Darren McDonald
@R3n5k1
Currently into Rust, phishing, redteaming, and hardware.
What a find! My man Blackie found something special. The private key included in the software #paxton #CVE-2023-43870
New Blog Post: Shipping your Private Key - CVE-2023-43870, Paxton do a Lenovo cryptic.red/post/shipping-…
New Blog Post: Shipping your Private Key - CVE-2023-43870, Paxton do a Lenovo cryptic.red/post/shipping-…
If you aren't using a pre-boot PIN with bitlocker, I'm getting in. With @R3n5k1
My first CVE with AmberWolf has recently been resolved by Dell. Memory dumps on ThinOS Wyse terminals are not stored encrypted despite the use of FDE. blog.amberwolf.com/blog/2025/june…
Just released a few new courses - the start of my "Code Review & Architecture Fundamentals" series. 33% off on two of the courses until EOD 2nd Dec. Big thanks to @getCourseStack for their support in making this possible! 👉 ogsec.co.uk/2024/11/13/cod…
We've been looking at FortiWeb Cloud IaaS WAFs. There's a very easy bypass which allows attackers passed all your logging and WAF rules if you've not implemented the origin lock feature. youtu.be/XtAOpiKu3u0?si…
.@buffaloverflow & @johnnyspandex are discussing how to exploit corporate VPN clients for remote root & SYSTEM shells. Join to see live demos on Windows & macOS vulnerabilities & how attackers gain control w/ just one click. Register Free: sans.org/u/1vBt #SANSHackFest
Docker is stupid. “Sorry, we can’t deploy a single statically linked executable of size 10 MB, so LET’S JUST SHIP GIGABYTES OF DATA CONTAINING AN ENTIRE OS WITH ALL DEPENDENCIES FOR EVERY SINGLE SERVICE”
We're excited to announce our first speaker for the October mini meet! @R3n5k1 will be delivering his talk, "Breaking the Shield: Bypassing FortWeb WAFs and Zscaler ZIA"
Myself and @00Waz are releasing the Desktop Decoder today, a useful tool to easily display an encoded hex value of the Wiegand data transmitted over the wire from an Access Control reader. Great for anyone into PACs! github.com/craigsblackie/…
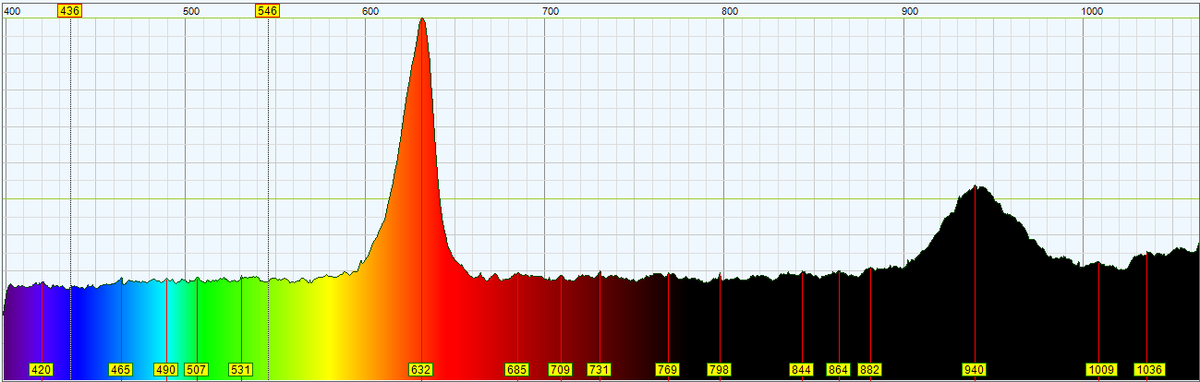
Started taking spectra of IR touch-less exit sensors to make sure I'm getting the best possible range when bypassing them. The assumption is they all work at 940nm, but seems worth checking. NT200 is up first.
Just released my tool LetItRust. Inspired by the tool LetItGo, it uses exchange API to get other domains in the same Microsoft tenant but it uses your Gandi PAT/API key to check if the domain can purchased. Great for cloud reviews, osint, and redteaming. github.com/CR-DMcDonald/l…
@BSidesBSK thanks for a great day @R3n5k1 , @NullMode_ and I had an awesome time!
If anyone else has fallen down the rabbit hole of bypassing IR touch-less exit sensors, I'm starting to document the signal patterns on a github repo. If you've got data for other models or different patterns and timings please consider adding them. github.com/CR-DMcDonald/I…
#emfcamp was great. My plans at listening to all the talks was derailed by meeting and talking with so many awesome people.
13 hours left on the early bird pricing on my report writing course! Grab it now for life time access while it's cheap m8s training.zeropointsecurity.co.uk/courses/the-ar…
After years of making do with a mixture of scapy, wireshark, and the existing rtpnatscan tool I have finally written an RTP Bleed exploit. Before running on your client's SBCs, be warned it can be very disruptive. github.com/CR-DMcDonald/v…
Automating the process of SEOS downgrade attacks.