
Bill Marczak
@billmarczak
senior researcher @citizenlab, phd @UCBerkeley, co-founder @BHWatch. كلنا راجعين
Turns out you can just hack any train in the USA and take control over the brakes. This is CVE-2025-1727 and it took me 12 years to get this published. This vulnerability is still not patched. Here's the story:
Perhaps one of the most badass CVE's I've ever seen from @midwestneil 💪😤 cisa.gov/news-events/ic…
Interesting work, though attribution solely based on "timezone" of "attacker activity" feels somewhat lacking (especially in 2025)... 9PM to 6AM Beijing time seems like the precise time that _any_ adversary of China would seek to attack China, no? x.com/RedDrip7/statu…
At the recently held CYDES 2025, we disclosed #APT group #NightEagle (APT-Q-95). This threat group has been targeting high-tech industries for a long time, including chip semiconductors, AI/GPT and other fields. Actors used an unknown Exchange exploit chain. PPT: #IOCs #APT
At the recently held CYDES 2025, we disclosed #APT group #NightEagle (APT-Q-95). This threat group has been targeting high-tech industries for a long time, including chip semiconductors, AI/GPT and other fields. Actors used an unknown Exchange exploit chain. PPT: #IOCs #APT
If you’re at @reconmtl come watch @droethlisberger and me talk (Sun 10:00AM) about a 2017 iOS persistence exploit used by NSO's Pegasus (and, interestingly, other threat actors too)! cfp.recon.cx/recon-2025/tal…

The siren has been sounded. Citizens and residents are urged to remain calm and head to the nearest safe place
Remember when Meta published about an ITW FreeType OOB write vuln (CVE-2025-27363) in March? Turns out, Meta links this vuln to an exploit from spyware vendor Paragon securityweek.com/freetype-zero-…

Zero-Day used by Stealth Falcon APT group in a spear-phishing campaign: 💥 .URL file exploitation (assigned CVE-2025-33053) 🧰 Custom Mythic implants, LOLBins, and custom payloads 🌍 High-profile targets across the Middle East and Africa research.checkpoint.com/2025/stealth-f…
BOMBSHELL: The Pentagon helped spread UFO myths for a generation. When a new DoD investigation dug up the military’s role, the Air Force pushed for a coverup. With the mighty @aviswanatha wsj.com/articles/WP-WS…
Wow, big punitive damages award (US$ 168M) against NSO Group in the WhatsApp "missed call hack" case. NSO CEO was in Oakland for the verdict. courthousenews.com/meta-wins-168-…

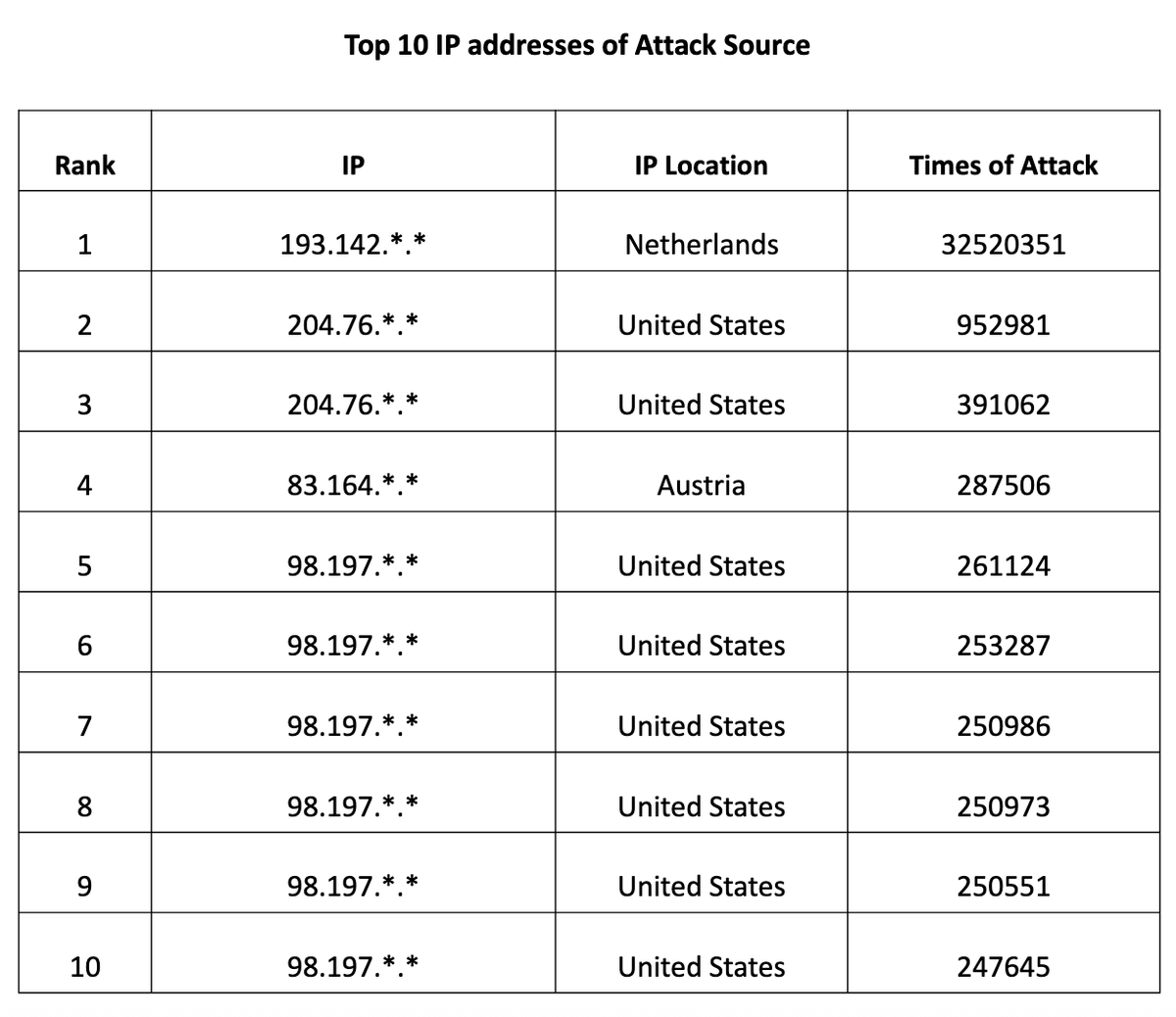
The China/NSA winter games "hacking" report from CVERC does not inspire confidence that there's solid technical data for a US Government attribution. I also wonder if this level of activity is above baseline for what an average Chinese IP address can expect to receive?


Very cool writeup of NSO's (2023) #BLASTPASS exploit, which (finally!) explores the precise reason why the WebP exploit was included in a .pkpass (i.e., .zip) container. (I still wonder why Triangulation was using a .watchface though...) x.com/i41nbeer/statu…
My writeup of the 2023 NSO in-the-wild iOS zero-click BLASTDOOR webp exploit: Blasting Past Webp - googleprojectzero.blogspot.com/2025/03/blasti…