Haifei Li
@HaifeiLi
For contact in the security community. NOTE: All the tweets are totally my personal opinions, not about any of my current employer stuff.
🔥🔥Announcement: Opening EXPMON for Everyone. justhaifei1.blogspot.com/2024/04/openin… EXPMON is a sophisticated exploit detection (and analytics) system specifically designed and built for detecting zero-day/unknown file-based exploits. pub.expmon.com
Three monks were watching a flag flapping in the wind. One said, “the flag moves.” The second said, “the wind moves.” And the third said, “it is a complex bug.” And they were enlightened.
I’m a bit confused when reading this story bleepingcomputer.com/news/microsoft…, was the variant 0day bug discovered and shared accidentally by CODEWHITE researchers (threat actors saw that and exploited itw), or threat actors independently discovered it? Who was the original discoverer?
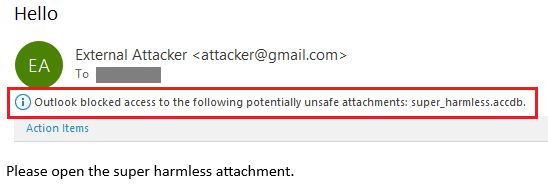
Credit where credit is due. The Microsoft Office team doesn't often highlight their efforts to improve Office user security, so I'm going to share what I just observed while analyzing a very interesting Outlook 0day bug I recently discovered. :) It turns out that Outlook has…
Google Search continues to beat as more ppl ask AI for questions. 🤔
$GOOGL *ALPHABET SEES FY CAPEX ABOUT $85B, SAW ABOUT $75B, EST. $73.31B *ALPHABET 2Q GOOGLE SEARCH & OTHER REV. $54.19B, EST. $52.86B *ALPHABET 2Q GOOGLE CLOUD REV. $13.62B, EST. $13.14B *ALPHABET: CONTINUE TO SEE STRONG PERFORMANCE IN YOUTUBE (Bloomberg)
We are very happy to announce the nominees for the 2025 Pwnie Awards! As a reminder, we will be presenting the winners at DEF CON this year. Saturday the 9th, 10:00AM Main Stage. Hope to see you there! docs.google.com/document/d/1fy…
I have done tons of tests locally for my Office bug and all reproduced (different software, different hardware), but when I used the MSRC-shared VM, I’m so far not able to reproduce once. Yes vulnerability is a tough work sometimes.
I JUST WANT TO POP CALC.EXE FOR A VIDEO WHY IS THIS SO HARD.
Interesting, the P2O bugs were exploited earlier than the patches (July 8).. does it mean the P2O bugs were leaked or something else?
MSTIC blog on Sharepoint exploitation At least 3 actors exploiting CVE-2025-49706 & CVE-2025-49704 as early as July 7: Linen Typhoon Violet Typhoon Storm-2603 (CN-based actor deployed Warlock & Lockbit ransomware in past - current motivation unknown) microsoft.com/en-us/security…
When you read stock news and still get in cybersecurity.
$PANW RUMORED TO BE ACQUIRING $S
This patch release was quick.
Microsoft has released security updates that fully protect customers using SharePoint Subscription Edition and SharePoint 2019 against the risks posed by CVE-2025-53770, and CVE-2025-53771. These vulnerabilities apply to on-premises SharePoint Servers only. Customers should apply…
One thing I wanted to point out - in case of misunderstandings - is that I was not blaming the MSRC bounty program on this specific 0day breaking out. Certainly there’re places that they can improve in their bounty programs (such as my recent “complex bug!= low quality”), but the…
I was reading the SharePoint zero-day news (I have a personal interest in itw 0day hunting), then I realized MSRC has bounties for SharePoint bugs, then I read the program & found it only offers like 20k for critical SharePoint RCE (if I read the rules correctly)…
It's always interesting for me, but it's also very important for the infosec community to review vendor's bounty program when an itw 0day attack broke out. For example, the "secure" vpn appliance vendors don't even have bounty at all, who can blame the 0days then?…
Any SharePoint researcher care to explain why "SharePoint Online in Microsoft 365 is not impacted"? Did the cloud version kill the attack vector/path or the codebase doesn't contain the bug at all? x.com/HaifeiLi/statu…
Whoa! Turns out a new Microsoft SharePoint zero-day attack is being actively exploited in the wild! It's a new variant of a previously-patched SharePoint bug. Of course it always happens on weekends. x.com/msftsecrespons…
Whoa! Turns out a new Microsoft SharePoint zero-day attack is being actively exploited in the wild! It's a new variant of a previously-patched SharePoint bug. Of course it always happens on weekends. x.com/msftsecrespons…
Microsoft is aware of active attacks targeting on-premises SharePoint Server customers, exploiting a variant of CVE-2025-49706. This vulnerability has been assigned CVE-2025-53770. We have outlined mitigations and detections in our blog. Our team is working urgently to release…
