Cube0x0
@cube0x0
http://0xC2.io -founder 🇸🇪
I just published a blog post where I try to explain and demystify Kerberos relay attacks. I hope it’s a good and comprehensive starting point for anyone looking to learn more about this topic. ➡️decoder.cloud/2025/04/24/fro…
If you wanna do it in c#, merge this with the og krbrelay https://github[.]com/CICADA8-Research/RemoteKrbRelay
RemoteMonologue - A Windows credential harvesting attack that leverages the Interactive User RunAs key and coerces NTLM authentications via DCOM. Remotely compromise users without moving laterally or touching LSASS. Hope you enjoy the blog & tool drop 🤟 ibm.com/think/x-force/…
I asked myself, how difficult would it be to run a 0xC2 agent in a non-rooted Samsung phone, via an APK installation, and use it for lateral movement Turns out, not very difficult at all
M'm glad to release the tool I have been working hard on the last month: #KrbRelayEx A Kerberos relay & forwarder for MiTM attacks! >Relays Kerberos AP-REQ tickets >Manages multiple SMB consoles >Works on Win& Linux with .NET 8.0 >... GitHub: github.com/decoder-it/Krb…
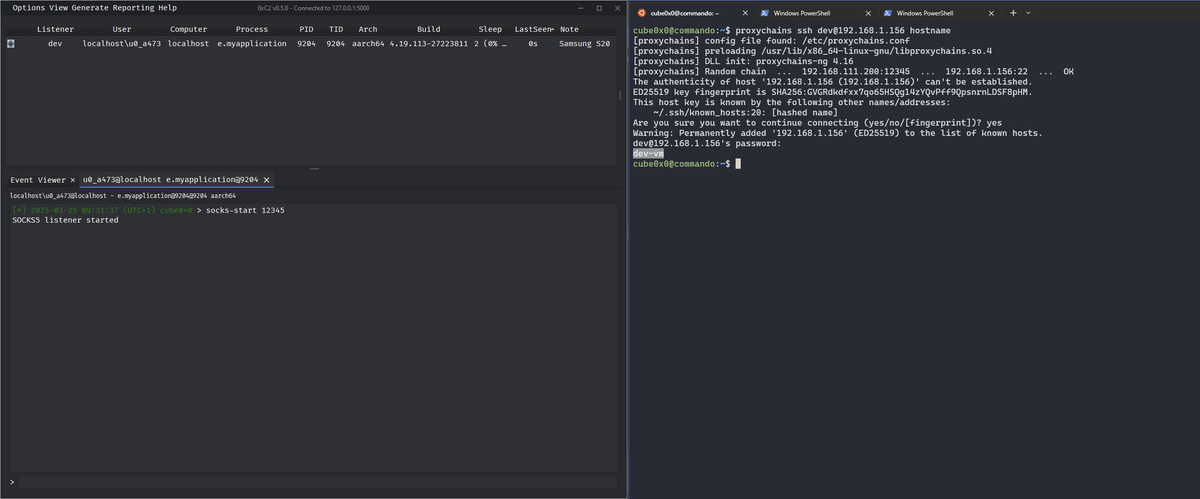
I have received a few questions about reusing existing open-source and in-house BOFs in 0xC2 so I am leaving it here for visibility. Yes the 0xC2 Windows agent has a backward-compatible layer so you can reuse your existing object file tools after converting the Sleep script to…
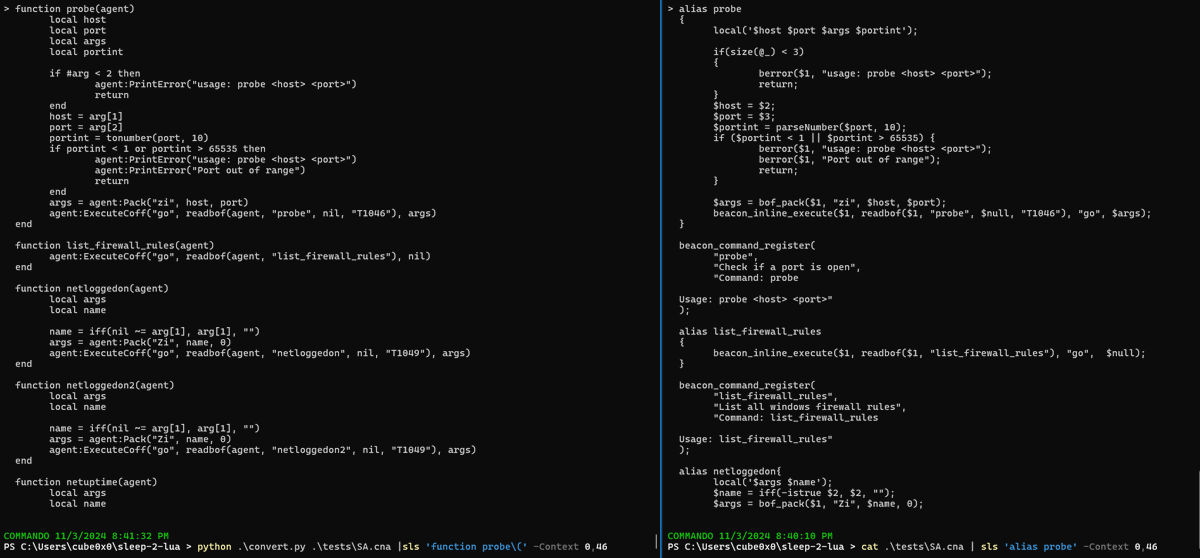
Don't we all get to the point where all you want to do is capture and relay NTLM and Kerberos authentications in a BOF? It's just faster to write a capture & relaying framework in C for ntlm, kerberos, dcom, smb, http, mssql with native Windows support than fixing impacket.…

Is Kerberos relaying so limited? I'd say no, thanks to @tiraniddo CredMarshalTargetInfo trick. In this case, I'm relaying SMB to HTTP (ADCS) with a modified version of @cube0x0 krbrelay using DFSCoerce and PetitPotam - classic ESC8 attack with Kerberos, no DCOM involved ;)
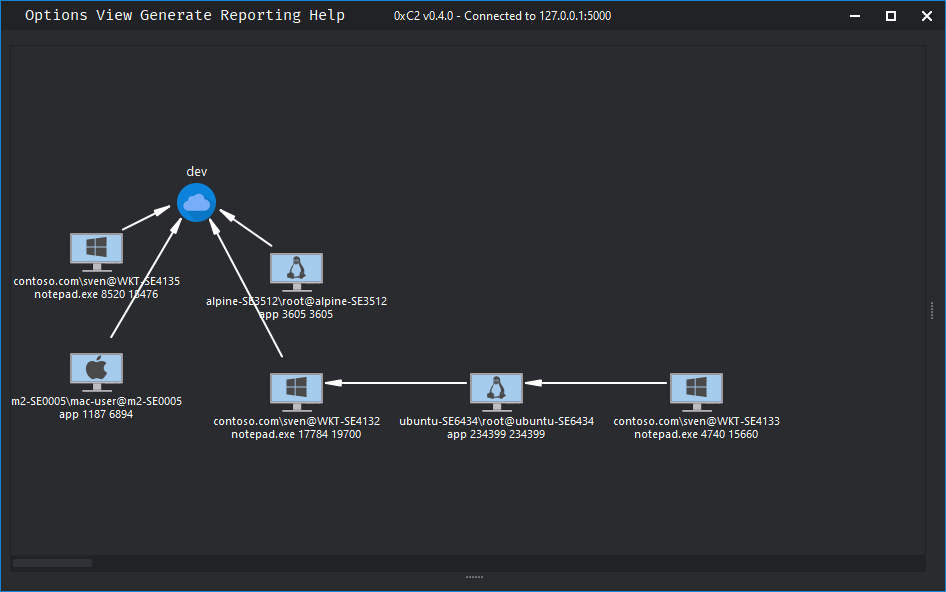
0xC2 is now available and the site has been updated with a brief introduction 0xc2.io/posts/introduc…
Red Teaming in the age of EDR: Evasion of Endpoint Detection Through Malware Virtualisation blog.fox-it.com/2024/09/25/red…
Is your team actively using github.com/WithSecureLabs… for external communication during red team engagements?
First blog! Reversing a VPN client to hijack sessions. rotarydrone.medium.com/decrypting-and…
Over a year ago, I left my position at WithSecure to start a new journey, create something new, and do my own thing. Today, I'm excited to publicly announce what I've been working on all this time. Introducing 0xC2, a cross-platform C2 framework targeting Windows, Linux, and…
Since I'm 6 drinks in for 20 bucks, let me tell you all about the story of how the first Microsoft Office 2007 vulnerability was discovered, or how it wasn't. This was a story I was gonna save for a book but fuck it, I ain't gonna write it anyways.
Time to be terrified. I've just dropped my Okta Terrify tool which I demonstrated as part of my @BSidesCymru talk last week. You can now backdoor compromised Okta accounts via Windows Okta Verify using attacker controlled passwordless keys. Enjoy - github.com/CCob/okta-terr…
🔥
POC for #SilverPotato utilizing Kerberos relay vs SMB ;) Starting from @cube0x0 great krbrelay tool with extra layer of complexity to get the SilverPotato beast working.. Still in the rough but will publish soon :-)
Taking a cue from @D1iv3 and @decoder_it's work on inducing authentication out of remote DCOM I thought I'd quickly write up a post about getting Kerberos authentication out of the initial OXID resolving call. tiraniddo.dev/2024/04/relayi…
Interested in red team operations using almost all internal tooling against some of the hardest companies in the world? Love coding on the fly? TrustedSec Targeted Operations may be for you. Shoot me a DM.
ADCS: Coercing NTLM Auth just for fun (or maybe for profit?)