Elad Shamir
@elad_shamir
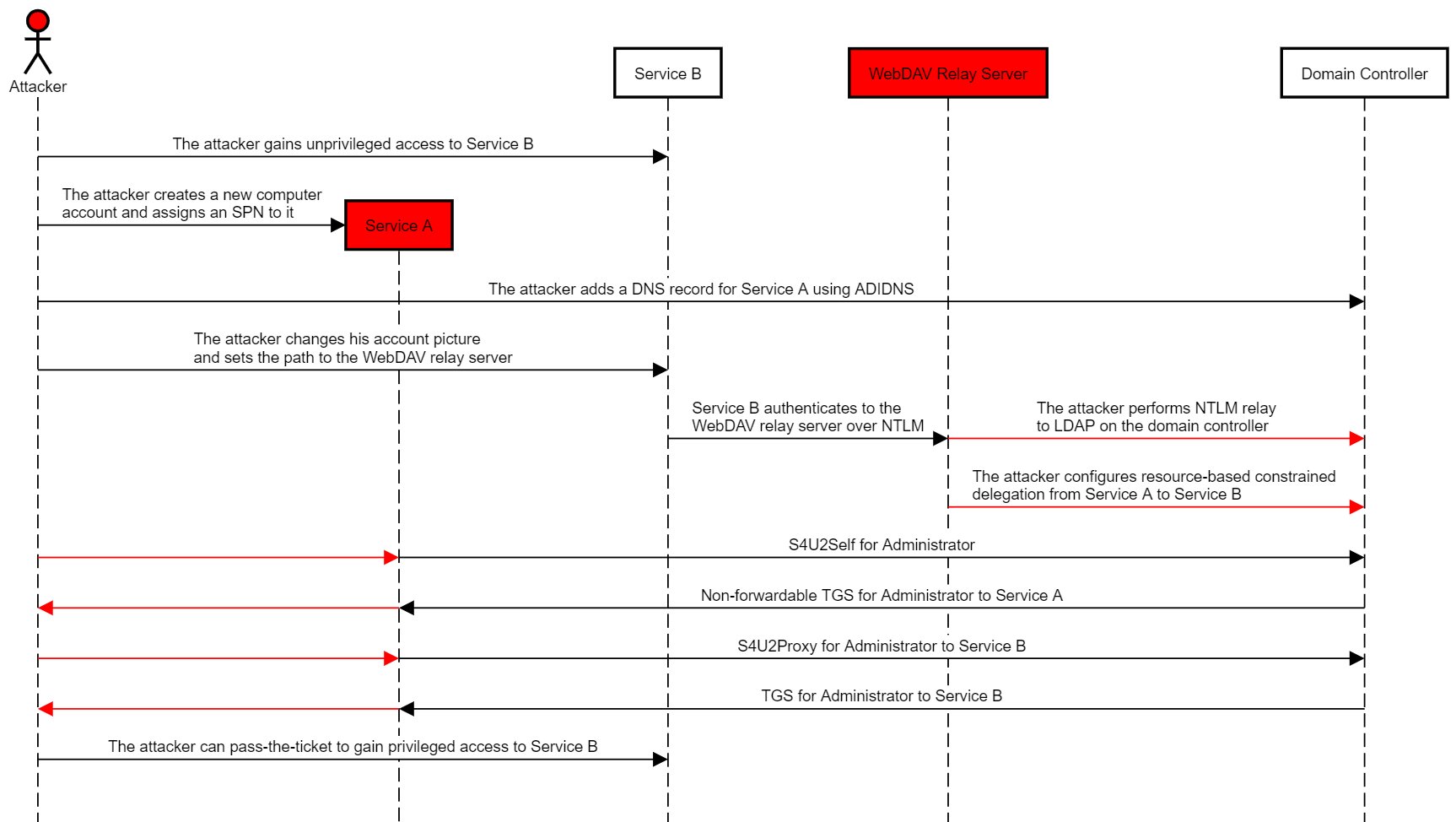
Check out my latest research "Wagging the Dog: Abusing Resource-Based Constrained Delegation to Attack Active Directory" New attack techniques and live 0days inside. MSRC’s response: "this is not an issue which will be addressed via a security update" shenaniganslabs.io/2019/01/28/Wag…
Attended this remotely for Identity-Driven Offensive Tradecraft from @elad_shamir. 10/10 course, the @SpecterOps team had insane levels of knowledge on the topics 🔥🔥
Thanks to all the ghouls and ghosts who joined us for the chilling training sessions and spine-tingling fun at Specter Bash in Denver! 👻🎃 Our team loved sharing hacking horror stories and indulging in eerie Halloween activities. We hope you had a frightfully good time!
I'm super happy to announce an operationally weaponized version of @YuG0rd's BadSuccessor in .NET format! With a minimum of "CreateChild" privileges over any OU it allows for automatic escalation to Domain Admin (DA). Enjoy your inline .NET execution! github.com/logangoins/Sha…
NTLM relay is still a major threat and is now even easier to abuse. We just added new NTLM relay edges to BloodHound to help defenders fix and attackers think in graphs. Read my detailed post - the most comprehensive guide on NTLM relay & the new edges: ghst.ly/4lv3E31

Think NTLM relay is a solved problem? Think again. Relay attacks are more complicated than many people realize. Check out this deep dive from @elad_shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31
The CFP for #SOCON2025 is now open! 🙌 If you have an idea for a talk delving into the complexities of identifying, executing & protecting against modern Attack Paths, we invite you to submit your presentation before the November 15 deadline. Submit ➡️ ghst.ly/cfp-socon25
If you liked RTO from @SpecterOps or have attack/defense experience, check out the continuation, Identity-driven Offensive Tradecraft. I got a preview and it's PACKED with techniques that work against well-defended targets. Virtual or in Denver w/ @elad_shamir and @_xpn_ Oct 7-10
New blog post just dropped! 😎 In this installment of our blog series on Identity-Driven Offensive Tradecraft, @elad_shamir shares a framework he developed for discovering known & unknown Attack Paths. posts.specterops.io/navigating-the…
Yesterday, I wrote a thread describing the ESXi vulnerability and how you can use BloodHound's Attack Path Management approach to quantify the impact of such a group. However, it's useful to understand our exposure to the vulnerability as well. x.com/jaredcatkinson…
🧵 Yesterday Microsoft released a post describing CVE-2024-37085, a vulnerability in ESXi hypervisors. According to the disclosure, a low-privilege user can gain "full administrative access" to domain-joined ESXi hypervisors. microsoft.com/en-us/security…
Check out my latest blog post, "The Security Principle Every Attacker Needs to Follow", in which I lay the foundation for a framework for discovering attack paths, including those that BloodHound can't find yet. posts.specterops.io/the-security-p…
Kicking this week off with a new blog post from @elad_shamir introducing our new Identity-Driven Offensive Tradecraft training and the principle behind the course framework, the Clean Source Principle. Read more: ghst.ly/4fgfuuq
My On Detection series continues. In part 14 I look at a “special” subset of operations that require a bit more detail to facilitate accurate detection. While this topic is more focused on the model, I finish the post by analyzing one of the variants of PoolParty Injection!…
I've released another post in my On Detection series. This edition builds on the previous post where I introduced "execution modalities." Here we look at how modalities, like behavior, can impact detection efficacy and how we can deal with that fact. posts.specterops.io/part-13-415c4d…
My On Detection series is back! In this edition I explore how the same behavior (operation chain) can be implemented using several different execution modalities and the implications of this for detection engineers. posts.specterops.io/behavior-vs-ex…
It's a big day- @tifkin_, @0xdab0, and I are proud to announce that Nemesis 1.0.0 has landed! We have a ton of awesome new features and a streamlined installation, check out the details at posts.specterops.io/nemesis-1-0-0-… and the code at github.com/SpecterOps/Nem…
My heart breaks hearing and seeing the atrocities committed by the demonic terrorists against Israelis simply for being Jews. Brutal murders. Mutilation. Entire families burned alive. Kidnap of the elderly, women, and children. Rapes. Beheadings. It is not fake news. We saw the…
A few months ago, I delivered a webinar on the topic of Kerberos abuse. It covers all the basics and some more advanced topics. It is now on YouTube if you missed it or want to watch it again: youtu.be/9SUXifUp9ZY
This will be an interesting one. We're running a webinar about defining Tier Zero at the same time (ghst.ly/42iswQy), so I won't be able to attend. But if anyone wants to see both webinars, ours will be available on demand later on.
Just a few more hours until our AMA free for all. Get all your Active Directory & Azure AD questions answered. Maybe we can also find out how @PyroTek3 gets his hair to be so luxurious. Thu, Jun 22, 2023, 2pm - 3pm EDT attendee.gotowebinar.com/register/82787…
Yesterday @hotnops and I gave a talk at @fwdcloudsec about abusing Cloud Kerberos Trust to gain Domain Admin on-prem. You can watch the talk at: youtu.be/JCphc30kFSw?t=… The slide deck is available at: eladshamir.com/uploads/fwdclo… Demos: youtu.be/cs8ATpuIuzw…
Have you ever wondered how RODCs work and whether compromising one would necessarily allow for privilege escalation? The answers are in my new post: At the Edge of Tier Zero: The Curious Case of the RODC posts.specterops.io/at-the-edge-of…
