
ClearSky Cyber Security
@ClearskySec
Cyber security and threat intelligence company
Recently we identified a notable uptick in TA455 related activity tied to the ongoing Iranian "Dream Job" campaign. Tactics, techniques, and procedures (TTP’s) of the group seem to be evolving continuously, demonstrating a high level of agility. We discovered new unknown malware…

We have identified a widespread campaign in Ukraine that distributes malicious PDF files. Documents claiming to be from tax[.]gov[.]ua are disguised as official messages. When the recipient clicks the download link within these PDFs, a JavaScript file with a double extension…
![ClearskySec's tweet image. We have identified a widespread campaign in Ukraine that distributes malicious PDF files.
Documents claiming to be from tax[.]gov[.]ua are disguised as official messages.
When the recipient clicks the download link within these PDFs, a JavaScript file with a double extension…](https://pbs.twimg.com/media/Gr3FjlzWcAA5w3g.jpg)
A suspected new malware variant linked to the MuddyWater Iranian APT group has been discovered. Based on the PDB path, we named it Phoniex. Phoniex was used in attacks impersonating the Hungary government and Netivtech, an Israeli company IoCs: Sha256:…

ClearSky discovered in early April a Yemeni/Houthi influence campaign operating in Israel, Saudi Arabia, and the UAE. In 2019, we first exposed the campaign. It continues to operate in a similar manner to what we uncovered in 2019. Between 2019 and 2022, the campaign focused…

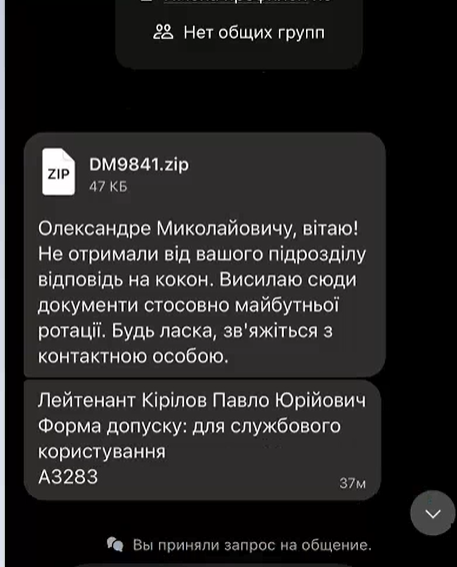
ClearSky Cyber Security has been tracking a campaign active since December 2024, potentially targeting Ukrainian soldiers. The attack begins with an SMS or Whatsapp message containing a ZIP file that includes malicious LNK shortcuts. These LNK files act as droppers, downloading…
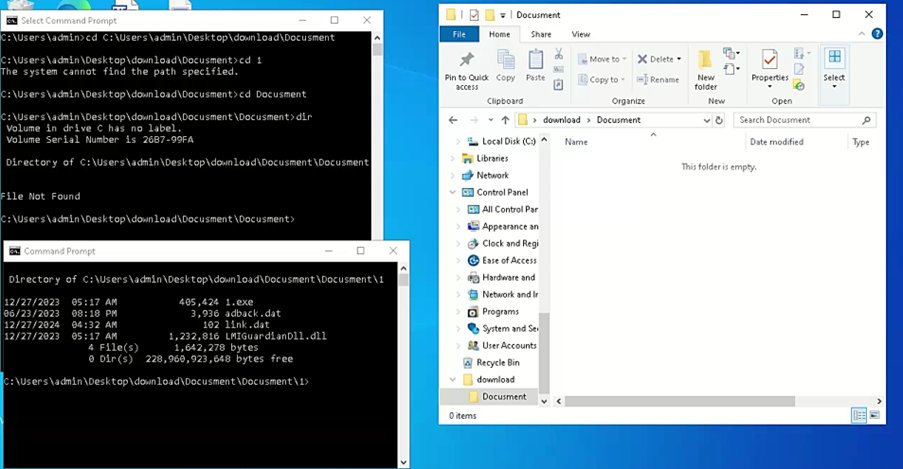
ClearSky Cyber Security has discovered a UI vulnerability in Microsoft Windows. This vulnerability is actively exploited by a suspected Chinese APT group - Mustang Panda. When files are extracted from compressed “RAR” files they are hidden from the user. If the compressed files…
A new infrastructure for the Russian information warfare campaign named Doppelgänger has been discovered by ClearSky. “Doppelgänger” (meaning an exact but usually invisible replica) is a global information warfare campaign publishing false information on fake websites and social…
A new zero-day vulnerability, CVE-2024-43451, was discovered by ClearSky. This vulnerability affects Windows systems and was actively exploited in attacks against Ukrainian entities. The malicious URL files were disguised as academic certificates and were initially observed…

ClearSky Cyber Security research identified a campaign named “Iranian Dream Job”, in which the Iranian threat actor TA455 targeted the defense sector by offering fake jobs. The campaign distributed the SnailResin malware, which activates the SlugResin backdoor. ClearSky…

The Iranian APT group MuddyWater is attacking Saudi Arabian organizations using PDQ Connect RMM software and internxt[.]com storage services ITW: hxxps[://]share[.]eu[.]internxt[.]com/d/sh/file/763a0e5…
![ClearskySec's tweet image. The Iranian APT group MuddyWater is attacking Saudi Arabian organizations using PDQ Connect RMM software and internxt[.]com storage services
ITW: hxxps[://]share[.]eu[.]internxt[.]com/d/sh/file/763a0e5…](https://pbs.twimg.com/media/GXHsUfkWMAECu-r.jpg)
Using a new RMM tool "PDQ Connect" MuddyWater impersonated to: MKK from Turkey, a Jordanian company "Offtec" and IDF: offtecportal[.]egnyte[.]com 750308da76cbff35ee548f23439bc0d8 6780e3b13029ac58c96e3e59c0535d42 2690694b348358c9d1261db2e64ae5ef 29aa13acd46472b62cc0fbaa4c94062e
![ClearskySec's tweet image. Using a new RMM tool "PDQ Connect" MuddyWater impersonated to: MKK from Turkey, a Jordanian company "Offtec" and IDF:
offtecportal[.]egnyte[.]com
750308da76cbff35ee548f23439bc0d8
6780e3b13029ac58c96e3e59c0535d42
2690694b348358c9d1261db2e64ae5ef
29aa13acd46472b62cc0fbaa4c94062e](https://pbs.twimg.com/media/GUN9kpzWcAACg-7.jpg)
Checkpoint published a report matching our findings of a new backdoor deployed in recent MuddyWater campaigns. Thanks for your credit @CheckPointSW research.checkpoint.com/2024/new-bugsl…

The Iranian APT group MuddyWater is targeting Azerbaijan with a new loader, named by us as "BackConnect" downloadfile[.]egnyte[.]com fileuploadcloud[.]egnyte[.]com 85[.]239.61.97 dda1c7d21118ccb6e7fb4b7a02e53db3 e7df84a5a22aeafcf1c3abf4fd986c91 dac03401c2cc284148a60bc88fbdf8bd
![ClearskySec's tweet image. The Iranian APT group MuddyWater is targeting Azerbaijan with a new loader, named by us as "BackConnect"
downloadfile[.]egnyte[.]com
fileuploadcloud[.]egnyte[.]com
85[.]239.61.97
dda1c7d21118ccb6e7fb4b7a02e53db3
e7df84a5a22aeafcf1c3abf4fd986c91
dac03401c2cc284148a60bc88fbdf8bd](https://pbs.twimg.com/media/GSNWqL9XsAAzIEp.jpg)
Iranian APT group MuddyWater impersonated Airpaz to target more Egyptian companies Egnyte url: airpaz[.]Egnyte[.]com Egnyte User: manara[.]edu[.]sy 15941e167f258c0d78d01aa6fa2fea19 9c63b57d1250cd89fbd82ae2b4062aa3 d1e400e1e8100872d1f0f6a4f99eb51d a46206daae98334e47e178bc718d9baf
![ClearskySec's tweet image. Iranian APT group MuddyWater impersonated Airpaz to target more Egyptian companies
Egnyte url: airpaz[.]Egnyte[.]com
Egnyte User: manara[.]edu[.]sy
15941e167f258c0d78d01aa6fa2fea19
9c63b57d1250cd89fbd82ae2b4062aa3
d1e400e1e8100872d1f0f6a4f99eb51d
a46206daae98334e47e178bc718d9baf](https://pbs.twimg.com/media/GReErfPX0AA0s1-.png)
Using an impersonation of Cairo International Airport, the Iranian MuddyWater APT group targeted a Jordanian company Egnyte url: Cairoairport[.]Egnyte[.]com MD5: b77259eb3279ef1f5eb7cfae7d818ff1 0993e8ffdc69c202e56b8070a0ceb8cd
![ClearskySec's tweet image. Using an impersonation of Cairo International Airport, the Iranian MuddyWater APT group targeted a Jordanian company
Egnyte url:
Cairoairport[.]Egnyte[.]com
MD5:
b77259eb3279ef1f5eb7cfae7d818ff1
0993e8ffdc69c202e56b8070a0ceb8cd](https://pbs.twimg.com/media/GQw_wydWwAAvz14.jpg)
We have identified a change in the primary domain used in the Doppelganger campaign, Russian Cyberwarfare campaign. As of May 2024, it appears that the main root domain is cheekss[.]click instead of sdgqaef[.]site
![ClearskySec's tweet image. We have identified a change in the primary domain used in the Doppelganger campaign, Russian Cyberwarfare campaign. As of May 2024, it appears that the main root domain is cheekss[.]click instead of sdgqaef[.]site](https://pbs.twimg.com/media/GQhSmK9W8AAbG3s.png)
The Iranian MuddyWater APT group targeted Nour Communications from Saudi Arabia Egnyte url: nour[.]egnyte[.]com MD5: 5af57c7c7721519c0dc613a837f436c5
![ClearskySec's tweet image. The Iranian MuddyWater APT group targeted Nour Communications from Saudi Arabia
Egnyte url:
nour[.]egnyte[.]com
MD5:
5af57c7c7721519c0dc613a837f436c5](https://pbs.twimg.com/media/GP8hr1dW4AAx2ky.jpg)
Iran's MuddyWater APT group is suspected of targeting Turkey, Azerbaijan, Jordan, Saudi Arabia, and Israel. Egnyte urls: alkan[.]egnyte[.]com cnsmportal[.]egnyte[.]com c2: 91[.]235[.]234[.]202 146[.]19[.]143[.]14 md5: aded87fc07645e8fcecf622b3b1171d2…
![ClearskySec's tweet image. Iran's MuddyWater APT group is suspected of targeting Turkey, Azerbaijan, Jordan, Saudi Arabia, and Israel.
Egnyte urls:
alkan[.]egnyte[.]com
cnsmportal[.]egnyte[.]com
c2:
91[.]235[.]234[.]202
146[.]19[.]143[.]14
md5:
aded87fc07645e8fcecf622b3b1171d2…](https://pbs.twimg.com/media/GPpHjKjXAAAAa1C.png)
ClearSky and SentinelLabs have discovered a new wave of Doppelgänger campaign. The "Doppelgänger NG" campaign (meaning “spirit double”) spreads false information. We found a link between the "Doppelgänger NG" Campaign and the Russian group APT28. clearskysec.com/dg…

The latest Iranian attack against Albanian organizations is presented in a new blog post on our website titled "No-Justice" Wiper clearskysec.com/no-justice-wip…
