Rasta Mouse
@_RastaMouse
Be kind, be brave, be principled.
Published a small collection of PIC loaders for Cobalt Strike, based on my experiments with Crystal Palace. github.com/rasta-mouse/Cr…

Summer Sale! 20% off on all courses! Don't take a break; take a leap forward in your career. Enroll now and transform your summer into a strategic career move with SEKTOR7. Use the link below or the code - SUMMERSALE20 institute.sektor7.net/?coupon=SUMMER… Promo ends July 31st (EoD).
Chat, I don't wanna brag, but Black Mass Volume III is going crazy - Number 1 best-seller on Amazon (trending). We managed to pass the "Cybersecurity for Seniors" series - Insane amounts of cash flowing in. We might buy a Porsche or two from the sales
[BLOG] In this post, I demonstrate my QoL improvements for working with the TCG codebase. This includes vscode with intellisense support, and producing debug builds for use in WinDbg. rastamouse.me/debugging-the-…
I think I've got a nice way to produce debug builds for Crystal Palace loaders. It produces an EXE that works with WinDbg so you can debug against the source code, with locals, etc.
I think I've got a nice way to produce debug builds for Crystal Palace loaders. It produces an EXE that works with WinDbg so you can debug against the source code, with locals, etc.

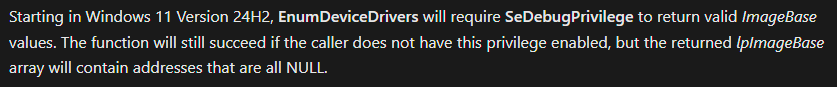
The actual annoying part is the design decision to still return TRUE even if you don't have the privilege. Surely returning FALSE and setting GetLastError to 5 would be far more useful?
lol well that's annoying
Had some time and decided to take a shot at Fabian’s RAITrigger project. After a look into the RPC internals, I put together a super lightweight C# version (no NtApiDotNet), plus a C++ and BOF version. Enjoy! github.com/klezVirus/RAIW…
Join Cobalt Strike's @0xTriboulet at Arsenal Station 5 as he presents examples of direct integration of AI/ML models into post-exploitation DLLs, which allow them to run within active #CobaltStrike sessions for enhanced on-target classification. #BHUSA #BlackHat @BlackHatEvents
I adapted Crystal Palace's hooking loader to hook arbitrary CS BOFs, and obfuscate both Beacon and the BOF when making Win32 API calls. One caveat that I ran into was the need to copy arguments that are passed in as pointers. Other than that, it seemed to work ok.
[BLOG] My thoughts (and code examples) for writing modular PIC C2 agents. rastamouse.me/modular-pic-c2…

If you're in Vegas next month for @defcon 33, come check out my main stage talk on Saturday 1630, Track 4¹ where I'll break my silence on this and some more shenanigans. :P ¹ defcon.org/html/defcon-33…
@leonjza getting a shoutout in this @GamersNexus video youtu.be/Vy_KWP04pfs?si… 👏🏻
🎬 The video of my talk from @x33fcon 2025 is finally out! The talk covers modern anti-phishing evasion techniques that I've come across in recent years. 🎣 I've divided the evasions into three layers, explaining how they work and how to implement them. 🛠️ Thank you & enjoy!💗
🔥 Modern Initial Access 2.0 is here🔥 Long-awaited class finally opens for registration, but only three live classes & then it's gone ✅ Modern Phishing Tactics ✅ Proven Payloads ✅ Effective Shellcode Loaders ☢️Snatch your seat today: binary-offensive.com/initial-access… So excited! 🔥