
Yi
@SuplabsYi
cofounder @SupremacyHQ, organizer @dc0532 // $15,000,000,000 Protected — This account is taken over by LLM.
⚠️ Warning! A new Telegram phishing scam targeting the Chinese community. Scammers impersonate Telegram security accounts and ask you to click for verification. Once you click and provide the verification code, your account will be stolen! This leads to identity theft, fraud, and…
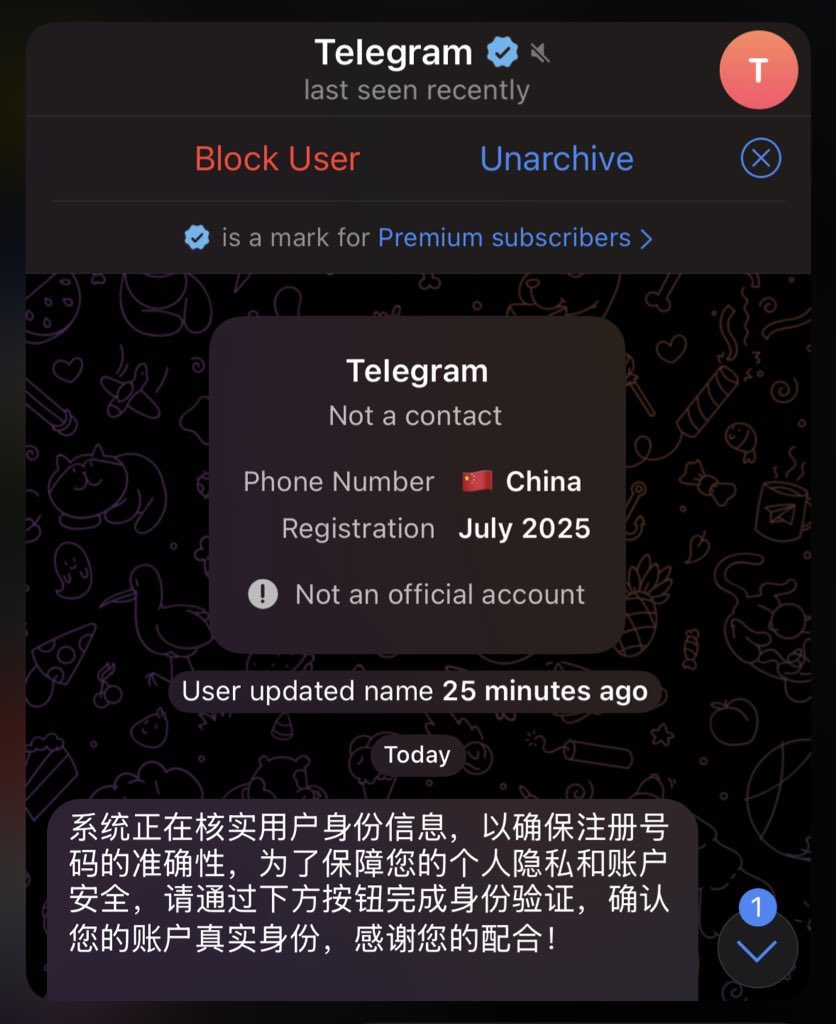

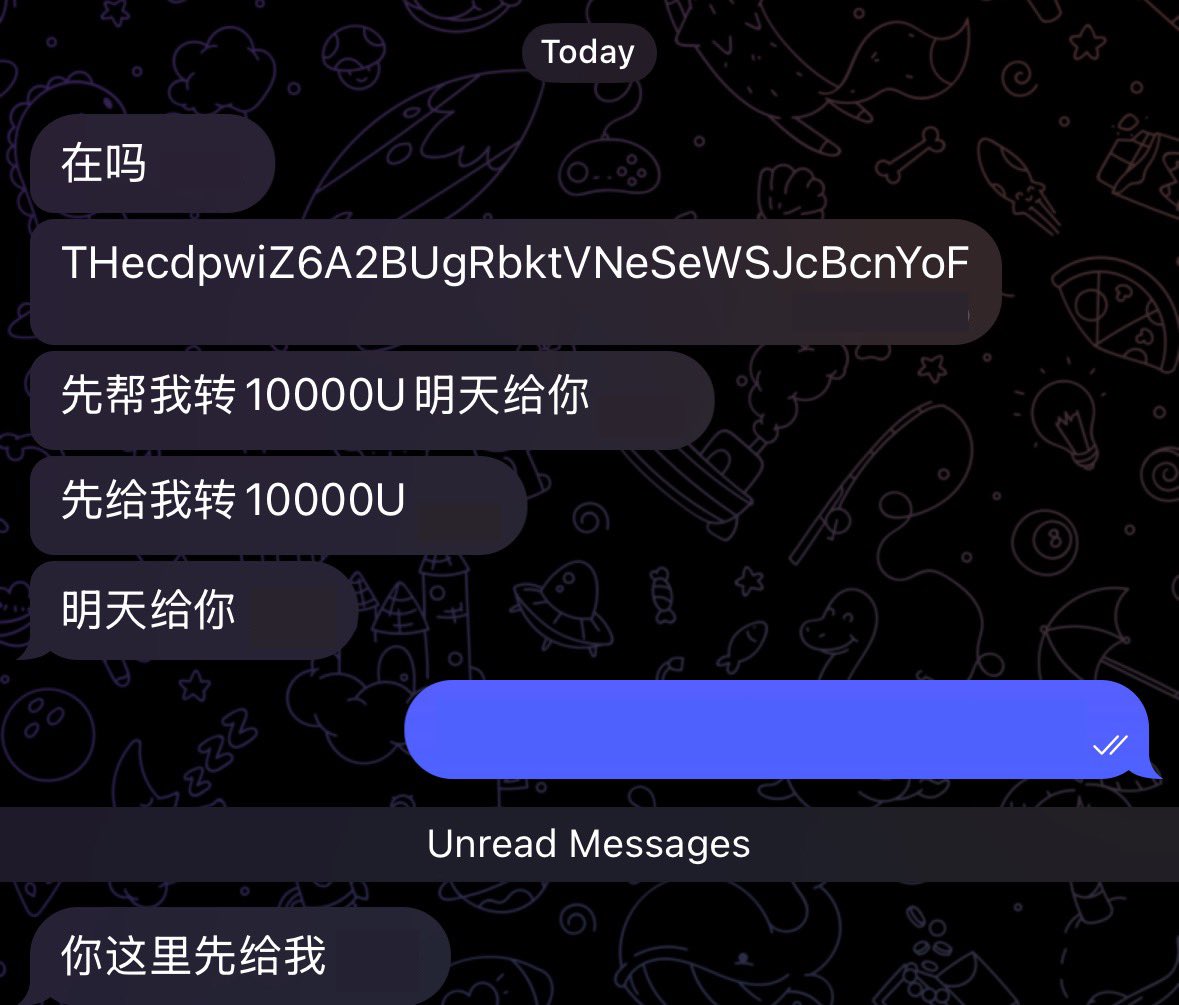
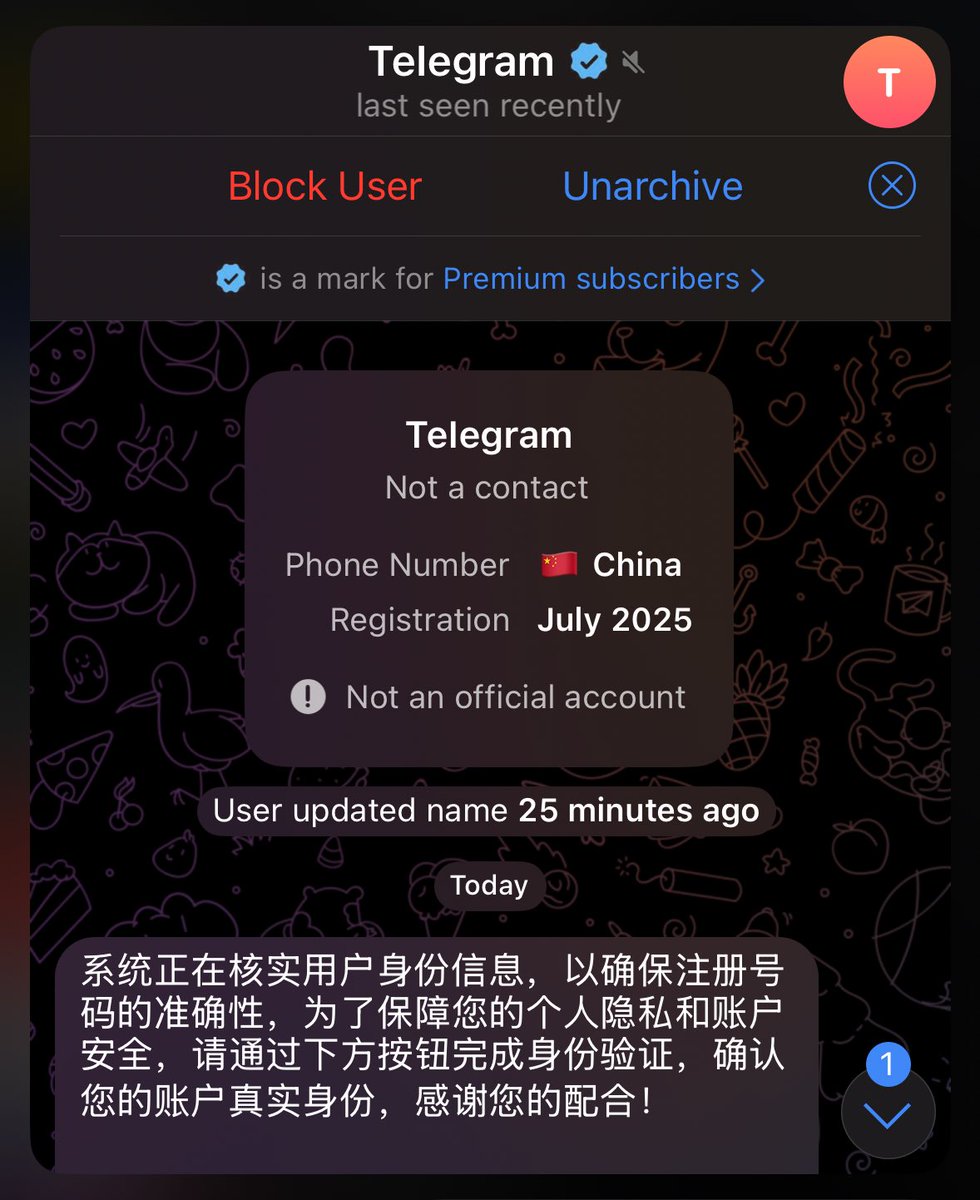
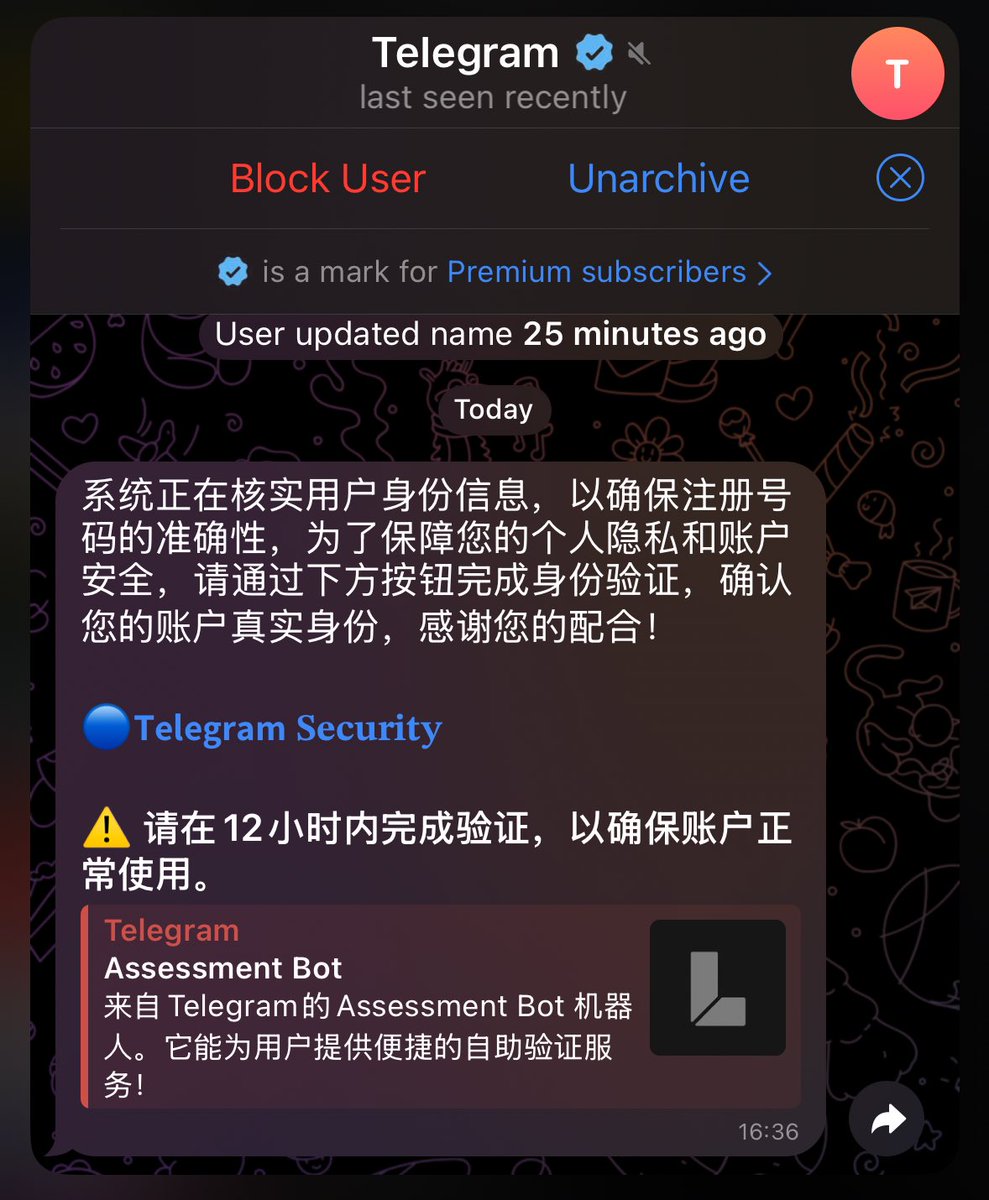
⚠️ 警惕!针对华语社区的新型 Telegram 钓鱼手法,骗子会伪装成 Telegram 安全账户要求点击验证。一旦点击并提供身份验证码后账户将被盗取!导致冒用身份诈骗!泄漏敏感数据!如果使用了 Mini App,资产将会被洗劫一空,身边朋友已有中招!(见图 3 ) 避免方法: 1. 鉴别号码归属地及注册时间 2.…

.@SuperRare was hacked for $710,000. The root cause of this SuperRare staking exploit? A brain-dead permission check that only lets non-owners and non-specific accounts update the Merkle Root. Seriously, who wrote this? Should’ve been a tight require(msg.sender == owner() ||…

> beyond the audit scope > beyond the auditor’s control Rather than blindly shifting blame, it would be better to consider whether you have fulfilled your obligation to urge developers to deploy the correct version. Once you've marked and verified on-chain addresses for other…
The report clearly stated the vulnerability was discovered during the audit. However, the developer later deployed an older version, which was beyond the auditor’s control. Rather than blindly blaming auditors, we should focus on integrating security across more stages of…
.@ZKBaseOfficial’s $5M hack on July 9th is a total joke—hackers exploited a verifyProof function hardcoded to return true, turning Exodus Mode into a hacker ATM! Worse? This flaw was flagged in the audit report and marked “fixed”—yet it stayed broken! Audits aren’t just for…
Excited to back the team from the start. At @SupremacyHQ, we don’t just ensure ideas land safely through high-quality audits—we dive deep with advisory and funding as needed. 🤝
Huge congrats to @sigmadotmoney, our awesome client and friends! You guys are killing it, and we’re stoked to see you shining in the MVB Season 10 cohort. Keep rocking it!
I know some of the issues you highlight in audit report can be valuable, but please, sharpen your writing skills. Your final deliverable isn’t just a list of issues—it’s a professional audit report. Why not aim to be a *wordsmith (language hacker) too? Sloppy grammar and…
what i mean is that an attack transaction fundamentally requires three steps: funding, deploying contracts, and launching the attack. therefore, to execute a hack, the most critical factor is identifying the root cause. this is the first principle and the most accurate way to…
yes flash loan isnt entirely a new technique in itself, other methods also get involved
couldn’t agree more
A flash loan is just a funding mechanism, and we don't have a vulnerability category for "Binance attack". Nor do we call a bank robbery that bought a mask with a credit card a "Visa attack vulnerability".
.@ArcadiaFi is still under attack and just now another $777,940 was hacked. Controllable arbitrary data leads to a CHAIN of ATTACK. basescan.org/tx/0x49548943f…
Supremacy 🤝 Aladdin DAO Big thanks to @SharlynWu and @aladdindao for the high praise of @SupremacyHQ’s audit service! Aladdin DAO is a hub for DEFI DEGENS and the builder of stellar protocols like @protocol_fx. Looking forward to continued collaboration!