Sam Bent
@DoingFedTime
Journalist | OSINT & OPSEC Specialist | Darknet Expert (Ex Vendor & DNM Admin) | DEFCON/SANS Speaker | Youtuber | Social Engineer | Author | Paralegal
87E1LCiePLNJyufiUW48bNAH7bobcSXU8TSxLXWjkuXbfSDVq3oZgze9nvotdv8Fp55Ud5itCuUEmXbEbdanTRfECx9Ubh8
Two-factor authentication via SMS can be intercepted through SIM swapping attacks. Use TOTP apps or hardware keys instead of text messages.

Your phone's accelerometer data reveals what you're typing through vibration patterns. Apps can read keystrokes without accessing your keyboard.

You can write "Password: abcdef123" on the phone case to avoid needing to actually provide it to them. This way you aren't actually providing the duress PIN/password to anyone in particular. It's their own fault for reading it off the phone case and entering it.
Even the local PDs are now protecting the child rapists. @VBPD It would be great to see these cops who let a dude who raped a 6 year old go to prison as co-conspirators.
HOLY SHIT! Virginia Beach Police LIED about arresting chi*d p*rn producer Mijeul Butler. We were told he was arrested and is being held on no bond. In reality, he was never even booked. This is the most egregious dereliction of duty ive EVER seen. Make your voice peacefully…
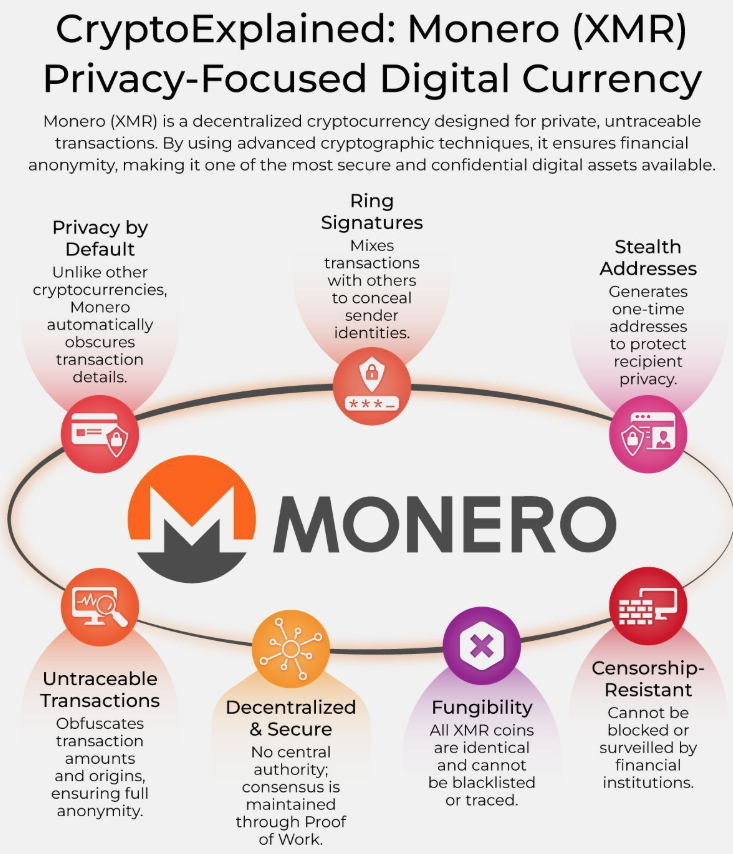
Monero's stealth addresses generate unique payment addresses for each transaction. Bitcoin address reuse links all your payments together forever.
Which surveillance tool has the highest adoption rate? Social media platforms that convinced users to voluntarily report their every thought and location.
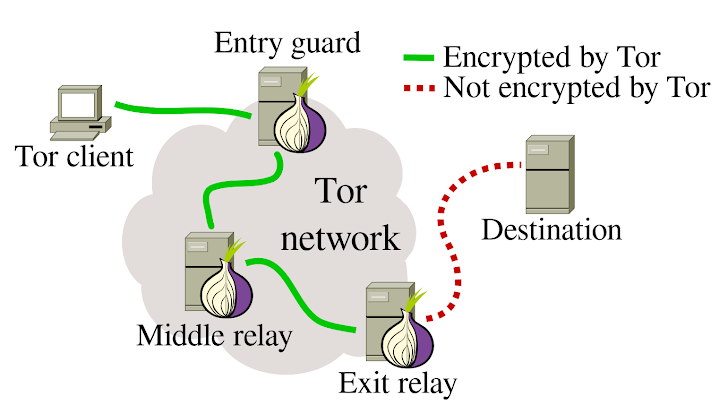
Tor exit nodes can see unencrypted traffic but not its source. HTTPS protects content while Tor protects identity, use both together.
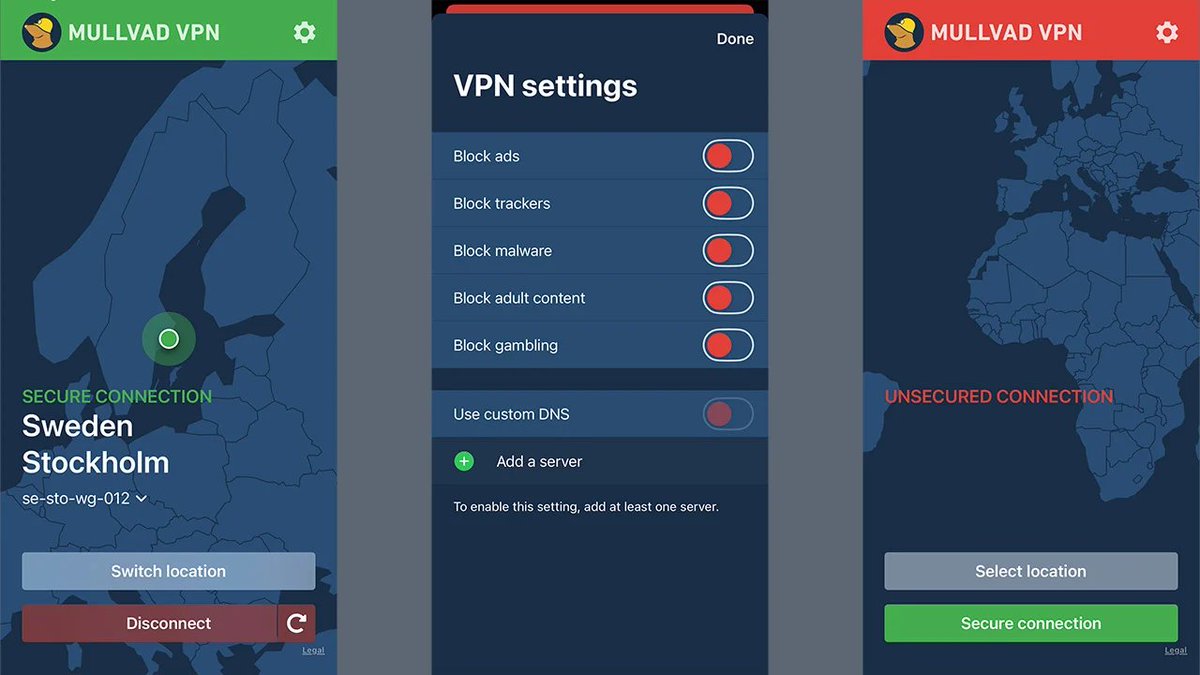
Mullvad VPN accepts cash payments and doesn't require email addresses. Most VPN companies want your payment details to build customer profiles.
Developers Are Already Terrified Developers now need lawyers before pushing code to GitHub. This is what criminalizing software looks like. youtu.be/WN5uOMTGzPc #OpenSource #CryptoPrivacy #RomanStorm
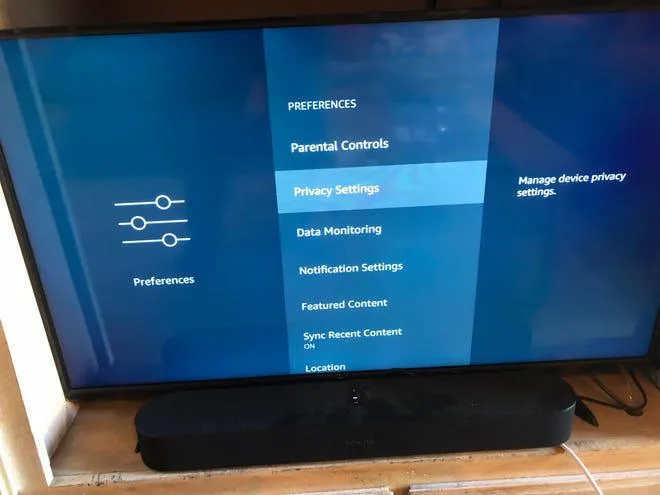
Your smart TV records conversations and sends them to manufacturers. Roku, Samsung, and LG privacy policies admit to 'improving voice recognition.'
Border agents copy entire phone contents in seconds using Cellebrite devices. Full disk encryption only protects powered-off devices.

That annoying GPU coil whine? It's broadcasting your computational secrets. Researchers can determine specific calculations, rendered content, even cryptographic operations—all from the high-pitched sounds your graphics card makes. Shocking details: youtu.be/kDMfDN7iuQY
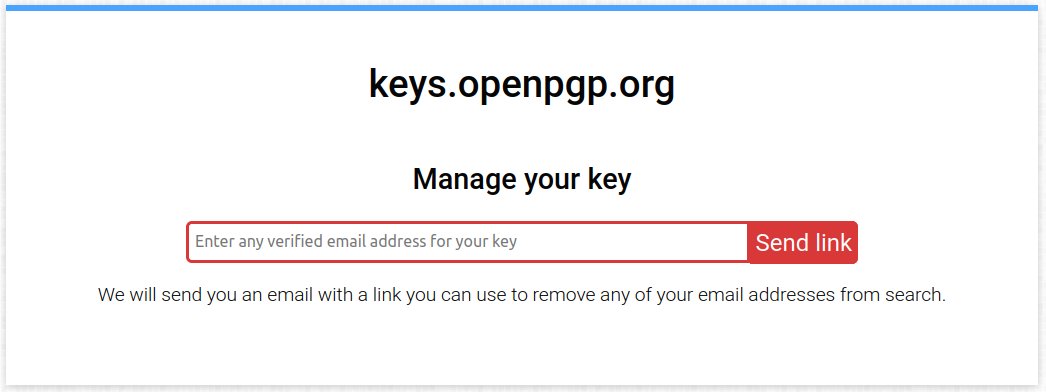
OpenPGP keyservers store public keys forever and can't delete them. Once your email is associated with a key, it's permanent internet history.
Banks vs Developers HSBC laundered $881 million for cartels and paid a fine. This developer faces 45 years for writing privacy code. youtu.be/WN5uOMTGzPc #TornadoCash #FinancialPrivacy #CryptoTrial
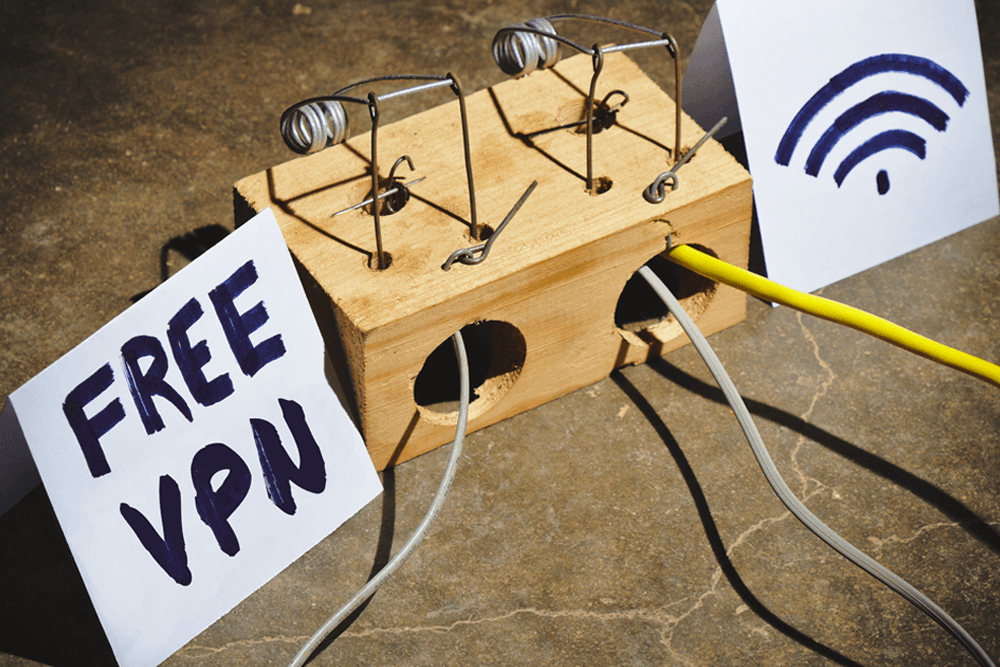
Why do free VPNs exist when servers cost money? Because they sell your browsing data to the same advertisers you're trying to avoid.
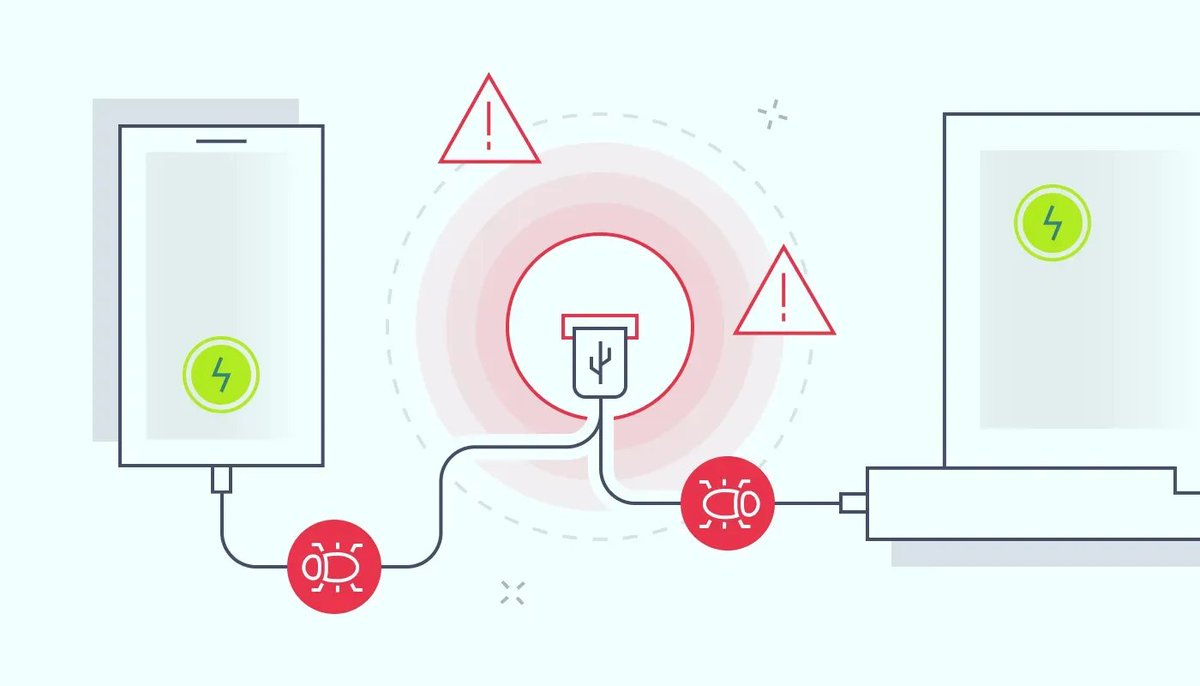
USB data blockers prevent public charging stations from accessing your phone's files. 'Juice jacking' attacks install malware through charging cables.
Element Matrix client offers encrypted group chats without phone numbers. Unlike Discord or Telegram, you control your own server and data.