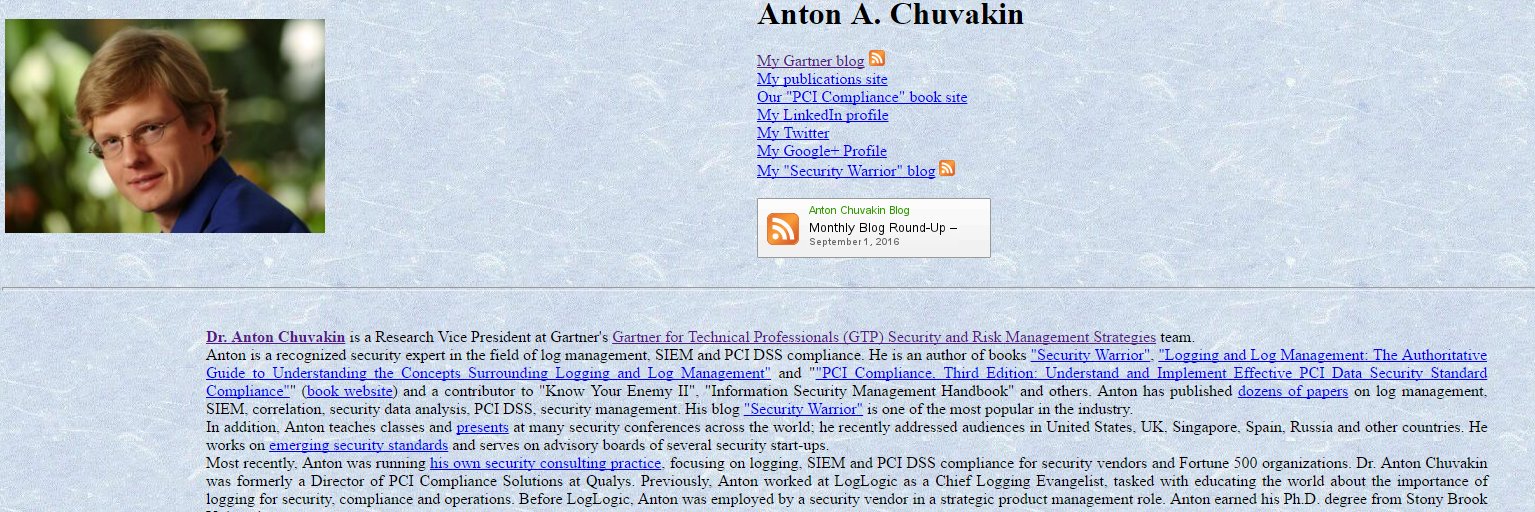
Dr. Anton Chuvakin
@anton_chuvakin
Information security - #SIEM, #DFIR, #EDR formerly at Gartner! Now @GoogleCloud Office of the #CISO; host of @CloudSecPodcast http://infosec.exchange/@anton_chuvakin
Cloud Security Podcast by Google #CloudSecPodcast #GoogleCloud #CloudSecurity Website: cloud.withgoogle.com/cloudsecurity/… Google Podcasts: podcasts.google.com/feed/aHR0cHM6L… Apple Podcasts / iTunes: podcasts.apple.com/us/podcast/clo… Spotify: open.spotify.com/show/12WPC7aW5… Twitter:
“The mission of Google and Search has never felt more current.” 👈 Yes. This.
1/2 Had an awesome chat with @OfficialLoganK on the Release Notes podcast this week about what it takes to build a frontier AI search experience that helps billions of people truly ask anything. We’re shipping a lot in Search right now so it was great to pause and reflect on the…
For decades one of the most exploited vulnerabilities has been “misconfigured software.” Whether that was “+ +” in an .rhosts file, or bad access controls on an S3 bucket, or unauthenticated database access on the open web, it is all still hacking.
Calling the Tea hack a "hack" is honestly a stretch. They put everything in a publicly accessible DB. Not in the "they didn't encrypt" sense, in the "literally publicly accessible URL" sense. The "hack" is downloading the .jpg files from a publicly accessible URL.
Use LLMs where they shine. To create, not calculate. To communicate, not control. Where flexibility matters more than precision. This may sound cliche, but they're here to augment, not replace. They're the kind of worker that's highly dependent on you to lead. (4/n)
There's a great line from Dragon Age Inquisition I try to live by: "Faith is made stronger by facing doubt. Untested, it is nothing." Facing challenges to your perspective allows you to confirm it, grow it, or change it. It is more than necessary, it's mandatory.
Guise it’s NOT a hack!!!!! They just sent an http GET request!!!!
I once joined a new org where the IT team told me were saving screenshots of user’s desktops taken periodically via a DLP app, to an s3 bucket. I asked them to immediately turn off that feature and delete the bucket. There was no reason for it other than the DLP tool offered it,…
Part of the job as a cybersecurity professional is in fact arguing to purge and not log information about your customers. Data is not oil. It's risk.
Part of the job as a cybersecurity professional is in fact arguing to purge and not log information about your customers. Data is not oil. It's risk.
Tea app has allegedly been hacked, they used a public bucket to store drivers licenses of users and someone has downloaded them. Tea was likely a vibe slop app
I don't know you, but a +32% growth in Google Cloud is insane. AI investments are obviously paying off. Google demonstrates itself as a leader in AI for cloud services. I'm long $GOOG $GOOGL, 3rd highest holding.
Remember when @KnowBe4 put out that blog post about inadvertently hiring a North Korean criminal who started uploading malware to the network immediately! They caught one of the US citizens involved in the attacks on the hiring system at 300+ US companies.
Arizona Woman Sentenced for $17M Information Technology Worker Fraud Scheme that Generated Revenue for North Korea fbi.gov/news/press-rel… @FBIPhoenix
If you listen to #podcasts, and have these choices, what do you pick?
I’m building a new team at @GoogleDeepMind to work on Open-Ended Discovery! We’re looking for strong Research Scientists and Research Engineers to help us push the frontier of autonomously discovering novel artifacts such as new knowledge, capabilities, or algorithms, in an…
"Organizations need to build change muscles within every function and every business across the enterprise. It’s not just about upskilling; it’s the constant questioning of why we do what we do, every single day." In collaboration with @EYNews: theinformation.com/articles/four-…
There are now parallels with AI: We have this tool where a dev (using AI coding tools) could produce ~10x as much as code as before. And some say demand for devs will decrease. Look at offshoring: demand for devs should have decreased for devs in the West. But it increased!
We are looking for a guest on the topic of VULNERABILITY MANAGEMENT. Got ideas?
Waiting for the first reported occurrence of "But is your AI agent PCI DSS compliant?" #random :)
We're launching an "AI psychiatry" team as part of interpretability efforts at Anthropic! We'll be researching phenomena like model personas, motivations, and situational awareness, and how they lead to spooky/unhinged behaviors. We're hiring - join us! job-boards.greenhouse.io/anthropic/jobs…
Join @rmedranollamas and #Swapnil Haria to explore how AI agents are changing the #SRE role, from summarizing alerts to proactively preventing outages. Explore the interplay between human experts and AI capabilities in the latest episode of Prodcast! google.smh.re/51pU
A bug bounty program is economically beneficial to a firm when the firm has low in-house efficiency in finding a vulnerability *or* when the firm faces a high proportion of coopetitive hackers (bug reporters who would otherwise pose a security risk by misusing vulnerability…