CyberWar - 싸워
@cyberwar_15
Since. 2001. 8. 8 / 우리는 2001년 8월 8일부터 북한 사이버 공작원과 싸우고 있습니다.
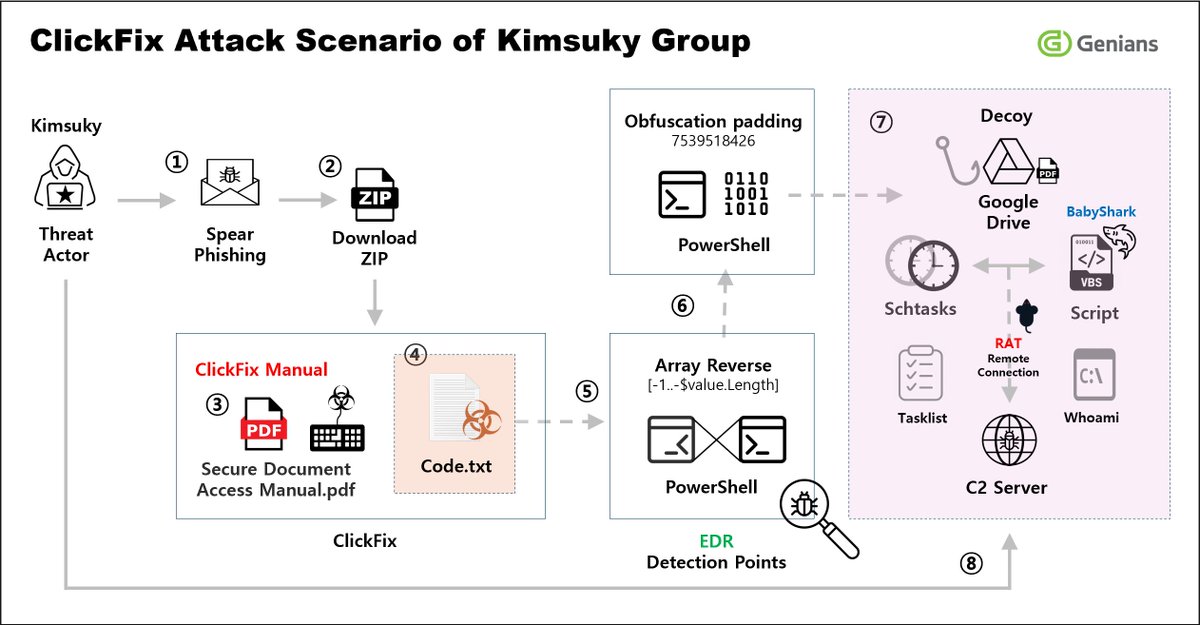
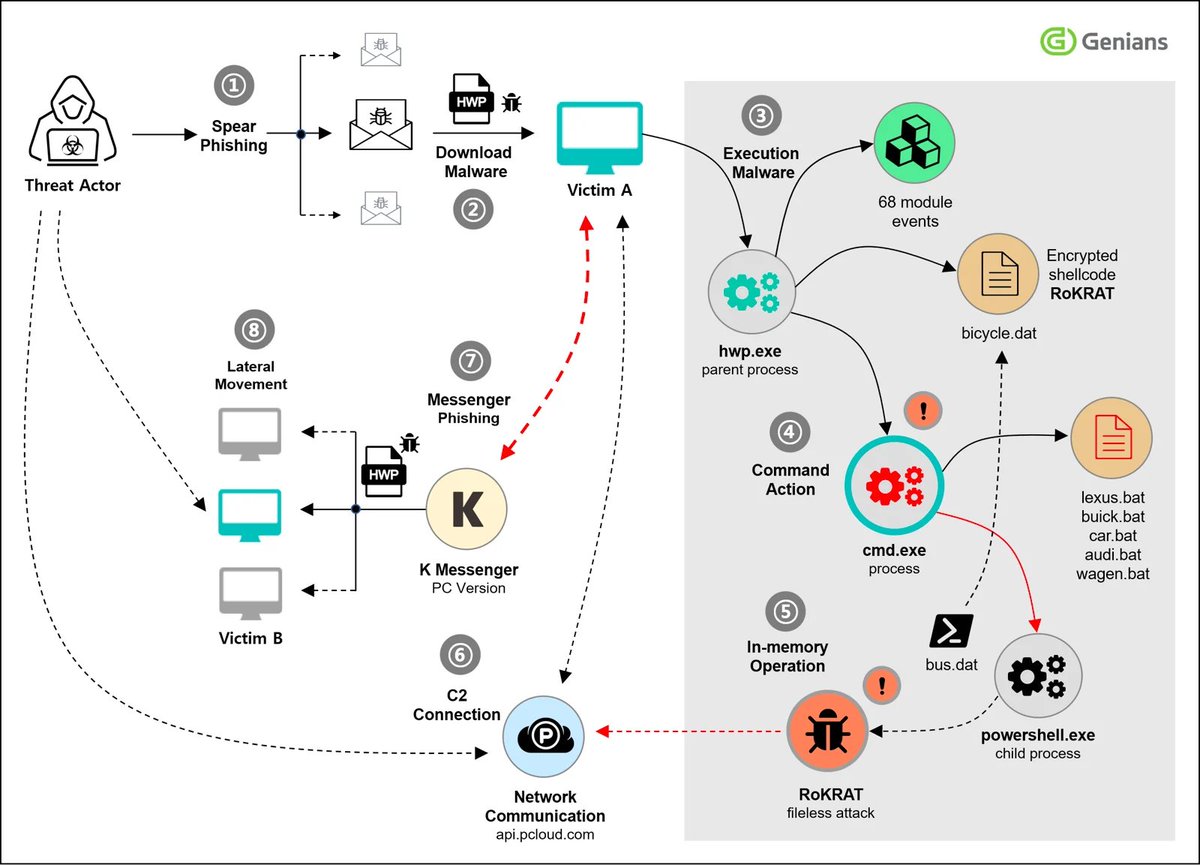
#NorthKorea #Kimsuky #ClickFix Analysis of the threat case of kimsuky group using 'ClickFix' tactic genians.co.kr/en/blog/threat… 56233bac07f4f9c43585e485e70b6169 a523bf5dca0f2a4ace0cf766d9225343 ad6104a503b46bf6ea505fe8b3182970 bf795a376233032d05766a396b3d6e08 ........
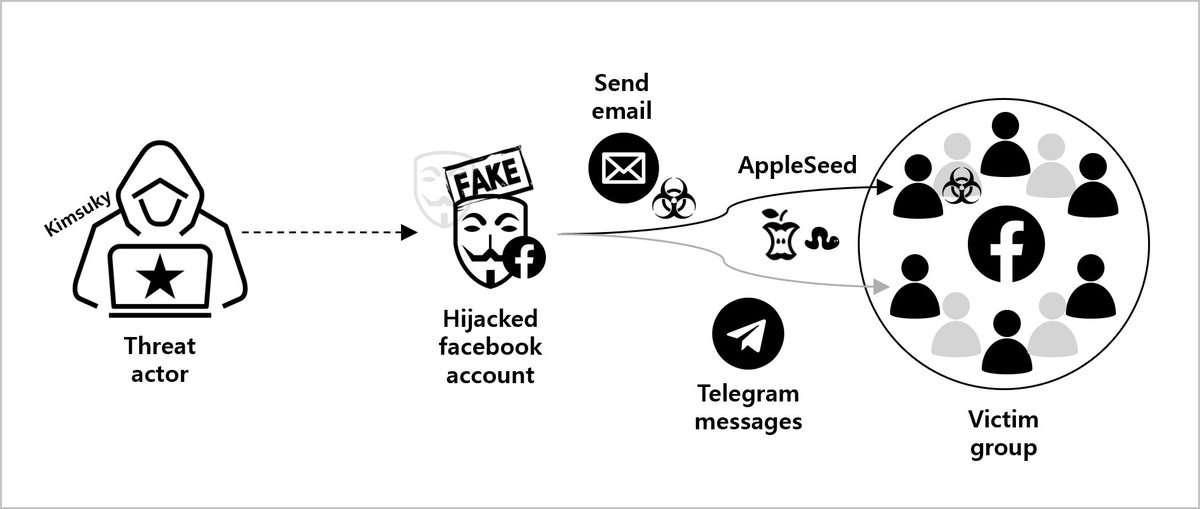
#NorthKorea #APT #Kimsuky #AppleSeed genians.co.kr/en/blog/threat… Deployed a covert infiltration strategy using a three-stage communication channel: Facebook, email, and Telegram 2f6fe22be1ed2a6ba42689747c9e18a0 5a223c70b65c4d74fea98ba39bf5d127 7a0c0a4c550a95809e93ab7e6bdcc290 ....
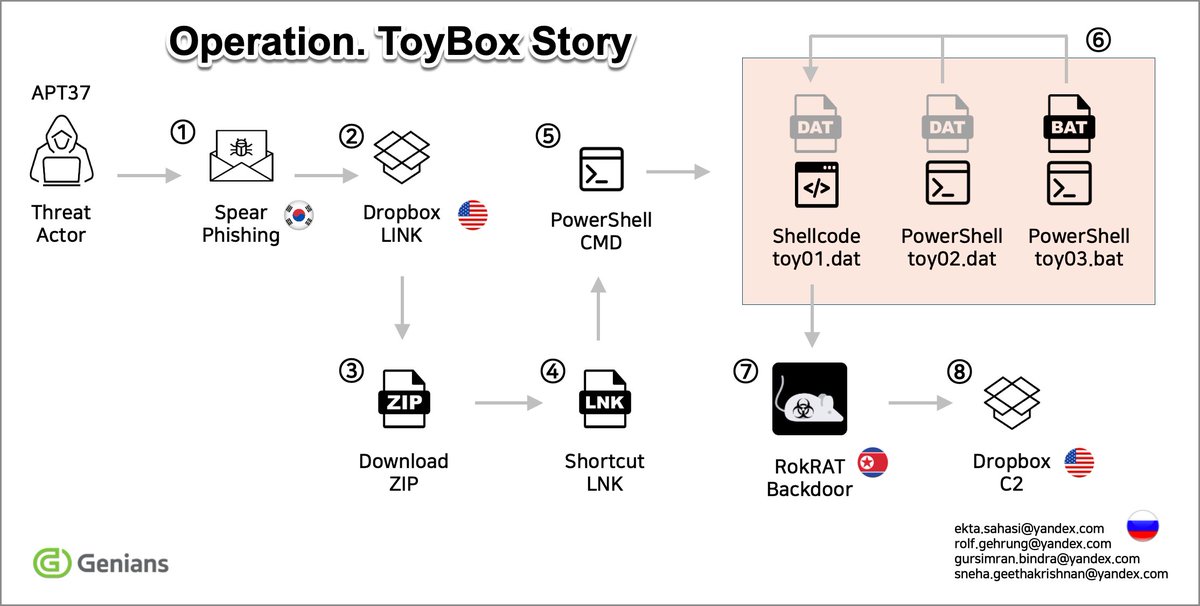
#NorthKorea #APT37 Analysis of APT37 Attack Case Disguised as a Think Tank for National Security Strategy in South Korea (Operation. ToyBox Story) genians.co.kr/en/blog/threat…
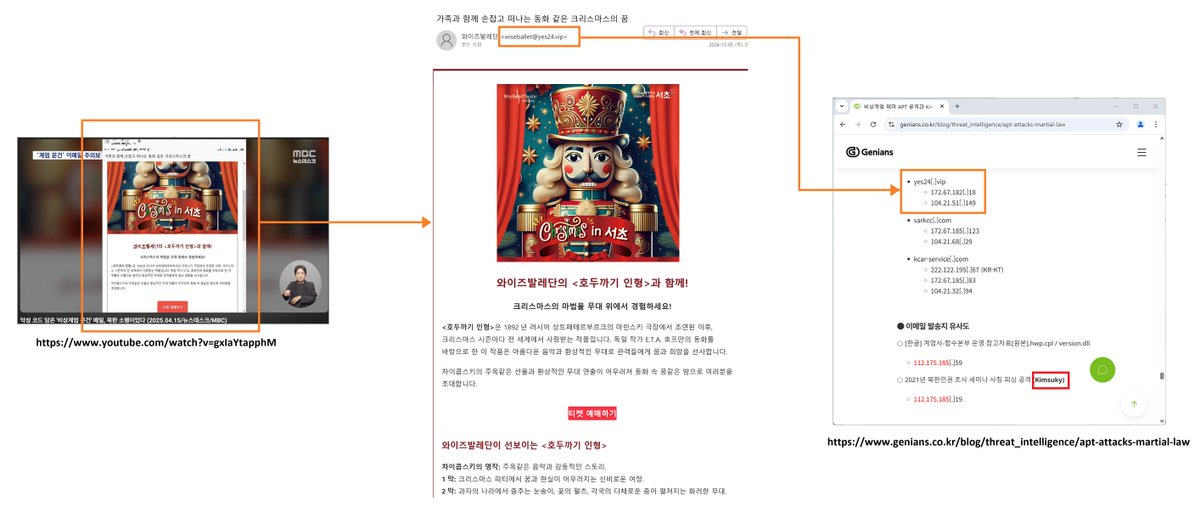
#NorthKorea - Youtube : youtube.com/watch?v=gxIaYt… - TI Report : genians.co.kr/blog/threat_in…
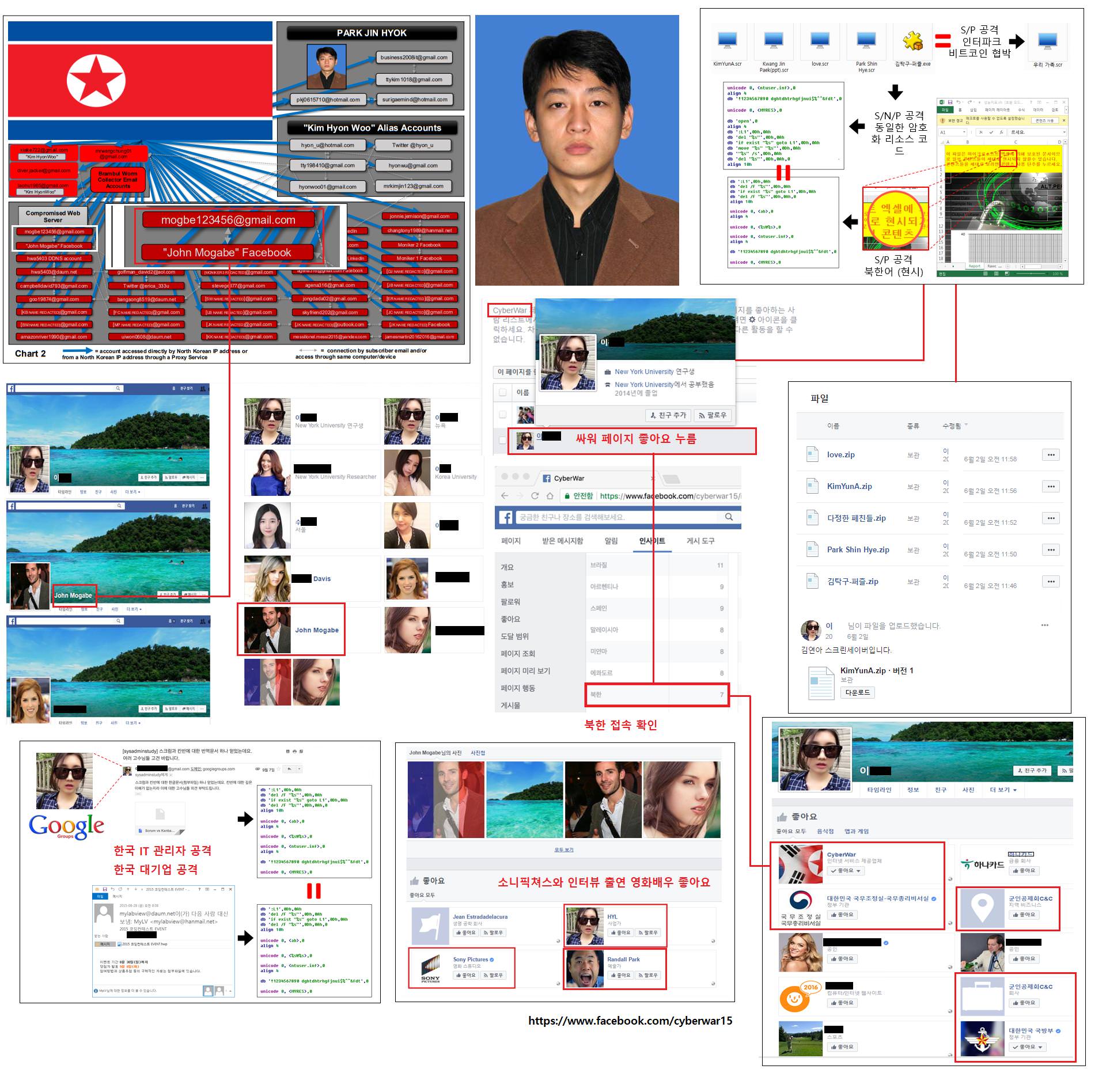
#NorthKorea #Konni Threat actors using North Korean language genians.co.kr/blog/threat_in…
linkedin.com/in/rolfgehrung/ linkedin.com/in/esahasi/ linkedin.com/in/gursimranbi… linkedin.com/in/sneha-geeth…
#NorthKorea #Kimsuky genians.co.kr/blog/threat_in… 9e94126e8a26efd10b2a5b179d64be90 35b4f28dd2d50dbf48e5c63c3ef5efb7 66e8096b9b061550314a82654ce0fabd 71d5270d1a165bb6dec144e16089450d
🇰🇵 2 more #Lazarus JS Files Uncovered linked to #ByBit $1.5B #Hack Series! MD5: 9e96a53a50d4f046696e976e60332ac0 MD5: 98303ede11d912877ca7c83e8db9b4a7 Source: github.com/TheRavenFile/D… #bybit #crypto #cryptocurrency #blockchain #cyberattack #lazarus #northkorea #ether #bitcoin
#NorthKorea #APT37 genians.co.kr/blog/threat_in… 1a70a013a56673f25738cf145928d0f5 1c3bb05a03834f56b0285788d988aae4 1d736803cb8fbb910dc0150087530de7 1fcfea1ed7f0da272d37eff49371fcf0 2c24f8fa2654aa2675566f7d6b0f5b12
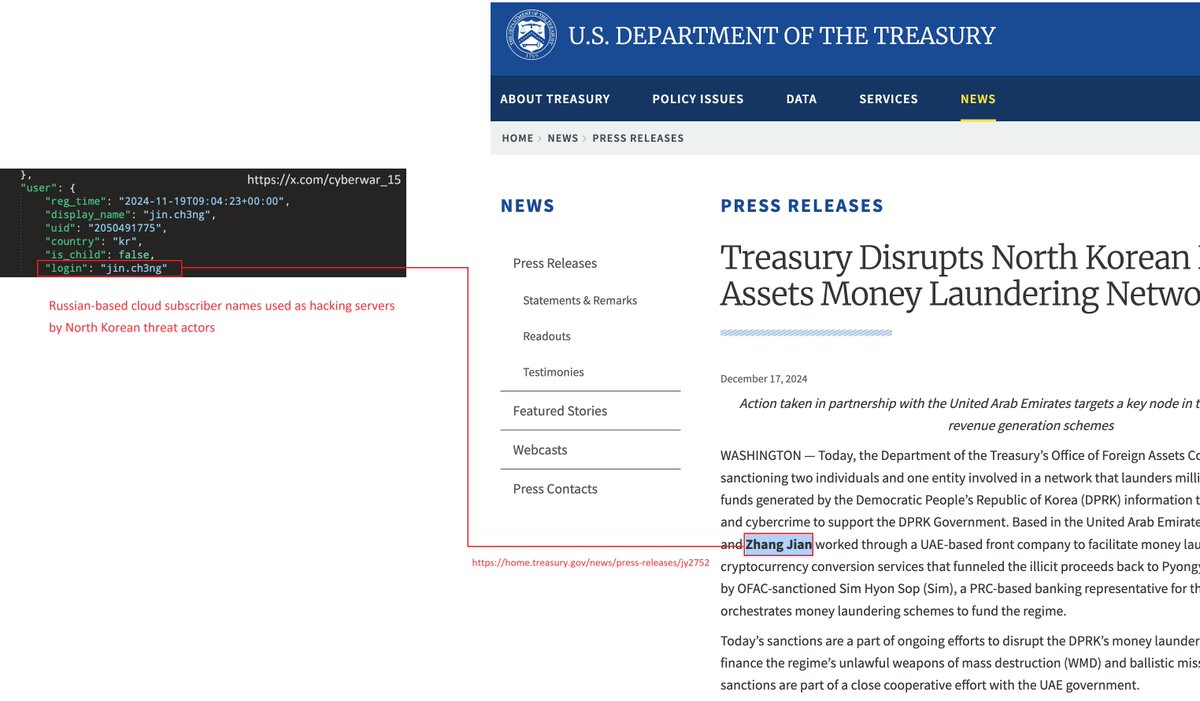
#NorthKorea #similar Jin.ch3ng Zhang Jian home.treasury.gov/news/press-rel…
#NorthKorea Everything has a meaning and we must understand it. NorthKorea = 북한 DPRK = 조선민주주의인민공화국
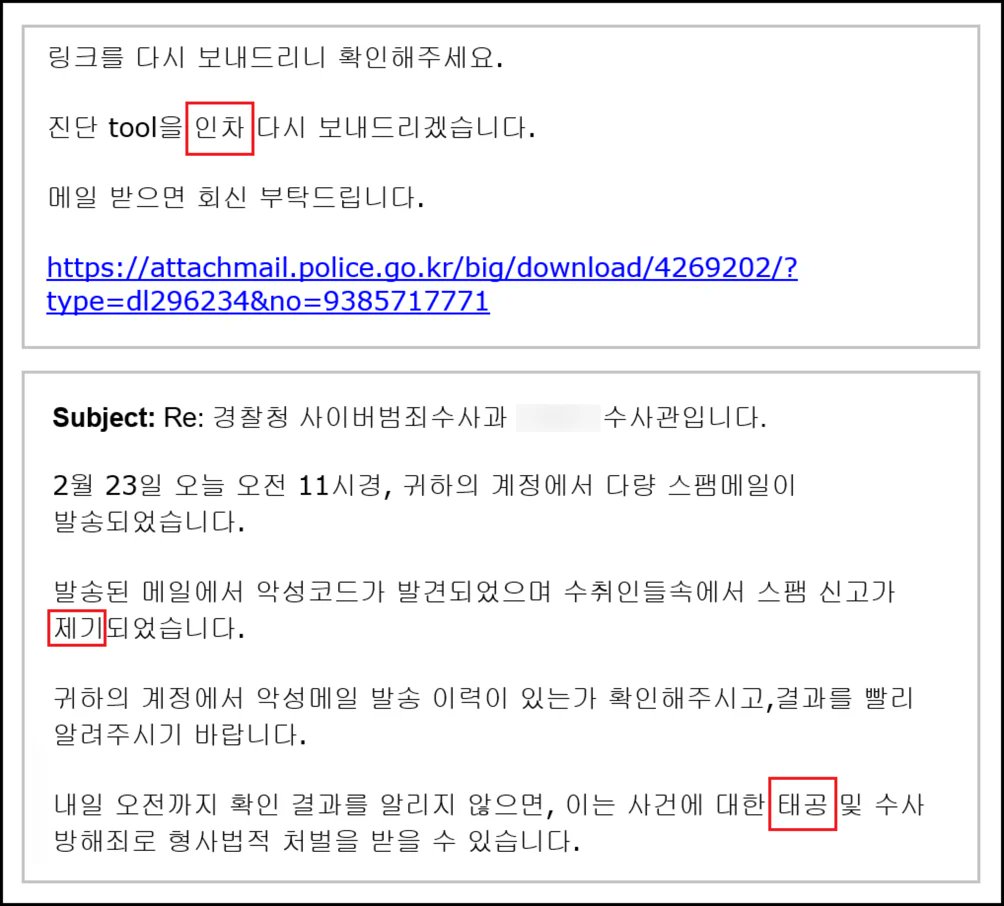
#NorthKorea #APT This is the screen used by the North Korean threat actor. It mentions South Korea's President Yoon Seok-yeol's martial law.

#NorthKorea #Kimsuky #C2 #DE - atlanwelt[.]de - 167.235.230[.]60
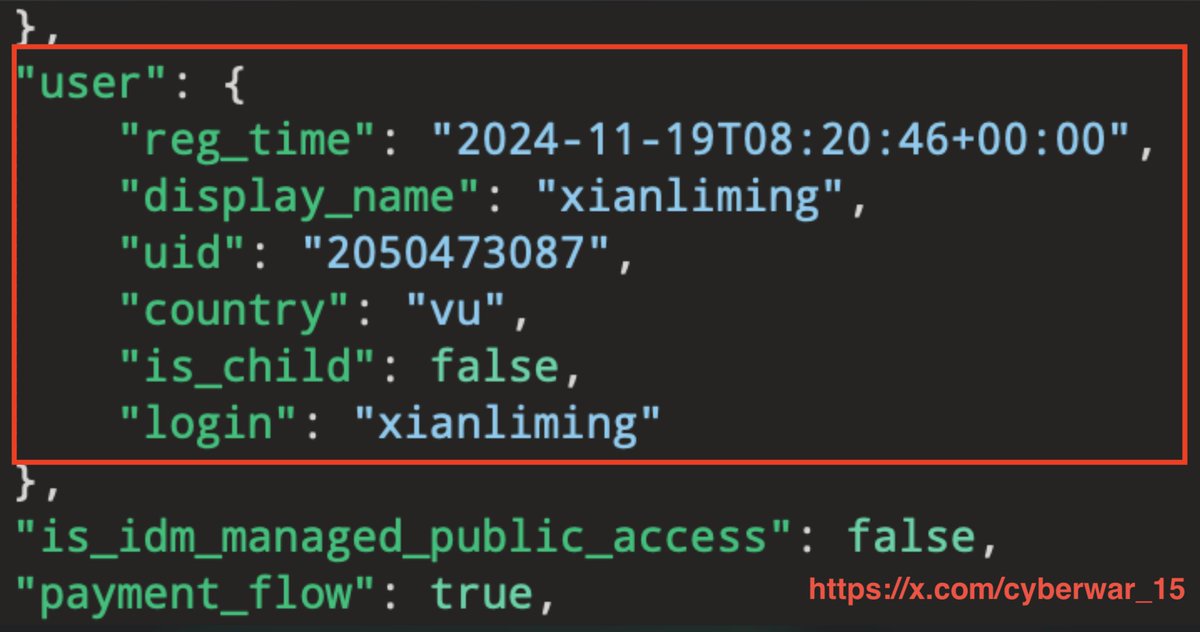
#NorthKorea #APT #xianliming #China #Russia #Vanuatu North Korean threat actors have set up infrastructure in Russia using Chinese login names. The vu country code is Vanuatu. - xianliming - 西安立明
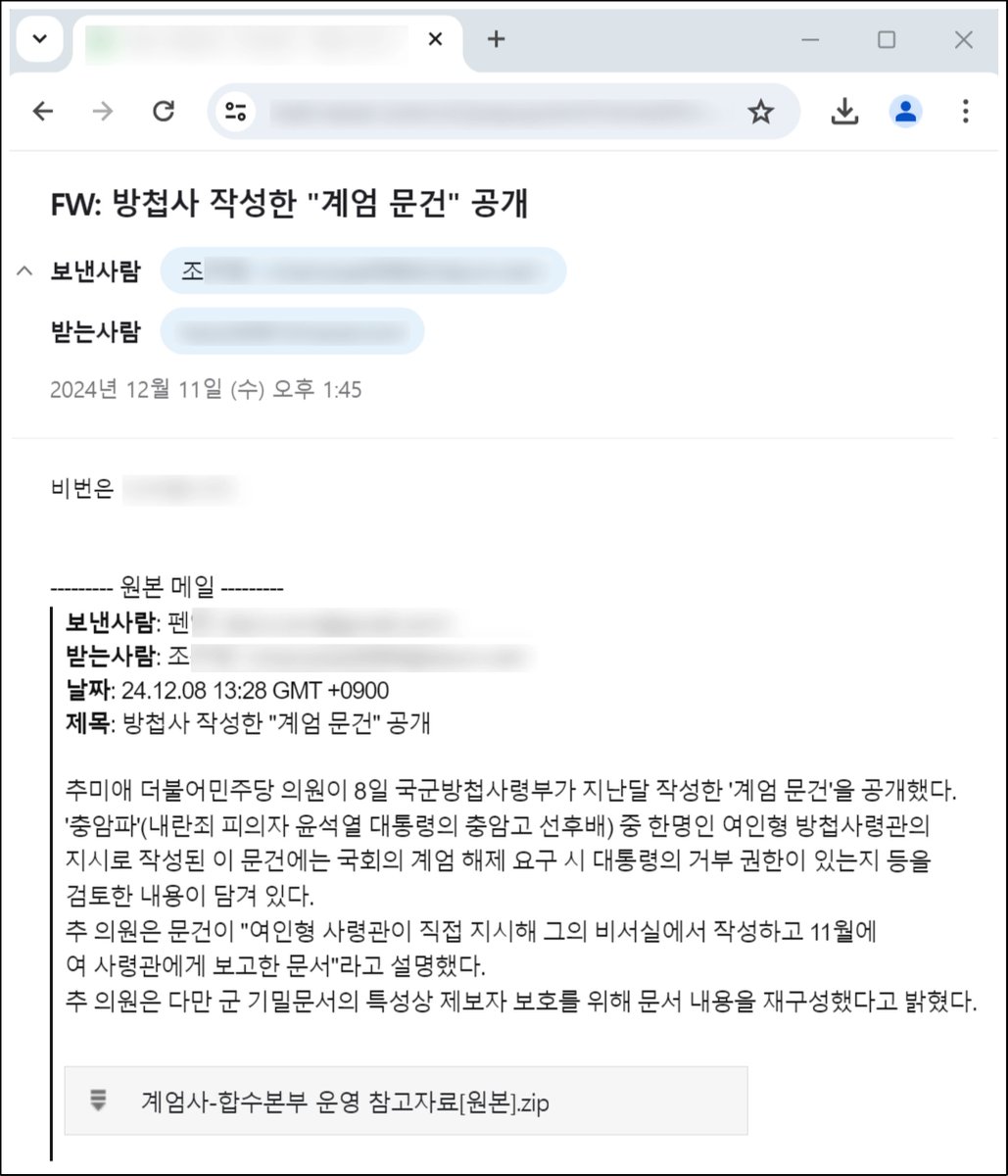
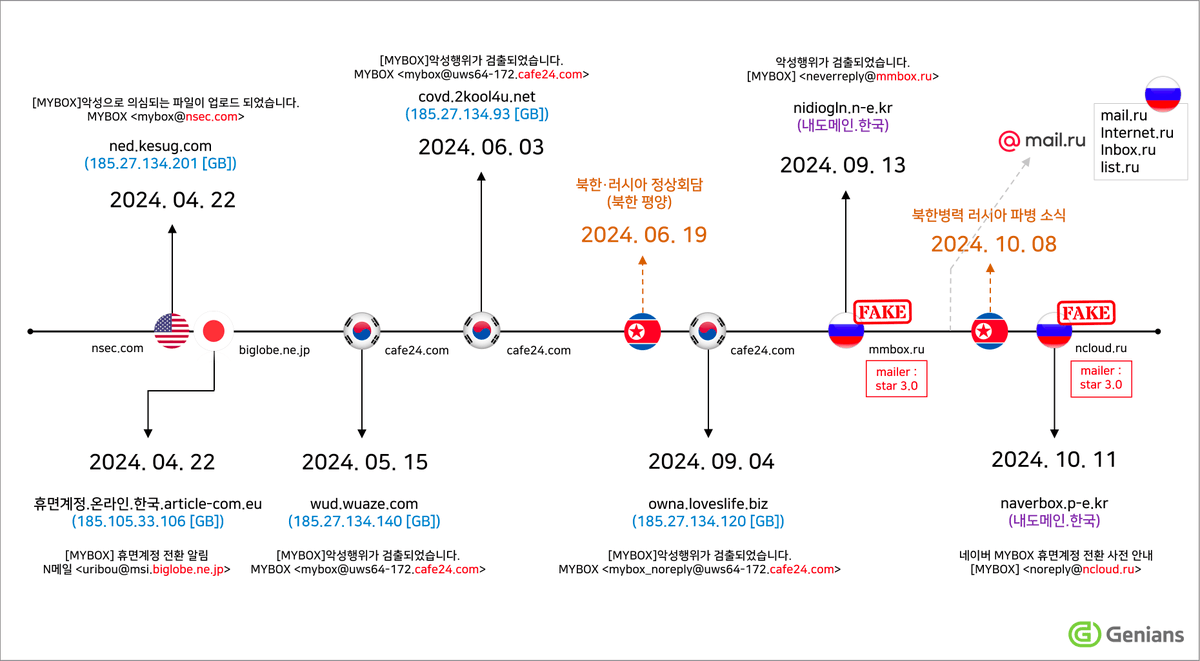
#NorthKorea #Kimsuky #Russian The timing of North Korea's attack on the Russian email service is interesting. North Korea uses Russian emails for cyberattacks before and after the North Korea-Russia summit and the North Koreans send troops to Russia. genians.co.kr/blog/threat_in…
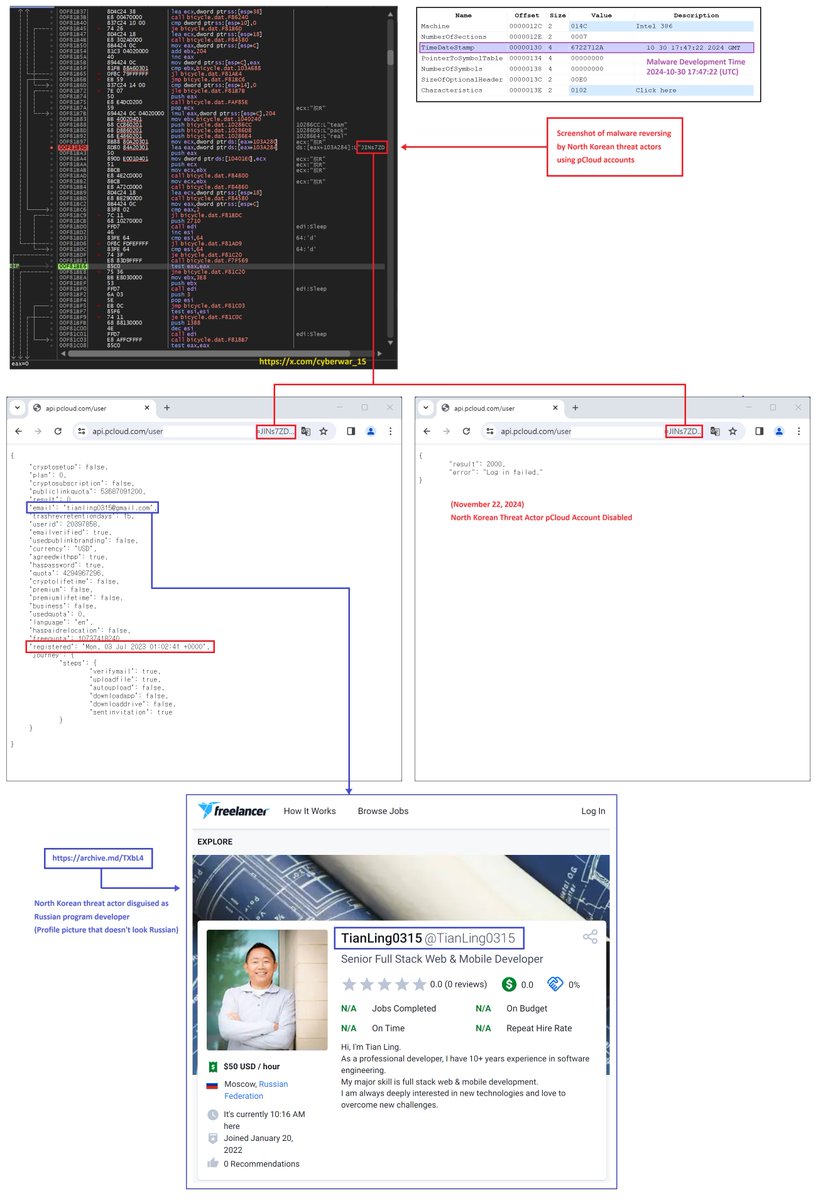
#North_Korea #Threat_Actor #IT_Worker #Fake_Russian_Freelancer #TianLing0315 A pCloud account used by a North Korean threat actor for a long time has been blocked. North Korean threat actors operate under cover of identity, much like Russian program developers.