Octoberfest7
@Octoberfest73
Red Team | Offensive Tool Dev | OSCP | OSEP
Here is a demo of the TGT Auto-Harvester that students will create in my BOF Development and Tradecraft course (training.zeropointsecurity.co.uk/courses/bof-de…). Install in a SYSTEM beacon and passively monitor + capture TGTs from new user logins without calling back to the TS, even while Beacon sleeps!
Disappointing red team affirmations
Disappointing red team affirmations
How in the world is the bot/crypto scam problem so prolific on this site when they lock your account and make you pass a captcha every time you try to message a new person (oh and they delete / lose the message you typed out so you start over when you're done). Trash.
I've been looking at the Sharepoint RCE; does anyone have any good resources/guidance on creating custom .net payloads that can be serialized to work with the exploit? Seen ITW payloads posted here that don't use ysoserial/msf generated payloads (which all spawn cmd, etc)
tfw my tools dont get burned cause i suck at documentation and UI
I didn't want to drop a new *Fix naming variant on you guys, but there you go. All jokes aside, it was a great collab with @Octoberfest73. Awesome person and really helps you push the limits when researching and testing💪
One of the very first tools/projects I released back in early 2022 looked at hosting malware via DNS records and then retrieving+reassembling. I used MX instead of TXT records to sidestep MDE detection. github.com/Octoberfest7/D…
Malware in DNS dti.domaintools.com/malware-in-dns/
What tech is out there for individuals to verify the identity of another party on the phone/video? Context of combatting deepfakes and the crazy things AI can do now. A mutual TOTP kind of thing comes to mind, exchange a QR, establish shared TOTP, verify each others codes
We're excited to announce a major new release of x64dbg! The main new feature is support for bitfields, enums and anonymous types, which allows all types in the Windows SDK to be represented and displayed 🔥
After today’s talk at #TROOPERS25 I’m releasing BitlockMove, a PoC to execute code on remote systems in the context of a loggedon user session 🔥 github.com/rtecCyberSec/B… No need to steal credentials, no impersonation, no injection needed 👌
And it doesn't even execute in one of Chrome's sandboxed processes, you get the medium integrity one. LOL, LMAO even
FileFix - A ClickFix Alternative mrd0x.com/filefix-clickf…
FileFix - A ClickFix Alternative mrd0x.com/filefix-clickf…
FileFix - A ClickFix Alternative mrd0x.com/filefix-clickf…
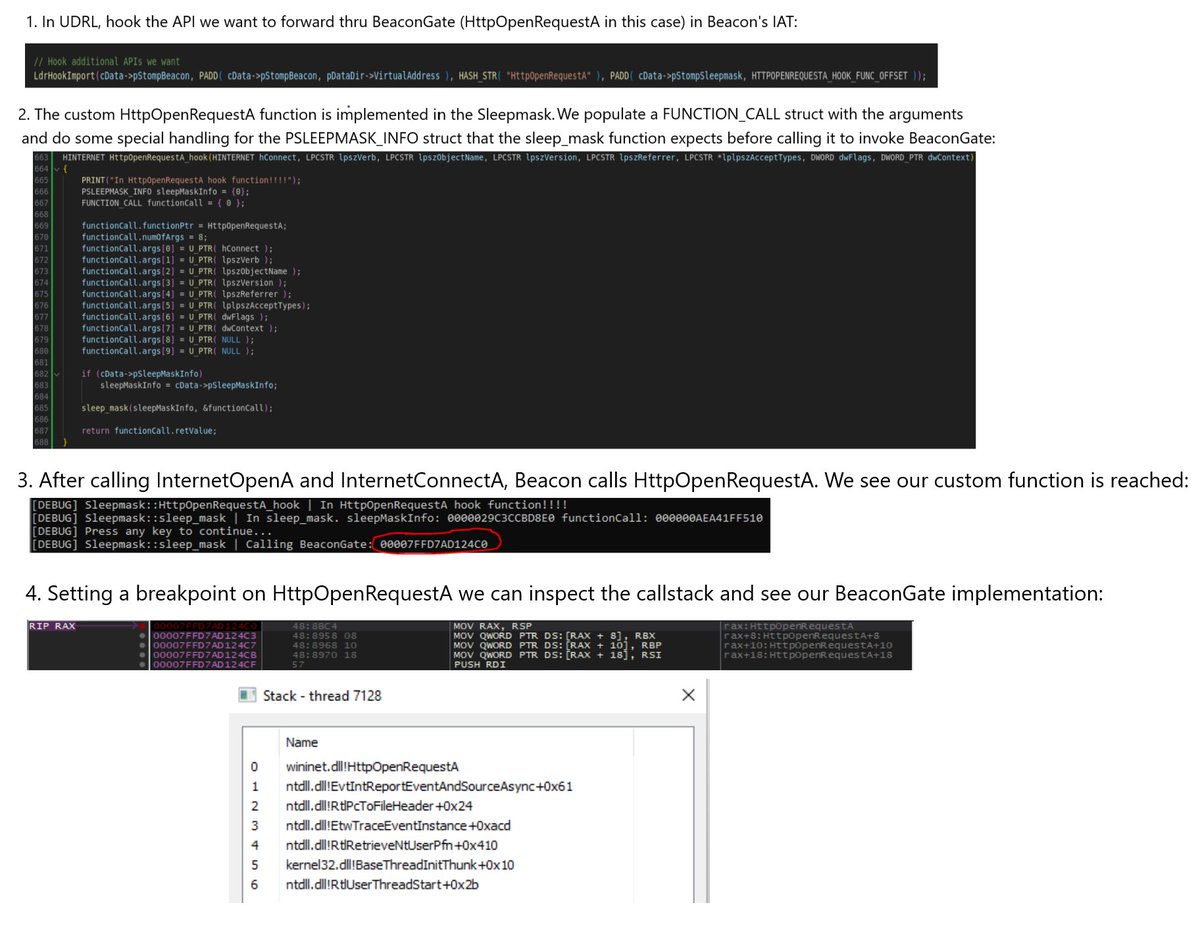
UDRL + Sleepmask is pretty powerful. You can extend Cobalt Strike's BeaconGate functionality to any API you want, no longer limiting you to the officially supported set of API's. Attached example shows proxying HttpOpenRequestA through BeaconGate
I'm happy to announce that my BOF Development and Tradecraft course on Zero Point Security is now part of their Purcharsing Parity Program (PPP). This means you can purchase the course at a potentially reduced price based on the country that you live in! zeropointsecurity.co.uk/course/bof-dev

Some nice work here. Glad to have a working self-deletion technique on latest Windows again.
Windows 11 24H2 broke a popular malware evasion technique! The Lloyd Labs self-deletion method now fails because of NTFS changes, so I spent time with kernel debugging to figure out why and how to fix it. Full technical breakdown: tkyn.dev/2025-6-8-The-N…
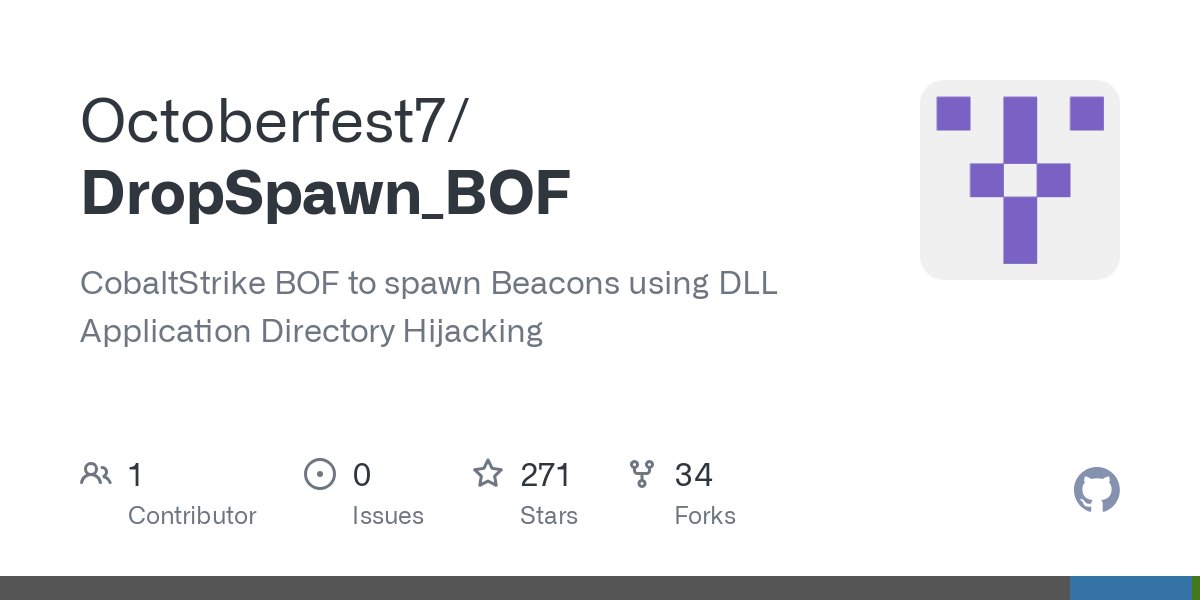
It's 2 years old, but wanted to share this project again as I think it's still relevant. I recently ported DropSpawn to .Net for inclusion in a ClickOnce payload and it's still undetected by MDE. Neat trick to start a process and force it to load a DLL. github.com/Octoberfest7/D…
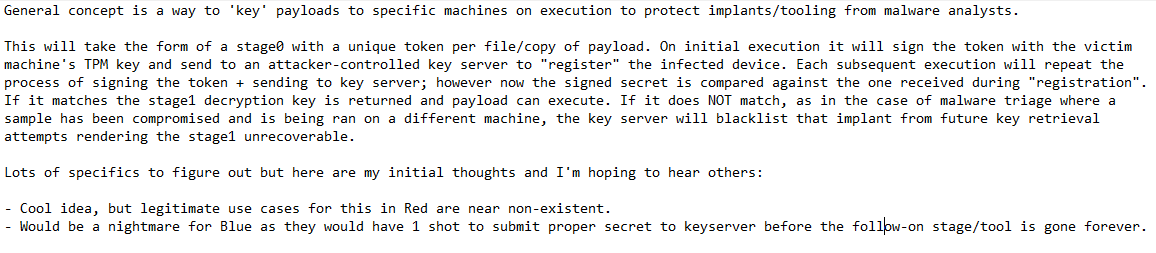
Want to get both Red and Blue's thoughts on a tool concept. Please see screenshot as it's too long to fit in a post.
BadSuccessor (@YuG0rd), o3 finds SMB 0day (@seanhn), crashing defender (@InfoGuard_Labs), MDT looting (@Oddvarmoe), and more! blog.badsectorlabs.com/last-week-in-s…
