Hiroshi Suzuki
@herosi_t
A malware analyst, forensic investigator, incident responder and researcher. A conference speaker and trainer such as Black Hat, Virus Bulletin and FIRST.
Thanks to YOU, our course at #BHUSA have sold out now! However, don't worry about it. We will add several seats. Stay tuned! @BlackHatEvents blackhat.com/us-19/training…

TorNetとPureHVNCを実行する新種のローダーの調査 | IIJ Security Diary sect.iij.ad.jp/blog/2025/07/l… @IIJSECT
Technical Analysis of NailaoLocker Ransomware | IIJ Security Diary (in English) sect.iij.ad.jp/en/2025/07/tec… @IIJSECT
ランサムウェアNailaoLockerの調査 | IIJ Security Diary sect.iij.ad.jp/blog/2025/06/r… @IIJSECT
All YARA rules from this REsearch are publicly available! Additionally, the ida_bootkit_finder scripts automate the discovery of bootkit-related patterns for IDA analysis. Happy Hunting!🔬 github.com/binarly-io/Res…
Some exciting research to share from Binarly REsearchers @cci_forensics and @pagabuc -- a novel approach to UEFI bootkit detection. 🔥Read the technical paper: "UEFI Bootkit Hunting: In-Depth Search for Unique Code Behavior" 👉 binarly.io/blog/uefi-boot…
My presentation slides "UEFI Bootkit Hunting: In-Depth Search for Unique Code Behavior" @REverseConf are available online github.com/binarly-io/Res…
I updated PyClassInformer to add several new features such as auto-renaming virtual methods, detecting user-defined classes, detecting possible constructors and destructors, tree-based widget to display class-related information and so on. github.com/herosi/PyClass…
I've released a new tool "PyClassInformer". It detects vftables in a program compiled with MSVC++ by parsing RTTI. It is written in pure python. So, it runs on MacOS and Linux as well as Windows. #cpp, #vftable, #RTTI, #IDA, #IDAPython, #ReverseEngineering github.com/herosi/PyClass…
I've released a new tool "PyClassInformer". It detects vftables in a program compiled with MSVC++ by parsing RTTI. It is written in pure python. So, it runs on MacOS and Linux as well as Windows. #cpp, #vftable, #RTTI, #IDA, #IDAPython, #ReverseEngineering github.com/herosi/PyClass…

Hi #DFIR community, I'm excited to announce that I have published my new forensic tool for analyzing journal data from #Linux file systems (EXT4 and XFS). 🔗 github.com/mnrkbys/fjta This tool requires TSK's develop branch to recognize the XFS file system, so you will need to…
#UAC (Unix-like Artifacts Collector) v3.0.0 has been released. Many of my PRs were also merged! Thanks, @tclahr. #DFIR #Linux
New #UAC (Unix-like Artifacts Collector) v3.0.0 released! 🌟 New features 🔎 New artifacts 👨💻 Thanks to all the contributors!!! Get it here: github.com/tclahr/uac#dfir #digitalforensics #cybersecurity #infosec
#gccsec #seccamp
GCC 2025 TaiwanでC++マルウェアの解析に関する講義することになりました。 gcc.ac/#reverse-engin… 募集は以下のページでされています。興味のある学生さん、応募お待ちしております。 security-camp.or.jp/event/gcc_taiw…
GCC 2025 TaiwanでC++マルウェアの解析に関する講義することになりました。 gcc.ac/#reverse-engin… 募集は以下のページでされています。興味のある学生さん、応募お待ちしております。 security-camp.or.jp/event/gcc_taiw…
サイバーセキュリティの世界でトップクラスのカンファレンスBlack Hat USA 2024にIIJの高山が参加しました。高山はIIJチームが提供するトレーニングコースのサポートをしつつ、様々な発表も聴講しています。そのサマリがレポートされています、どれも面白そうです。 eng-blog.iij.ad.jp/archives/27540
Due to some missing links on the conference web pages, I uploaded my conference talk pdfs for 10 years. Time flies. speakerdeck.com/takahiro_haruy…
Early pricing for our #BHUSA course ends this Friday. To save $300, join our DFIR course now! blackhat.com/us-24/training…
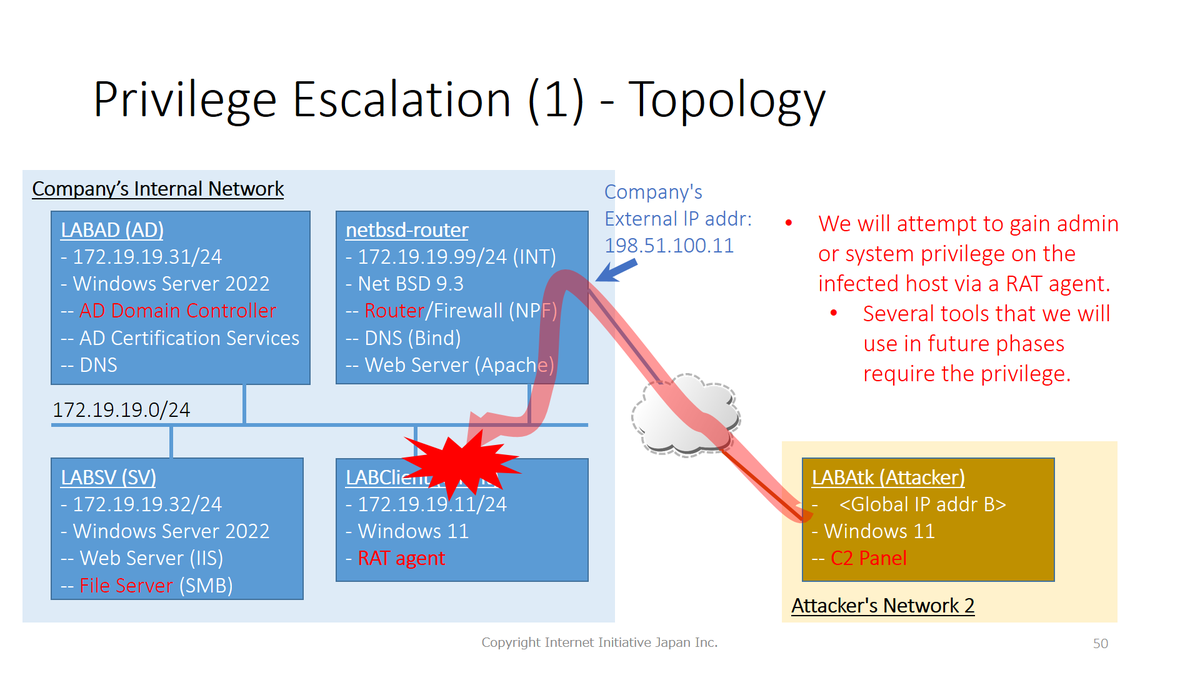
Our #BHUSA DFIR course will attack Win11 23H2 and Server 2022 with in-the-wild malware/attack tools. Then, we will analyze them to discover what evidence the attack tools remain, which means you can learn both attack and defense. Join our course: blackhat.com/us-24/training…
Our #BHUSA DFIR course will attack Win11 23H2 and Server 2022 with in-the-wild malware/attack tools. Then, we will analyze them to discover what evidence the attack tools remain, which means you can learn both attack and defense. Join our course: blackhat.com/us-24/training…


Google Chrome Platform Notifications Database analysis with the new @ArsenalRecon LevelDB parser sans.org/blog/google-ch…
related to this APT case virusbulletin.com/conference/vb2…
Visual Studio Code (VS Code) used by APT actor as a RAT tool case report. Our research member's presentation material at JSAC2024 is available now. jsac.jpcert.or.jp/archive/2024/p…
I wrote a script to convert Cisco MZIP format firmware into ELF. It might help checking manipulated firmware by attackers. Enjoy! github.com/herosi/mzip2elf
The tool, result and exploit PoCs github.com/TakahiroHaruya… Intel didn't assign the CVE number for stdcdrv64.sys but told us the driver was fixed.