseen;
Happy to share my first article with @zhero___, which is also my first CVE (CVE-2025-29927) on the largest JS framework: Next.js. A critical vulnerability that impacts a wide range of sensitive sectors across the internet.
the research paper is out: Next.js and the corrupt middleware: the authorizing artifact result of a collaboration with @inzo____ that led to CVE-2025-29927 (9.1-critical) zhero-web-sec.github.io/research-and-t… enjoy the read!
> valid reports frantically closed by the same analyst who doesn't understand the vuln (nor tries/ask) > mediation disabled for these reports(?) > reports resent hoping to find a different analyst > same analyst, reports closed listen, here, what I don't understand doesn't exist
new discovery: cache poisoning on next.js - CVE-2025-49826 indefinite caching of a 204 response, rendering the affected pages inaccessible affected versions: >15.0.4 and <15.2.0 there will be no research paper for this one
back to work with @zhero___ and a new vulnerability on @nextjs that led to CVE-2025-49826 both routers are impacted: app router: framework's cache is directly impacted on ISR pages, regardless of the presence of a CDN pages router: SSR pages only + requires a misconfigured CDN
Bug bounty, feedback, strategy, and alchemy frequently asked for advice, roadmaps, and more, I finally took the time, after 2–3 years of bug bounty, to write down my vision, thoughts and perspective on the subject non-technical, no research this time! zhero-web-sec.github.io/thoughts/bugbo…
The real key is to focus on maximizing your bug hunting income, making smart investments, and ultimately transitioning to full-time zero-day research once your investments cover all your living expenses.
The key is to maximize your bug hunting income, invest wisely, and gradually stop hunting as your investments fully cover your expenses. 🤓☝️
Vercel customers are protected from two high-severity vulnerabilities (CVE-2025-43864 and CVE-2025-43865) in Remix and React Router. Read our advisory to understand impact and next steps. vercel.com/changelog/prot…
another research effort with @inzo____ led to the discovery of two new vulnerabilities in React Router (14M+ downloads/week), resulting in: - CVE-2025-43865 (High-8.2) - CVE-2025-43864 (High-7.5)
back to work, a sleepless night and 2 open-source vulnerability reports submitted; back on track with @inzo____
new paper on a vulnerability discovered in React Router, resulting from a collaboration with @inzo____ that led to CVE-2025-31137; React Router and the Remix'ed path zhero-web-sec.github.io/research-and-t… good reading
new open-source software vulnerability report sent with @inzo____ let's see;
The 9.1 CVSS CVE-2025-29927 authentication bypass vulnerability in Next.js middleware -- covered in a rambling video and teeny tiny demo showcase, ✨ V I B E C O D I N G✨ a vulnerable proof-of-concept app. youtu.be/dL1a0KcAW3Y
the research paper is out: Next.js and the corrupt middleware: the authorizing artifact result of a collaboration with @inzo____ that led to CVE-2025-29927 (9.1-critical) zhero-web-sec.github.io/research-and-t… enjoy the read!
Next.js 15.2.3 includes a security vulnerability patch. We recommend updating to 15.2.3 or backported patches. If you cannot update, we have included guidance for how to protect your application. Apps on Vercel, Netlify, and Cloudflare are not affected. nextjs.org/blog/cve-2025-…
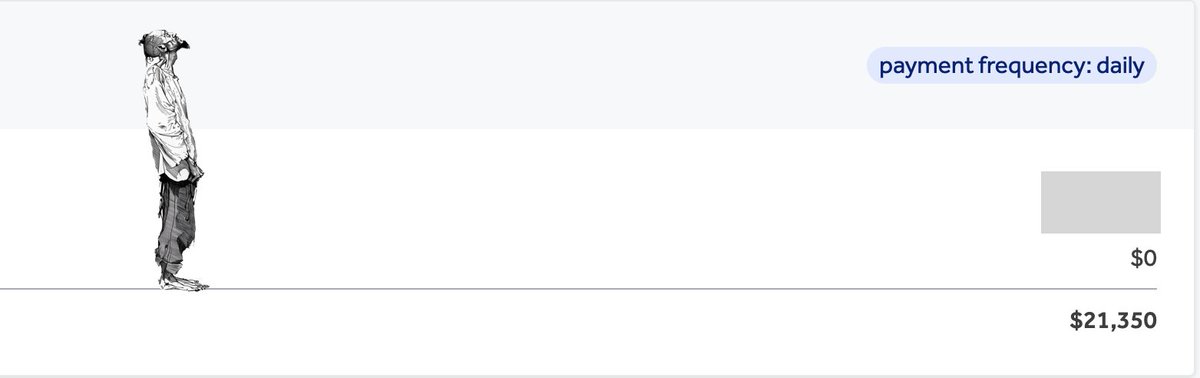
Bug bounty is a dopamine rush, it's true. But it's also a discipline, a constant grind, an obsession with understanding and exploiting what others have overlooked What a nice payment coming