
BlackWasp
@BlWasp_
Pentester and Red Team technical leader at Advens | Microsoft MVP
I'v recently updated my Active Directory cheatsheets. I'v added attacks regarding krbjack, GPOditty, SCCM, RODC pivoting, External Trust non-transitivity bypass, DES attacks, and others. If interested : - AD : hideandsec.sh/books/cheatshe… - AD Python : hideandsec.sh/books/cheatshe…
Following the release of IPSpinner last week, now is the time to unveil CaptainCredz! Perform advanced, fine-grained password spraying while remaining under the radar for your next Red Team engagement 🔥 github.com/synacktiv/capt…
Introducing Havoc Professional: A Lethal Presence We’re excited to share a first look at Havoc Professional, a next-generation, highly modular Command and Control framework, and Kaine-kit our fully Position Independent Code agent engineered for stealth! infinitycurve.org/blog/introduct…
Currently, if this patch is not deployed in an Active Directory, anyone with a user account is able to takeover any assets, except for DC, by default!
Microsoft just released the patch for CVE-2025-33073, a critical vulnerability allowing a standard user to remotely compromise any machine with SMB signing not enforced! Checkout the details in the blogpost by @yaumn_ and @wil_fri3d. synacktiv.com/publications/n…
If you thought phishing was now ineffective, you may have missed something 👀 My latest post highlights the advanced tactics used to bypass security controls and deceive even the most savvy users. Check it out ⤵️
From classic HTML pages to advanced MFA bypasses, dive in with @_atsika in an exploration of phishing techniques 🎣. Learn some infrastructure tricks and delivery methods to bypass common detection. 👉blog.quarkslab.com/technical-dive… (promise this one is legit 👀)
I've just completed the @MalDevAcademy Malware Development Course. The course presents modern techniques for bypassing security solutions, low-level development and evasion. I would totally recommend this course to Red Team operators requiring a high level of discretion!
Kerberos relay on The Hacker Recipes, brought to you by @BlWasp_ 💪 thehacker.recipes/ad/movement/ke…
Just finished to refactor my network #pivoting cheatsheet! If you are in an internal engagement, and you're stuck on a pivot, perhaps the solution will lie there: hideandsec.sh/books/cheatshe…
Following the recent @Synacktiv 's article about abusing WebClient authentications from multicast poisoning, I have made a quick PR on Responder to simplify the setup: github.com/lgandx/Respond…

Make Bloodhound Cool Again: Migrating Custom Queries from Legacy BloodHound to BloodHound CE medium.com/seercurity-spo…
New Active Directory Mindmap v2025.03! 🚀 📖 Readable version: orange-cyberdefense.github.io/ocd-mindmaps/i… 🔧 Now fully generated from markdown files—way easier to update and maintain! 💡 Got improvements? PRs welcome! 👉 github.com/Orange-Cyberde…
This looks off to you? Yeah... In the default configuration, NFS exposes THE ENTIRE FILE SYSTEM and not only the exported directory! This means that you can read every file on the system that is not root:root owned, e.g. /etc/shadow. But it can get even worse 1/4🧵
In our latest article, @l4x4 revisits the secretsdump implementation, offering an alternative avoiding reg save and eliminates writing files to disk, significantly reducing the likelihood of triggering security alerts. Read the details at synacktiv.com/publications/l….
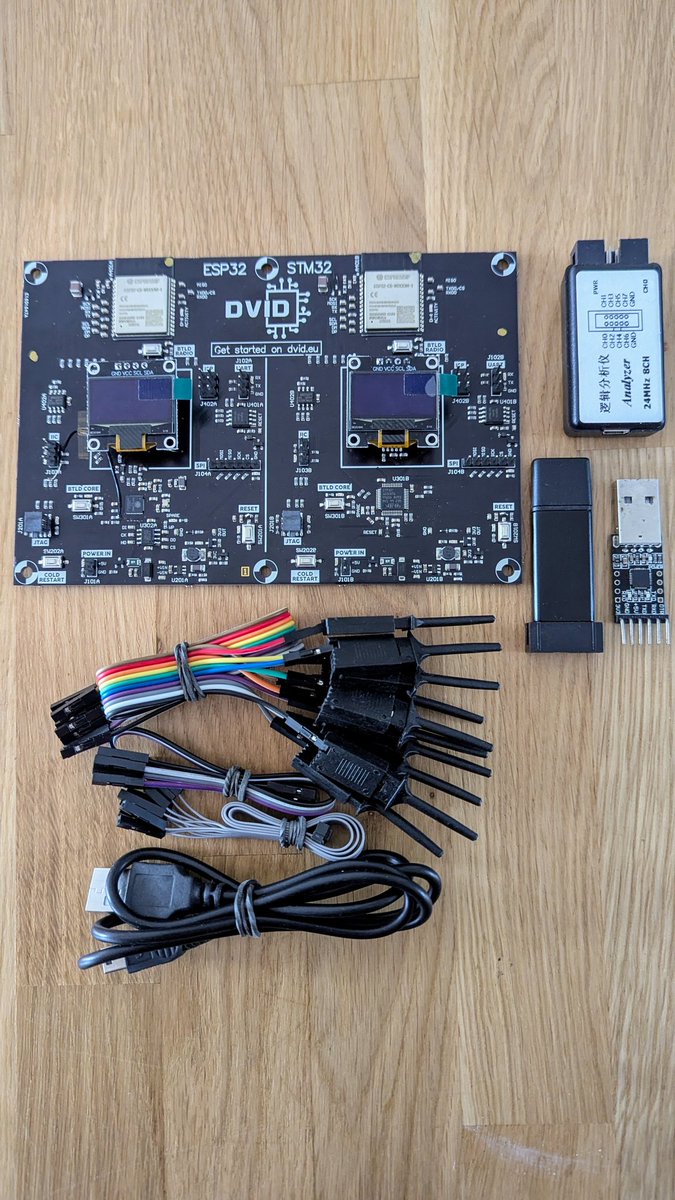
An interesting package just arrived at home! 👀 I'm starting to contribute to the DVID project by writing new trainings, and working on the wiki page. 🚀 If you are interested IoT security, check it out ! dvid.eu
Pretty interesting article to start digging into Intune !
In Part 1 of my Intune Attack Paths series, I discuss the fundamental components and mechanics of Intune that lead to the emergence of attack paths: posts.specterops.io/intune-attack-…
Released GHunt 2.3.3 with a new module : 🕷️ Spiderdal ! Put a domain name and quickly find tied assets, including the hidden ones, by abusing Google's assets links statements. New way for doing recon before a pentest ! 🥳
A few months ago, Microsoft released a critical patch for CVE-2024-43468, an unauthenticated SQL injection vulnerability in SCCM/ConfigMgr leading to remote code execution, discovered by @kalimer0x00. synacktiv.com/advisories/mic…
