Simo
@SimoKohonen
cyber deception founder + researcher @defusedcyber | adversary tools, techniques, procedures
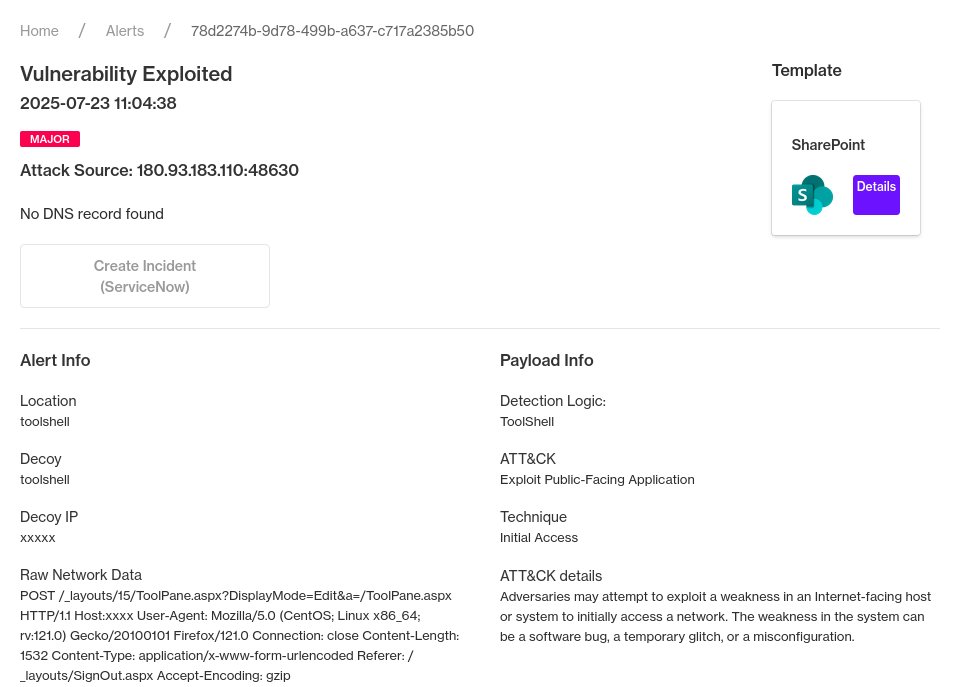
And here we go, first CVE-2025-53770 exploit hitting the honeypots I deployed. I guess there is a public exploit now somewhere? POST /_layouts/15/ToolPane.aspx?DisplayMode=Edit&a=/ToolPane.aspx HTTP/1.1 Host: xxxx User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64;…
Brb deploying 25 sharepoint honeypots / decoys...
CISA flags PaperCut RCE bug as exploited in attacks, patch now - @serghei bleepingcomputer.com/news/security/…
Adding a functionality to the honeypots 🍯 that instafires a NMAP scan back at all connections
Papercut NG honeypot fleets have been registered by @shodanhq AFAIK CVE-2023-2533 does not have a known/public POC yet, let's see if one manifests..
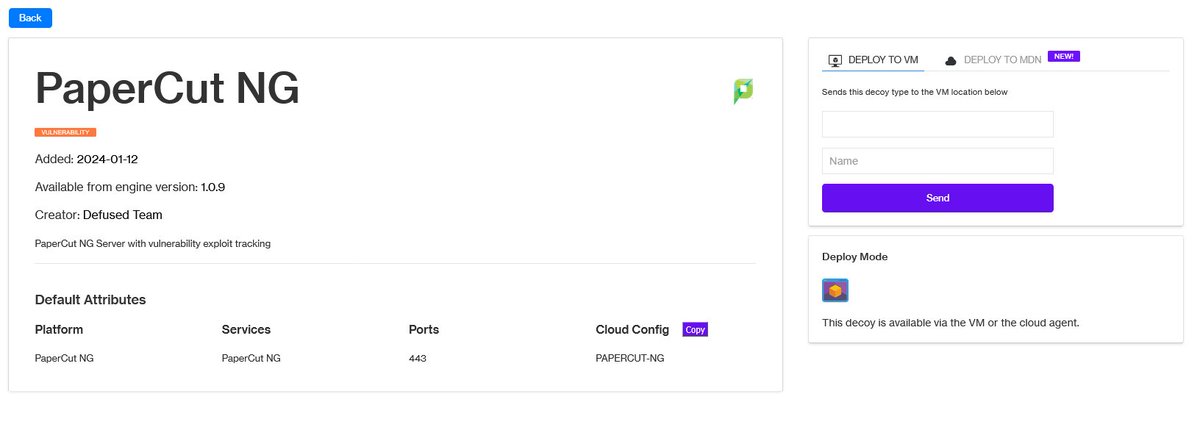
CISA warns of acute exploitation of PaperCut NG - CVE-2023-2533 PaperCut NG/MF Cross-Site Request Forgery (CSRF) Vulnerability We've added a PaperCut NG decoy into the free decoys, go deploy yours now 👉console.defusedcyber.com/signup
CISA warns of acute exploitation of PaperCut NG - CVE-2023-2533 PaperCut NG/MF Cross-Site Request Forgery (CSRF) Vulnerability We've added a PaperCut NG decoy into the free decoys, go deploy yours now 👉console.defusedcyber.com/signup
CISA warns of acute exploitation of PaperCut NG - CVE-2023-2533 PaperCut NG/MF Cross-Site Request Forgery (CSRF) Vulnerability We've added a PaperCut NG decoy into the free decoys, go deploy yours now @DefusedCyber
For non-rogue warmonger states, please leverage our free F5 BIG-IP decoy on @DefusedCyber
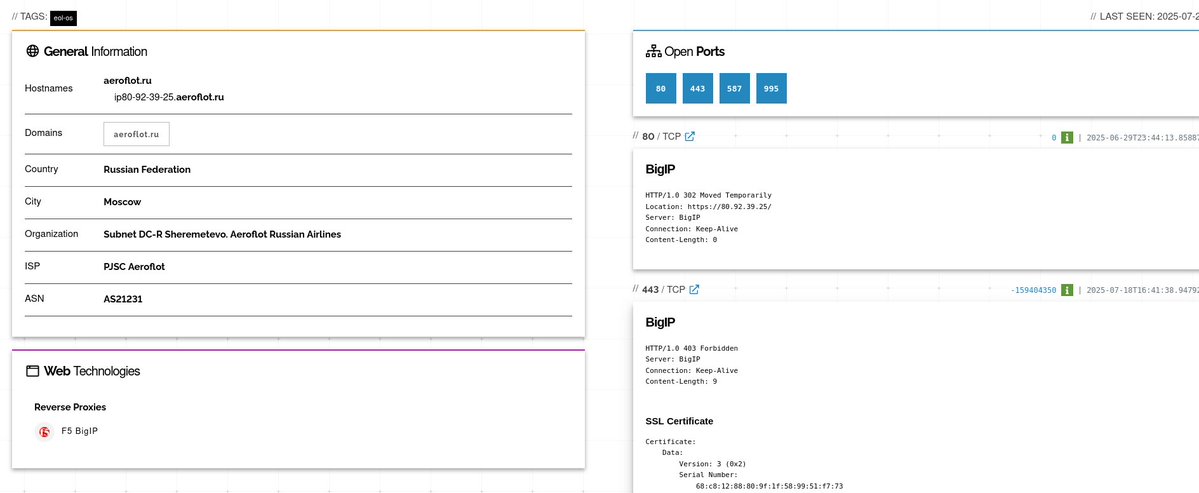
Re: Aeroflot hack - they have at least been running F5 BIG-IP which, being American software, falls under sanctions and consequently may be running a very outdated version. Plenty of critical vulns in BIG-IP in the last 2 year timespan allowing for remote code execution
Re: Aeroflot hack - they have at least been running F5 BIG-IP which, being American software, falls under sanctions and consequently may be running a very outdated version. Plenty of critical vulns in BIG-IP in the last 2 year timespan allowing for remote code execution
Someone should tell the iranians SMB is not on port 443
Bunch of 🇮🇷 IPs sending low‑effort SMB/NetBIOS scan/fuzz traffic to VMWare honeypots.. just putting them here for reference: 5.211.111.97 5.134.133.12 217.218.35.195 46.100.87.55 151.234.200.224
Honeypot server activated: 14:49:08 GMT+3 1 minutes and 37 seconds later: The internet is a pretty hostile place 💀
Bunch of 🇮🇷 IPs sending low‑effort SMB/NetBIOS scan/fuzz traffic to VMWare honeypots.. just putting them here for reference: 5.211.111.97 5.134.133.12 217.218.35.195 46.100.87.55 151.234.200.224
I literally write and make content on the topics I wish I had when I was a newbie in IT & Security. Read time: 4-5 minutes per week I promise I'll do my best every week to deliver value. Click the link to subscribe 👇 click.spenceralessi.com/mylinks p.s. it won't hurt my feelings if…
Detections engineers, threat hunters, you should be putting controls in place for ‘Bring-Your-Own-EDR (BYOEDR)’ style attacks
EDR-on-EDR Violence 1/🧵 @BushidoToken called out that EDR products were being abused by threat actors. @Shammahwoods & I realized a free trial of an attacker controlled EDR can be used to kill the existing EDR. @techspence @UK_Daniel_Card @Jhaddix github.com/CroodSolutions…
Interesting thread by @CroodSolutions on using EDR to kill EDR
🧵2/ We noticed a few problems immediately: - Multiple EDR/AV vendors allow for unverified free trials. - An attacker-controlled (trial) EDR can be used to kill the actual EDR (Cisco Secure Endpoint can kill Elastic Defend and Crowdstrike Falcon Protect). - Sometimes a new…
Go go go 👉console.defusedcyber.com/signup
The Sharepoint vulnerability (CVE-2025-53770) is being associated with a new strand of ransomware, the Warlock ransomware. If you run Sharepoint in any form: 1) Deploy a free Sharepoint decoy on @DefusedCyber 2) Chuck it's IP address into your public DNS under something like…
The Sharepoint vulnerability (CVE-2025-53770) is being associated with a new strand of ransomware, the Warlock ransomware. If you run Sharepoint in any form: 1) Deploy a free Sharepoint decoy on @DefusedCyber 2) Chuck it's IP address into your public DNS under something like…