Almond OffSec
@AlmondOffSec
Offensive Security team at Almond - Follow us also on https://infosec.exchange/@AlmondOffsec
The Blog post about "Revisiting Cross Session Activation attacks" is now also public. Lateral Movement with code execution in the context of an active session? 😎 Here you go: r-tec.net/r-tec-blog-rev…
Following @ShitSecure's TROOPERS talk and release of BitlockMove, we're releasing our internal DCOMRunAs PoC made by @SAERXCIT last year. It uses a similar technique with a few differences, such as DLL hijacking to avoid registry modification. github.com/AlmondOffSec/D…

Did you know deleting a file in Wire doesn’t remove it from servers? Team member @myst404_ took a closer look at Wire's asset handling and identified 5 cases where behaviors may diverge from user expectations. offsec.almond.consulting/deleting-file-…

Attacks against AD CS are de rigueur these days, but sometimes a working attack doesn’t work somewhere else, and the inscrutable error messages are no help. Jacques replicated the most infuriating and explains what’s happening under the hood in this post sensepost.com/blog/2025/divi…
To escape a locked-down Citrix environnement, team member @saerxcit wrote a basic shellcode loader in OpenEdge ABL, a 40 years old english-like programming language. We're sharing it in the off chance someone else might one day need it: github.com/AlmondOffSec/O…
This issue was assigned CVE-2024-52531. While the CVE description states that the vulnerability cannot be reached from the network, it seems, in fact, possible (check the blogpost for details).
Team member @sigabrt9 describes a fuzzing methodology he used to find a heap overflow in a public @yeswehack bug bounty program for Gnome: offsec.almond.consulting/using-aflplusp…
You can now also follow us on Mastodon : infosec.exchange/@AlmondOffsec
You can now also follow us on Bluesky: bsky.app/profile/almond…

📢 Hunter Alert! Here's an excellent write-up by @sigabrt9 - who recently uncovered a bug in @gnome’s #BugBounty program. Perfect to expand your knowledge about finding bugs in open-source programs 👉 offsec.almond.consulting/using-aflplusp… Thank you @sigabrt9 for this valuable contribution!
Team member @sigabrt9 describes a fuzzing methodology he used to find a heap overflow in a public @yeswehack bug bounty program for Gnome: offsec.almond.consulting/using-aflplusp…

New article on F5! A write-up on CVE-2024-45844, a privilege escalation vulnerability in BIG-IP by team member @myst404_ offsec.almond.consulting/privilege-esca…

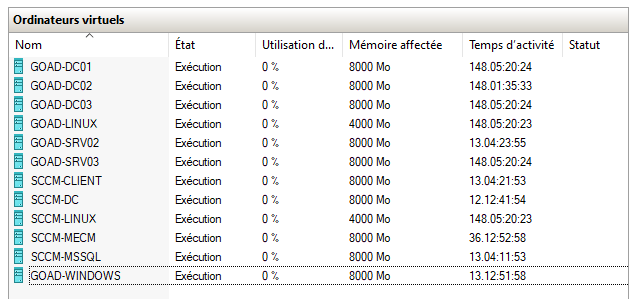
If you are lucky enough to have a Windows Server Datacenter with Hyper-V, you can automatically activate @M4yFly 's GOAD VMs, so rebuilding the lab every 180 days is no longer needed. We POCed a Vagrant-style script here: github.com/AlmondOffSec/G…
How does F5's Secure Vault, its "super-secure SSL-encrypted storage system" work? Response in this article by team member @myst404_ offsec.almond.consulting/deep-diving-f5…

Got root, what now? Practical post-exploitation steps on an F5 Big-IP appliance, by team members @lowercase_drm and @myst404_ offsec.almond.consulting/post-exploitin…

Stoked to see PassTheCert featured in @ippsec ‘s solution to @hackthebox_eu Authority🧑⚖️! Find the tool here: github.com/AlmondOffSec/P…
Authority showcased an ADCS Attack in the root step. Before we get there, need to decrypt an ansible vault and steal a LDAP cred with a rogue server. The ADCS involved ESC1, which is the creation of a machine account and then PassTheCert to gain access youtube.com/watch?v=7AF5ri…
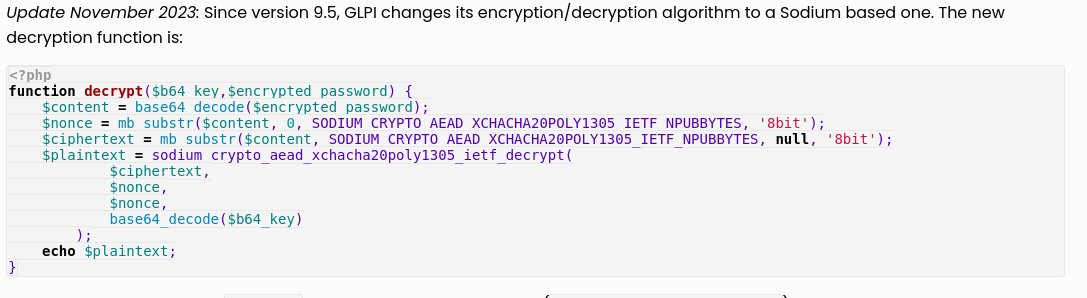
We updated this old gem by @myst404_ to include the new GLPI decryption algorithm. offsec.almond.consulting/multiple-vulne…
Understanding the different types of LDAP authentication methods is fundamental to apprehend subjects such as relay attacks or countermeasures. This post by @lowercase_drm introduces them through the lens of Python libraries. offsec.almond.consulting/ldap-authentic…
