Enno Rey
@Enno_Insinuator
Old-school network security person. Founded http://ernw.de & @WEareTROOPERS. IPv6 blog: http://theinternetprotocolblog.wordpress.com
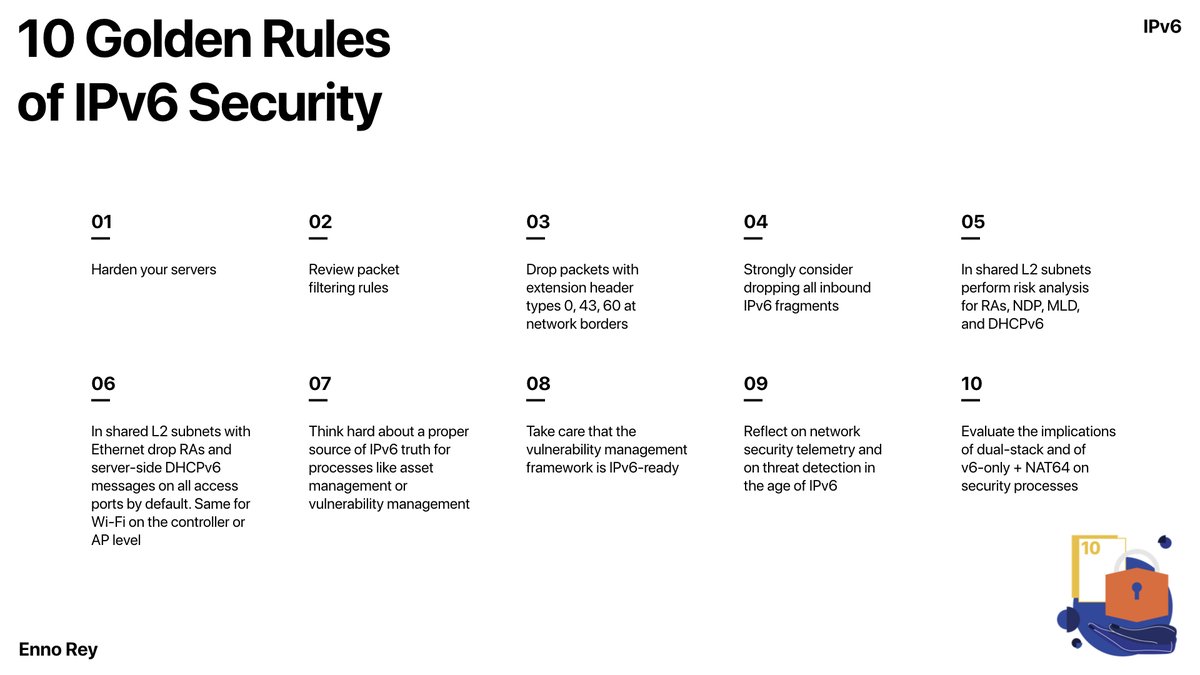
IPv6 Security Best Practices theinternetprotocolblog.wordpress.com/2020/11/28/ipv…
We’re getting ready for the 4th edition of BSides Tirana and we’re looking for support. If your company believes in supporting local talent, knowledge sharing, and cybersecurity, let’s talk. 📩 [email protected] #BSidesTirana #CyberSecurity #Infosec #SponsorCall
Introducing the new HackRF Pro from Great Scott Gadgets! This @GSGlabs product is available immediately for pre-order with an estimated ship date of Sept. 2025: nooelec.com/store/hackrf-p…. The MSRP is $400 Product details available at the link above, with more to follow soon😀…
Entra ID First Party Apps & Scope Browser, by @fabian_bader & @_dirkjan entrascopes.com
Windows Registry Forensics 2025 #DFIR cybertriage.com/blog/windows-r…
Windows Inter Process Communication – A Deep Dive Beyond the Surface, by @haider_kabibo Part 1 sud0ru.ghost.io/windows-inter-… Part 2 sud0ru.ghost.io/windows-inter-… Part 3 sud0ru.ghost.io/windows-inter-… Part 4 sud0ru.ghost.io/windows-inter-… Part 5 sud0ru.ghost.io/windows-inter-…
The Blog post about "Revisiting Cross Session Activation attacks" is now also public. Lateral Movement with code execution in the context of an active session? 😎 Here you go: r-tec.net/r-tec-blog-rev…
ernw.de research (II) Input Validation Vulnerabilities in Microsoft Bookings insinuator.net/2025/05/disclo… When Your Edge Browser Syncs Private Data to Your Employer insinuator.net/2025/02/when-y… Jigsaw RDPuzzle: Piecing Attacker Actions Together insinuator.net/2025/01/jigsaw…
Recent research/education contributions by ernw.de pros (I) Windows Hello for Business – The Face Swap insinuator.net/2025/07/window… Windows Hello for Business – Past and Present Attacks insinuator.net/2025/06/window… Microsoft Entra Dangerous Defaults shop.heise.de/microsoft-entr…
Thanks to everyone who came to my @WEareTROOPERS #TROOPERS25 talk today! The slides are available here - github.com/h4wkst3r/Confe…
New research just dropped I'll be presenting at @WEareTROOPERS next week - Attacking ML Training Infrastructure 💥 Model poisoning for code execution ⚠️ Abusing ML workflows ⚙️ MLOKit updates and new threat hunting rules ibm.com/think/x-force/…
It's also a pretty cool domain name 😀 leastprivilege.com cc: @leastprivilege
I publish two blog posts today! 📝🐫 The first dives into how we're improving the way BloodHound models attack paths through AD trusts: specterops.io/blog/2025/06/2… The second covers an attack technique I came across while exploring AD trust abuse: specterops.io/blog/2025/06/2…
At @WEareTROOPERS I dropped new research on #nOAuth, an abuse of #EntraID that allows you to spoof users in vulnerable SaaS applications. The attack is still alive and well. You can read all about it here: #Entra #M365 #infosec semperis.com/blog/noauth-ab…
The slides from #TROOPERS25 are now available🔥 The key point in the talk is that Device Registration Service is often forgotten in Conditional Access, leading to various abuse. This talk introduces one of the examples and explains lateral movement tips. troopers.de/downloads/troo…
It was great to attend #TROOPERS25! Beautiful city, nice weather, talented researchers. My talk was just based on how Entra works but I hope it contributed to the community. Thanks for everyone I had a chance to talk to! No jet lug now. Time to go home😂 github.com/temp43487580/E…
Windows Hello for Business – The Face Swap, on @Insinuator insinuator.net/2025/07/window…
Insecure Boot: Injecting initramfs from a debug shell, via @Insinuator insinuator.net/2025/07/insecu…