
BallisKit
@BallisKit
BallisKit provides tooling and services to professional Pentesters & Red Teams. We develop MacroPack, ShellcodePack, and DarwinOps. #redteam #infosec
I have arrived in Athens, I will be attending @TheOffensiveX tomorrow! Ping me if you are there!
We are adding a binary injection vulnerability scanner to DarwinOps! -> A DarwinOps JXA template -> Scan for Injection vulnerabilities in binaries and Apps Vulnerable binaries could be abused to bypass EDR, hide a backdoor, access memory, or bypass TCC! #redteam

New video out 😊 showing how you can take control of port 445 and perform those magical relay attacks toward AD CS when working from a C2 agent. Way easier than before thanks to some great research by @zyn3rgy youtube.com/watch?v=e4f3h5…
MacOS security is very different from Windows. DarwinOps, our redteam tool targeting MacOS can help you tackle that issue! @antoinedss just posted on our blog to help you understand the basics of initial access on MacOS with DarwinOps #redteam blog.balliskit.com/macos-initial-…

🔥 Not your typical remote access tool… but it works. Chrome Remote Desktop isn’t just for tech support—it can be quietly repurposed for red team operations. I break down the how and why in my latest post. 👇
Chrome Remote Desktop can offer red teamers a subtle way to bypass restrictions—if they know how to use it. In this blog, @Oddvarmoe reveals a practical guide to repurposing Chrome Remote Desktop on red team operations. Read it now! trustedsec.com/blog/abusing-c…
Here is a reminder that a Powerful DotNET obfuscator is available in MacroPack. Assembly level obfuscation (or course). With the latest 2.7.5 it supports all your favorite #redteam DotNET tools! And tested on major EDRs :) blog.balliskit.com/obfuscation-an…

A new version of MacroPack Pro with improved DotNET obfuscator, new shellcode launcher, improved clickonce, and more will be released soon! Also, after Sliver, we a preparing tutorials with Mythic Apollo and Havoc 😎 #redteam

New tuto! Weaponize Mythic Apollo using MacroPack and ShellcodePack. Tested on EDRs of course. blog.balliskit.com/tutorial-mythi… #redteam

The video is sponsored by @BallisKit They have been a huge supporter of my on-and-off streaming/YouTube journey for a year++ now, which I greatly appreciate 🥰
It’s been a while since I made a video🫥, so here’s one looking at LDAPx by @MacmodSec , which is based on the amazing research present last year by @sabi_elezi and @danielhbohannon youtu.be/GZ7Vbvf2Dso
Rubeus and Mythic Apollo DotNET Payload Obfuscation with MacroPack! This video demonstrates the next MacroPack Pro features: - DotNET obfuscation and evasion - EDR Bypass ready to use profiles - Compatibility with Mythic Apollo stager #redteam youtu.be/mzuT1MAQSXY
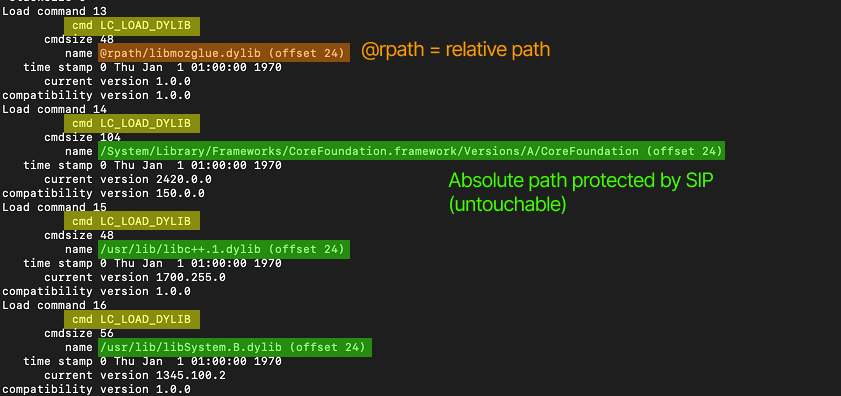
DLL injection and DLL proxying on macOS? Yes it is possible! Checkout this blog by @antoinedss about macOS automated DYLIB injection! #redteam blog.balliskit.com/macos-dylib-in…
How to weaponize Sliver C2 and evade EDRs? With BallisKit ShellcodePack and MacroPack of course! Checkout this new tutorial on our blog! #redteam blog.balliskit.com/tutorial-slive…

Need initial access payloads for MacOS? Need help to bypass EDR on MacOS? Need undetected persistance on MacOS? Say no more and contact us about DarwinOps Our redteam ToolKit dedicated to MacOS! #redteam
For us, "EDR bypass" is not just a buzzword. MacroPack, ShellcodePack, and DarwinOps all come with bypass presets for major EDRs and Antivirus Those presets are regularly updated and tested! If you want to see a demo or an equivalent screenshot for the major EDRs contact us with…