
NullSecX
@NullSecurityX
See New Threats Before They Strike https://buymeacoffee.com/nullsecx
🛡️ Since June 1st, we've been one of the most active and impactful voices in Cyber Security & Bug Bounty — maybe even the most. If you’ve learned something from us or just support the mission a retweet and follow goes a long way!💙 Youtube: youtube.com/@nullsecurityx #BugBounty
WhatsApp Chat Manipulation via SQLite Exploit A creative method to forge fake WhatsApp messages by modifying the msgstore.db database. 🙏 Huge thanks to @0x6rss for sharing this technique. 🎥 Demo live: youtu.be/yZy_80f9nO4 #infosec #sqlite #whatsapp #exploit #osint
DarkForums has been hacked by NullSecurityX :) Jokes aside, we showcased the vulnerability found on Darkforums in the video. Happy hacking, everyone! 😊 @DarkWebInformer #BugBounty #CyberSecurity #darkforum
🚨🚨🚨 Warning: DarkForums has an active XSS vulnerability. Do NOT use the website, it's unsafe and will leak your IP!
A critical Next.js Middleware Bypass (CVE-2025-29927) allows attackers to slip past route protections. 🔍 How it works 🧠 Why it matters 🛠️ How to fix it 🎥 Watch the full breakdown now: youtu.be/S3CVytIv098 #NextJS #BugBounty #WebSecurity #CyberSecurity
So… you want to get into CyberSecurity, but don’t know where to begin? I joined forces with @theXSSrat to break it down for you — no fluff, just real talk. ➡️ “How to Get Started in CyberSecurity” is live now! 📺 youtu.be/_C_VNc5of9w #CyberSecurity #Hacking #TheXSSRat
🎯 Quick Poll! Would you be interested in a voice-over training series on Reverse Engineering & Ghidra? 👇 Pick your answer: #bugbounty #ghidra #reverseengineering #re
Just dropped my full walkthrough of the Royal Router room on TryHackMe! 🚀 Step-by-step IoT hacking guide covering reconnaissance, exploits, and flag capture.🔍 Watch now and hack smart! youtu.be/LYQ5EDgqXCM #TryHackMe #IoTHacking #Cybersecurity
Holy cheeseballs!! If I just give away 1 bundle, I am going to have to dissapoint so many people!! I AM ADDING 2 ENDLESS BUNDLES TO THE GIVEAWAY!! 🥳🥳🥳🥳🥳 You have one more day to sign up and i know you want to ... we got knowledge, community, giveaways, lives and so much…
🚨 **CYBERSECURITY GIVEAWAY TIME** 🚨 Win **LIFETIME ACCESS** to the *Endless Bundle* 💥 All my current + future hacking courses 💥 XSS, IDOR, Burp Suite, BAC & more 💥 260+ lessons, private Discord, realistic labs 💥 Exclusive access to giveaways of merch, vouchers, and…
🚨 New Video Alert! 🛠️ How we broke into a server using just XML — deep dive into XXE attacks! Step-by-step walkthrough on file disclosure, SSRF, and even remote code execution. ▶️ youtu.be/jdwZ09E-lsY #XXE #CyberSecurity #BugBounty
Part 3/4 of my series on #BugBounty methodology is out ❤️❤️❤️ BBGMA - Full Bug Bounty Guide - RatMania Webshop labs youtube.com/playlist?list=… via @YouTube
Bug Bounty Tip: HTTP Parameter Pollution (HPP) Some apps mishandle duplicate parameters. You can bypass logic or elevate privileges by injecting multiple values: GET /transfer?amount=100&admin=true&amount=1 ⚠️ Always test: •param=value1¶m=value2 •Encoded (%26,) #BugBounty
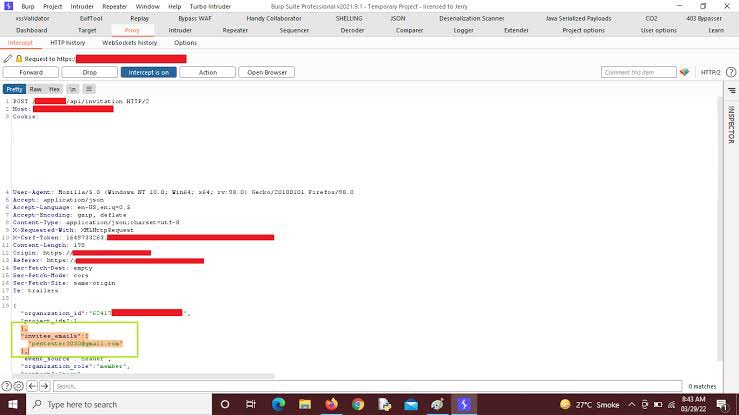
CSRF where token validation depends on request method #BugBounty #CSRF #bugbountytips
Stored XSS Through Malicious File Uploads Explained! #bugbounty #bugbountytips #xss
Go go go @theXSSrat 🧠🔥
Premiering now A reading by @coffinxp7 ❤️ someone who I admire This Is Why You Should NEVER Ignore IDOR! - LostSec youtu.be/lCWgdm3H-OI
How to test for reflected XSS in an HTML context with no encoding👇 #BugBounty #bugbountytips
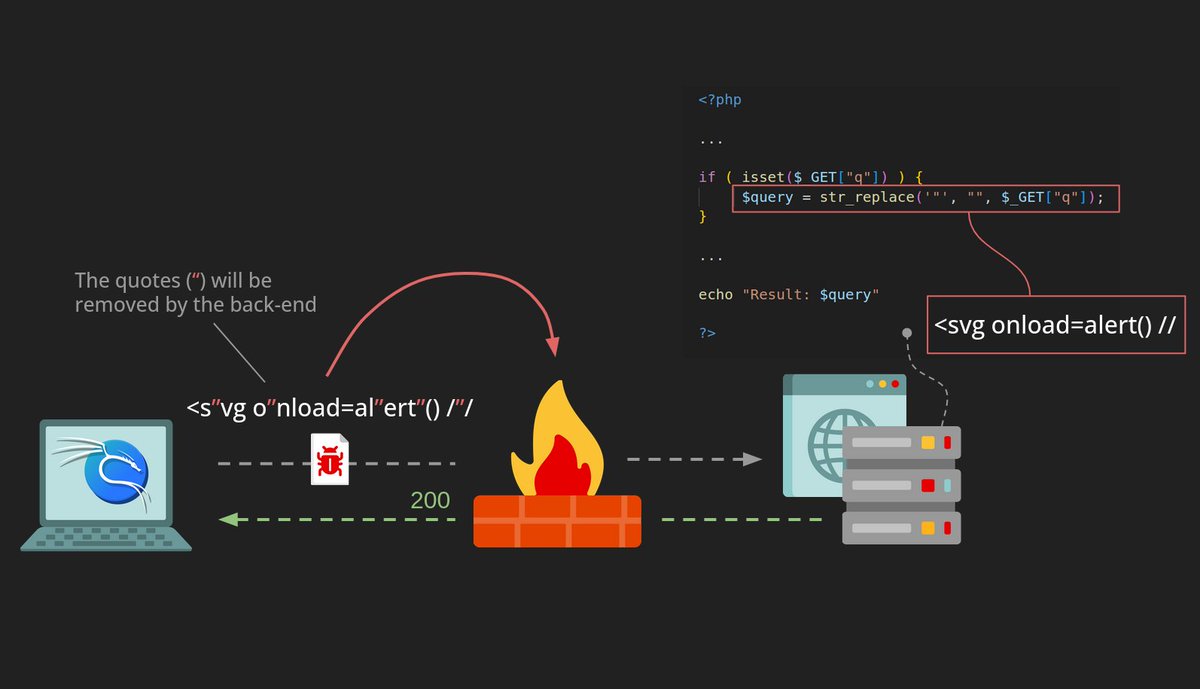
'"--><svg/onload=top[30]()>${{4*9}}<script>+alert?.``</script> •top[30]() → Triggers XSS without using the word alert •alert?.\`` → Optional chaining + template literal stealthy JS excution •--><svg> → Breaks out of HTML comments •${{4*9}} → SSTI,CSTI #BugBounty
Use this polyglot everywhere in #BugBounty and go broad, not deep <3 '"`><img src=x>${{2*8}} SQLi, broken img , JS context for XSS, html tag attribute, SSTI, CSTI
How to Find Path Delimiter Issues with Burp Suite Intruder: #BugBounty #burpsuite #bugbountytips
Successfully chained a SQLi vulnerability into full admin access by exploiting a BAC flaw on a vulnerable bank app by @commando_skiipz 💥 Watch the full PoC demo👇 🔗 youtu.be/ZsWR5nqxdzI #cybersecurity #sqli #bugbounty #infosec #ethicalhacking #websecurity #exploit #ctf