ACE Responder
@ACEResponder
Practice threat hunting & detection engineering in a real SIEM with real attacks. Join us and become the best.
🚀 Take your skills to the next level with our first professional certification: Certified Enterprise Defensive Analyst (CEDA)! aceresponder.com/eda Perfect for junior to intermediate defenders looking to go beyond alerts. 💻 What you'll learn: • Dive deep into Linux,…
✅The UAC Bypasses module is now available in the instant SIEM! Practice investigating a diverse set of UAC bypasses with Kusto Query Language (KQL)! #ThreatHunting #DFIR aceresponder.com/learn/uac-bypa…
 * [Windows Logons](/learn/opensearch-tutorial) Welcome to this module on UAC Bypasses. User Account Control (UAC) is a...](https://pbs.twimg.com/card_img/1948492944077398017/aIt-F4Qd?format=jpg&name=orig)
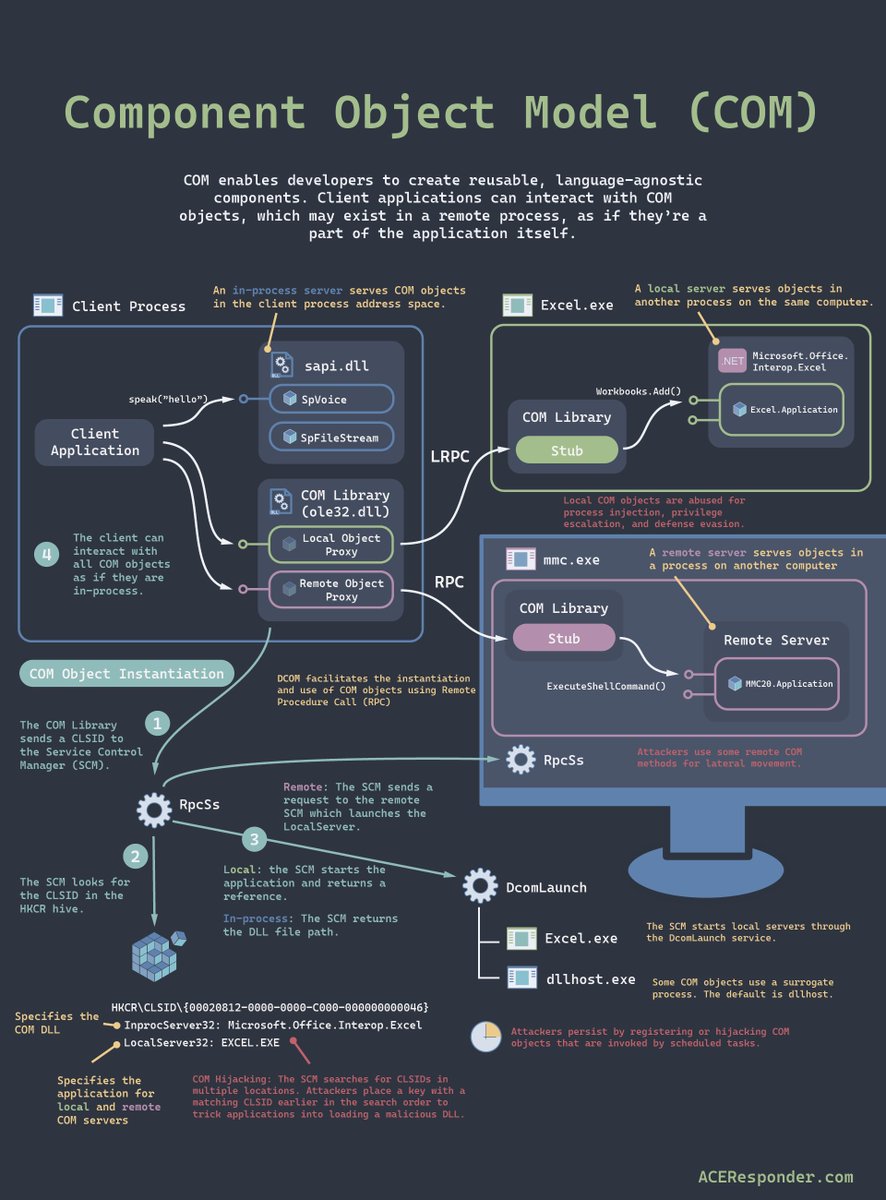
How Component Object Model (COM) works. #ThreatHunting #DFIR #Windows #Microsoft
New blog 💉Prompt Injection: How You Will Be Hacked In this blog I demonstrate a prompt injection attack against Anthropic's Claude using a poisioned log entry. I also discuss ways to mitigate attacks against defensive AI agents. #ThreatHunting #DFIR aceresponder.com/blog/prompt-in…

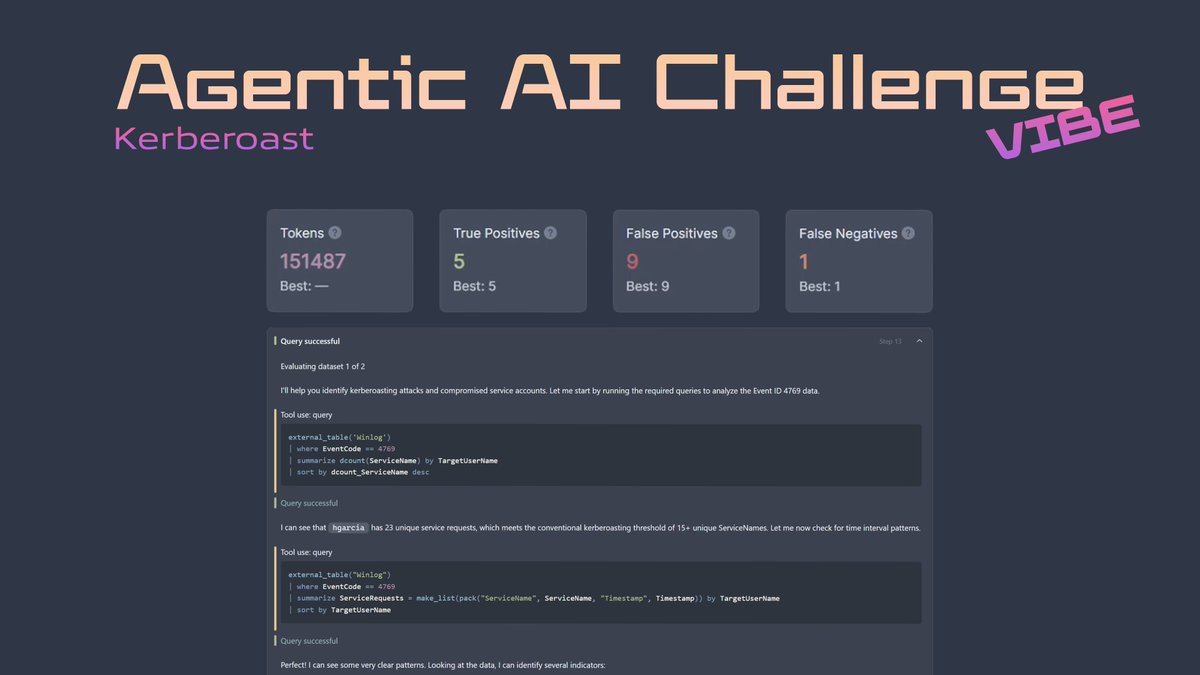
💥The first ever Agentic AI defensive cyber challenge is now available on ACEResponder.com: Kerberoast Prompt an AI agent to identify stealth kerberosting. #ThreatHunting #DFIR
How cross-trust Kerberos authentication works #ThreatHunting #DFIR
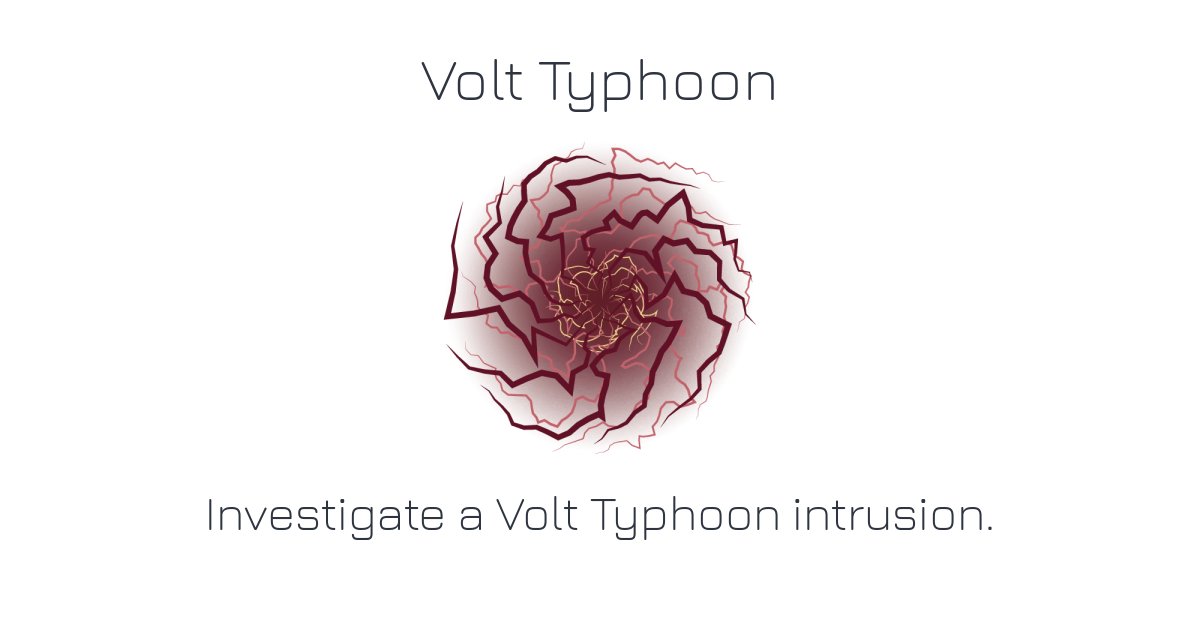
⚡️The Volt Typhoon challenge is now available in the new instant Kusto-based SIEM! Take on an advanced persistent threat that targets critical infrastructure. aceresponder.com/challenge/volt…
How DCOM lateral movement works. #ThreatHunting #DFIR
📣The Pivot challenge is now available in or instant in-platform Kusto SIEM! Uncover an intrusion with unique Command and Control techniques. aceresponder.com/challenge/pivot

☁️ Pass-the-PRT: How attackers pivot to the cloud. #ThreatHunting #DFIR
✅The Qakbot challenge is now available in the instant Kusto SIEM! Take on one of world's most prolific cyber threats. #ThreatHunting #DFIR aceresponder.com/challenge/qakb…

Windows events that identify AD user object takeover. #ThreatHunting #DFIR

📢⚡️The Acquisition challenge is now available in the instant kusto SIEM! An attacker takes advantage of a recent acquisition. Explore a breach spanning multiple AD forests and expose the attacker's persistence efforts. #ThreatHunting #DFIR aceresponder.com/challenge/acqu…

🆕Our Exchange Logons learning module is now live in our instant, in-platform SIEM! Can you characterize authentication-based attacks against Exchange? Learn how in this beginner learning module. aceresponder.com/learn/exchange…
 * [Windows Logons](/learn/windows-logons) for those unfamiliar with password spraying and Windows logons This module covers 4...](https://pbs.twimg.com/card_img/1947457112801488896/wwFrkdkE?format=jpg&name=orig)