Back Engineering Labs
@BackEngineerLab
Developing http://CodeDefender.io Discord: https://discord.gg/sgedeapTMm
❗️ We discovered a bug in Microsoft's driver compliance checks which are used to determine if "Memory Integrity" can be enabled on a system. ❌The function "vsbapi!HvciIsDriverImage" is comparing an RVA against the raw file size. learn.microsoft.com/en-us/answers/…


🧰 CodeDefender API and CLI are live Protect binaries from the terminal or Rust SDK Upload → Analyze → Obfuscate → Download YAML configs give full control over passes, symbols, and transform logic 🔗 github.com/codedefender-i… 📔 docs.codedefender.io/features/api

🚀 CodeDefender SDK now supports source-level macros! Obfuscate functions in Rust/C/C++ by tagging them with your pre-defined obfuscation profile. 🦀 #[codedefender("Profile1")] 💻 CODEDEFENDER("Profile1", ...) Docs + examples 👉 github.com/codedefender-i… #infosec #rustlang…
![BackEngineerLab's tweet image. 🚀 CodeDefender SDK now supports source-level macros!
Obfuscate functions in Rust/C/C++ by tagging them with your pre-defined obfuscation profile.
🦀 #[codedefender("Profile1")]
💻 CODEDEFENDER("Profile1", ...)
Docs + examples 👉 github.com/codedefender-i…
#infosec #rustlang…](https://pbs.twimg.com/media/GviPpReakAYoNKy.png)
Our CodeDefender SaaS has received a major update which includes the following: 🛠️Our new and improved compiler framework 💥SSE hardened mutations 🚀New UI/UX interface 💪Custom obfuscation pass configuration 🔗Register now: app.codedefender.io #reverseengineering…

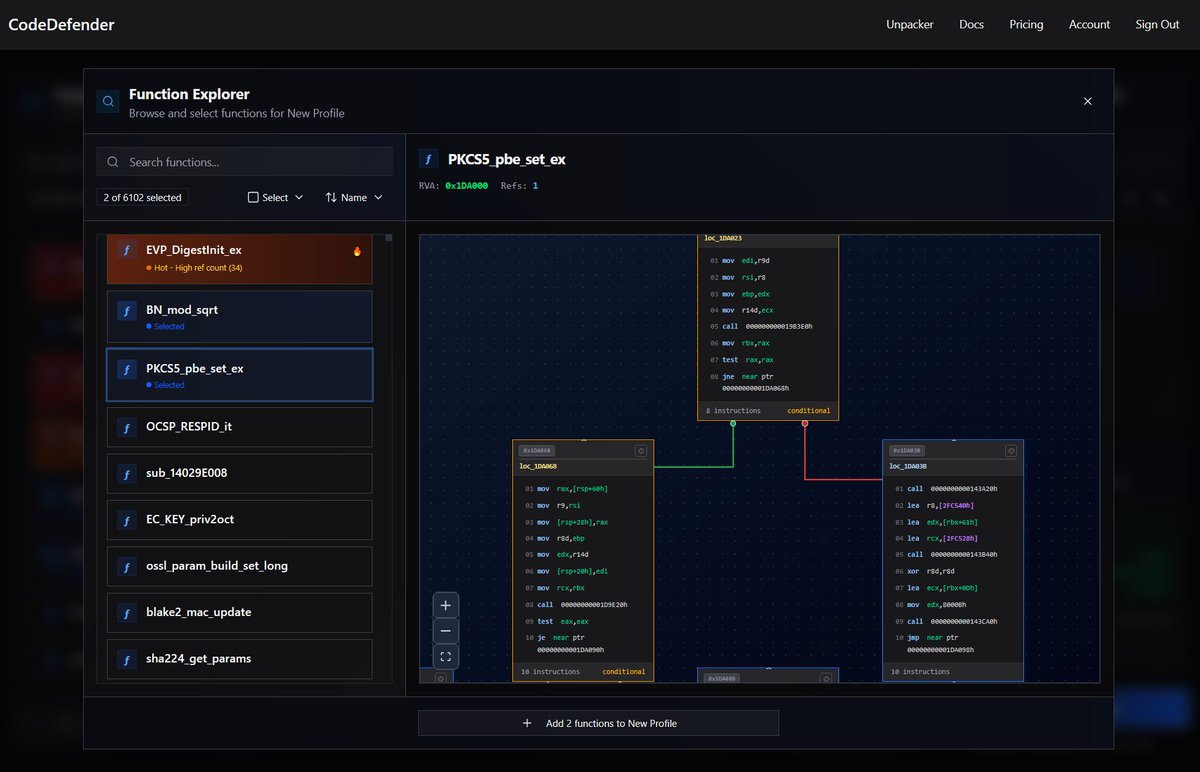
What has BELabs been up to ⁉️ Check out these new SSE based obfuscations. 🫣 We have completely rewritten our compiler from the ground up to pave the way for ARM support. ✅ This has allowed us to make the world's strongest bin2bin obfuscation framework even stronger.💪 The…

Can your bin2bin do this and still boot? CodeDefender.io can. See it in action with a demo at the end! 👉youtu.be/3LOGxOHfUHg
🚨 How are the geniuses at @BackEngineerLab revolutionizing binary obfuscation with CodeDefender.io? Learn about the unique challenges & solutions in bin2bin, virtualization & anti-tamper. See CodeDefender in action with a demo at the end! 👉youtu.be/3LOGxOHfUHg
what is CodeDefender and who is the handsome man in the corner? find out tomorrow when we drop our interview with the @BackEngineerLab team
Given the recent events with VMPSoft DMCA'ing educational YouTube videos demonstrating how to unpack malware protected with VMProtect, we have decided to release a free to use unpacker which works for all versions of VMP 3.x including the most recent version. Simply sign…

VMPSoft has been DMCA-ing YouTube videos which show how to combat malware payloads abusing VMProtect
We are excited to release our second blog post discussing our technical capabilities of integrating llvm-msvc compiled code into already compiled programs in efforts to build anti-cheats, anti-tamper, packers, import protectors, anti-debug functionality, runtime tracing, and much…
We are very excited to sponsor @mrexodia with 500$ His open source contributions have made it possible to do what we do. If you have ever benefited from using x64dbg.com or other tools developed by @mrexodia consider sponsoring him on github. Special thanks to all of…
We have made public a tool called "pdbgen2" which can generate a PDB file for CodeDefender.io obfuscated binaries. The PDB offers function/basic block level granularity. This is very useful for analyzing crash dumps and debugging your obfuscated code in production!…


CodeDefender SaaS now provides you with a debug map file format so that you can debug crashes in your binary code. Soon we will update your PDB file (if provided) so you can use it directly in WinDbg and Visual Studio, however this map file format works for PE files provided…


Recently, @BackEngineerLab released the crackme obfuscated by the CodeDefender and I reversed the binary: gist.github.com/5unKn0wn/24fa0…. The crackme implemented modified SipHash24, and the goal is to find the input that matches the hash. The obfuscation was nice and quite a challenge !
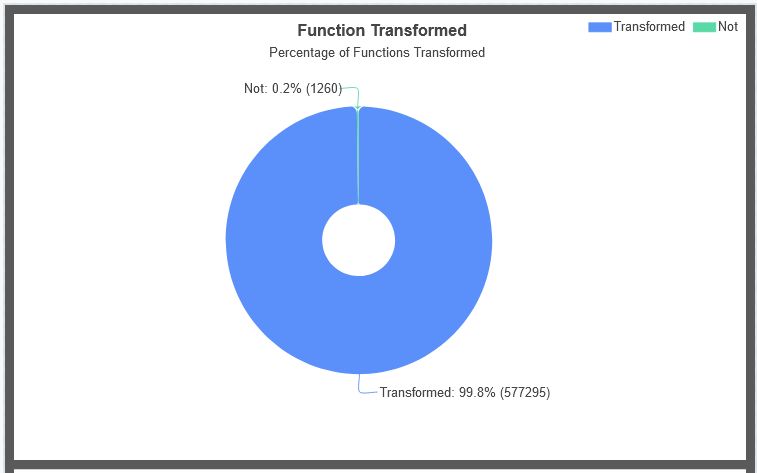
We have added @playrust GameAssembly.dll module coverage statistics to our binstats repo. We are able to statically uncover over 99% of functions within the il2cpp generated DLL (242mb) and transform them! No PDB or source code was used to generate these statistics!…
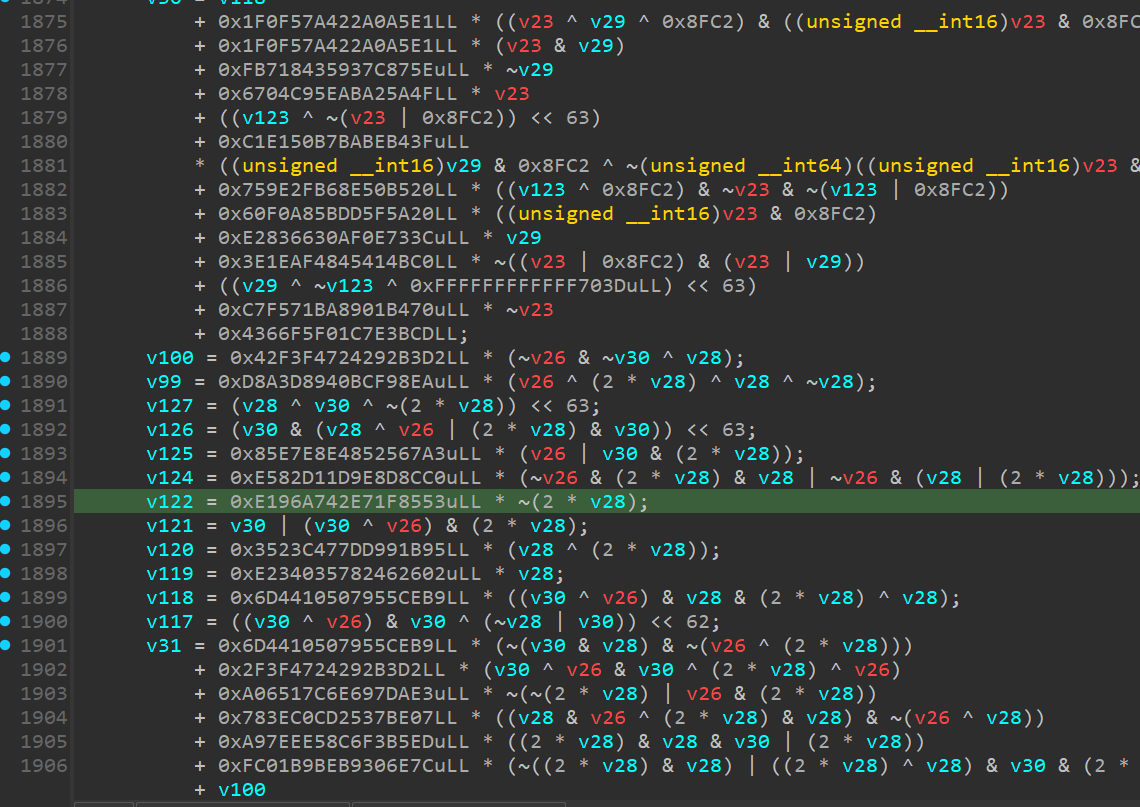
Loop-Based Semantic Encoding is a transformation that takes simple operations (add, and, xor, sub) and transforms them into a loop structure. We have made this obfuscation technique available for medium and large tier subscribers to CodeDefender. Docs: docs.codedefender.io/features/funct……

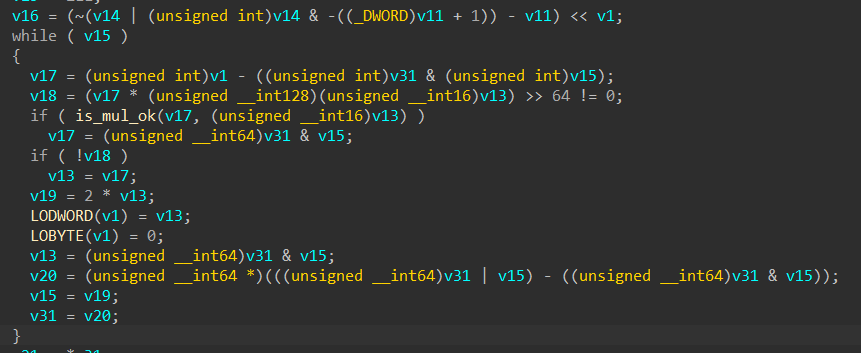
🚀 We've been hard at work to make CodeDefender even better for you! Here's what's new: ✨ A sleek new UI for our SaaS platform 🧩 A Mixed Boolean Arithmetic obfuscation pass 🔗 A brand-new API to supercharge your workflows docs.codedefender.io postman.com/back-engineeri…