Alexandre Borges
@ale_sp_brazil
Vulnerability Researcher and Exploit Developer.
To date, I have published 15 articles (1045 pages) with the strict goal of helping the cybersecurity community. ERS (439 pages, so far): [+] ERS 05: exploitreversing.com/2025/03/12/exp… [+] ERS 04: exploitreversing.com/2025/02/04/exp… [+] ERS 03: exploitreversing.com/2025/01/22/exp… [+] ERS 02:…
Hey #DFIR #ThreatHunting community. Are there folks who would be interested in doing a beta test for the "📈 Intro to Event Tracing for Windows (ETW)" course? I just want to make sure everything is good before releasing it to the public. Please RT/share labs.cyber5w.com/courses/dd4221…
Understand the SharePoint RCE: Exploitations, Detections, and Mitigations: akamai.com/blog/security-… #sharepoint #cve #rce #cybersecurity #informationsecurity #microsoft #exploitation #vulnerability
💡 Just a small tool tip for the best parsing and verifying of embedded #authenticode signatures (certificates) in #PE files: just use the #signify tool - trust me (recommended to use the code in examples folder): github.com/ralphje/signify ☑️ It gives you the most detailed verbose…
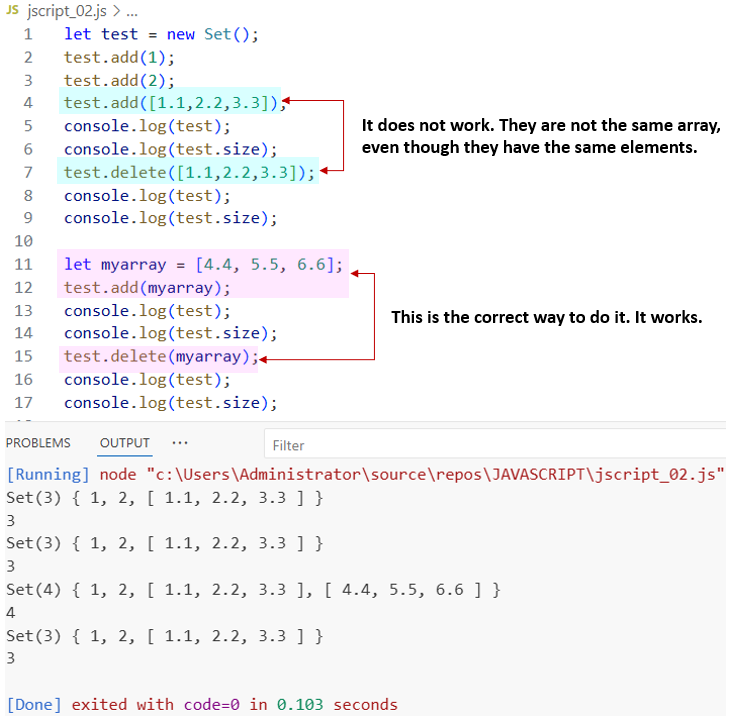
Recently I've seen a PoC trying to exploit V8 and, in the middle of the code, there was a simple mistake: the author was trying to delete a previously added array element into a Set, and later the apparently same array element would be deleted, but using a wrong approach. Of…
We've published the research materials. Two proofs of concept required modifications after the blog post's publication. For code 1, we replaced the reallocation technique, moving from the keyring subsystem to the VSOCK networking protocol using sendmsg(). Additionally, code 3…
We wrote a blog post about a Linux kernel vulnerability we reported to Red Hat in July 2024. The vulnerability had been fixed upstream a year before, but Red Hat and derivatives distributions didn't backport the patch. It was assigned the CVE-2023-52922 after we reported it.
101 Chrome Exploitation — Part 0: Preface We are starting a new series on modern browsers' architecture and their exploitation using Chrome as an example. Readers will learn how browser subsystems are implemented, how their security is ensured and how it is violated with…
📣 IDA 9.2 Beta is here! This release is packed with UI upgrades, smarter analysis, and expanded architecture support. ➥ Already a Beta user? Grab it now. ➥ Not enrolled? Sign up today. eu1.hubs.ly/H0lS6nv0
Lifting Binaries, Part 0: Devirtualizing VMProtect and Themida: It's Just Flattening: nac-l.github.io/2025/01/25/lif… #reverseengineering #cybersecurity #vmprotect #informationsecurity #infosec #binary #malwareanalysis #packers
One of our current intern, @goatmilkkk shared his Chrome-atic escape adventure using CVE-2024-30088 Epic obstacles documented in it too! starlabs.sg/blog/2025/07-f…
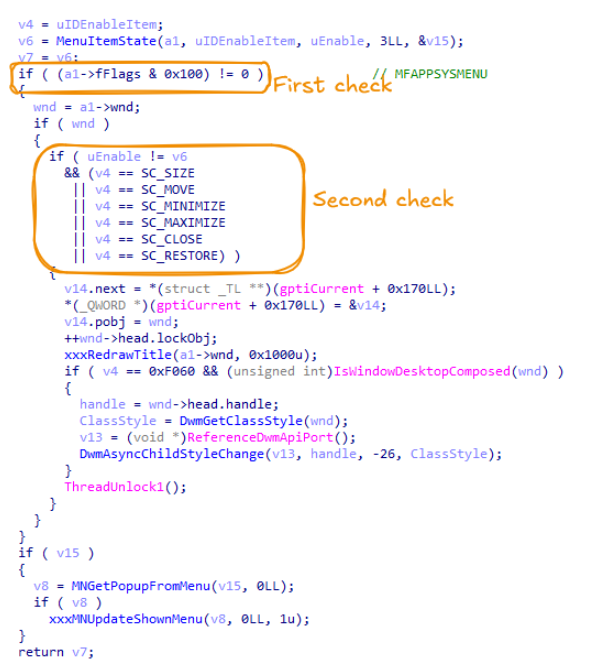
Win32k that we lost. In details writeup about CVE-2023-29336 (written by Sergey Tarasov @immortalp0ny) : deadprogrammers.club/posts/in-detai… #win32k #vulnerability #exploitation #exploit #informationsecurity
Today we released write up about vulnerability that I found and which was patched recently in NTFS.sys CVE-2025-49689. Enjoy! swarm.ptsecurity.com/buried-in-the-…
👨💻 Today we want to highlight some of the researchers and analysts who consistently move the #cybersecurity industry forward. From sharp threat analyses to smart defense tips, these experts are worth following. 💡 Here’s the list, in no specific order: @UK_Daniel_Card…
CVE-2023-52927 - Turning a Forgotten Syzkaller Report into kCTF Exploit (authored by @seadragnol): seadragnol.github.io/posts/CVE-2023… #cve #exploit #exploitation #vulnerability #linux #ctf #kctf
Just published a new issues of .NET R&D Digest! Thanks to @unmeshjoshi, @martinfowler, @andrewlocknet, @meziantou, @DamianEdwards, @STeplyakov and other great authors for their amazing content! olegkarasik.wordpress.com/2025/07/04/net… #dotnet
Mini Writeup of CVE-2025-6554. POC by @DarkNavyOrg. All errors in writeup my own. gist.github.com/mistymntncop/3…
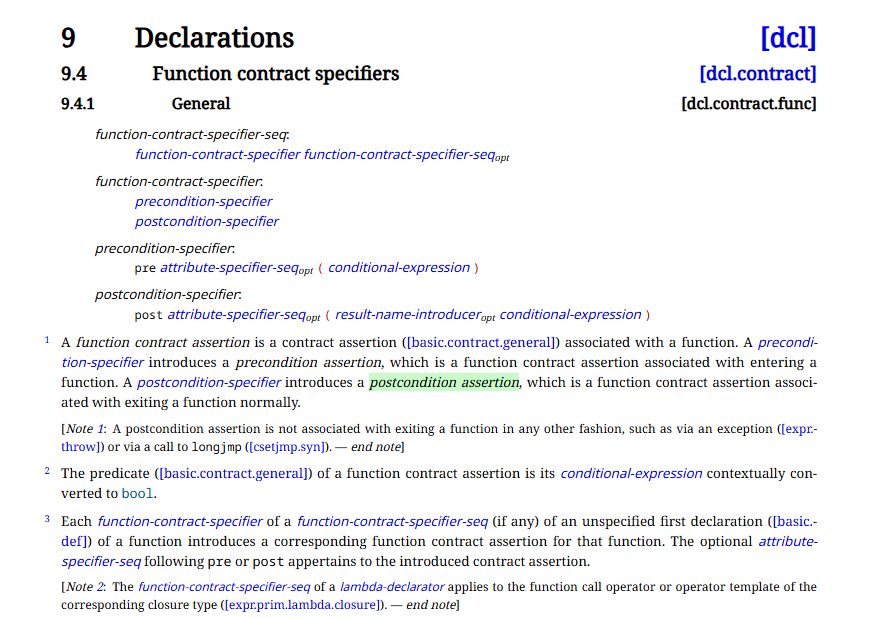
C++ exceptions are not good for performance and leave a heavy memory footprint. Finally, C++ contracts (preconditions, postconditions and contract assertions), which should have become standard since C++12 and C++20, will be included in C++26. C++ contracts allows to remove tons…