Andrew
@4ndr3w6S
Detection Engineering @HuntressLabs | Prev. Practice Lead, TAC (Purple Team) @TrustedSec | @SpursOfficial Super Fan - COYS!
Domain Controllers are not PAWs. Please DO NOT USE your Domain Controllers as “jump boxes” to other systems.
“This leverages the Microsoft-Windows-DotNETRuntime ETW provider which is often 'patched' - but why would someone patch an provider they don’t think anyone is collecting data from?” 😈
Have you ever wondered if there was a way to deploy a "Remote EDR"? Today I'm excited to share research I've been working on for the past couple months. This dives into DCOM Interfaces that enable remote ETW trace sessions without dropping an agent to disk. Includes a detailed…
💯 percent agreed! But… Wild how everyone’s focused on wiping payloads, but no one mentions cleaning up AD—things that got modified, deleted, or added. Like yeah, your tools are gone, but AD’s still wearing the scars.
This shouldn’t be a topic up for debate and also applies to pentesting. You need to know your tools which often requires looking at code and running them in a lab for observable IoCs.
Excited to be co-hosting the first onsite @DEATHCon2025 with @cyberGoatPsyOps in Austin, TX. It’s happening 😈 Don’t miss this 🤘 eventbrite.com/e/deathcon-202…

Happy to finally share a new blog with @exploitph on our work revisiting the Kerberos Diamond Ticket. ✅ /opsec for a more genuine flow ✅ /ldap to populate the PAC 🆕 Forge a diamond service ticket using an ST We finally gave it a proper cut 💎 huntress.com/blog/recutting…
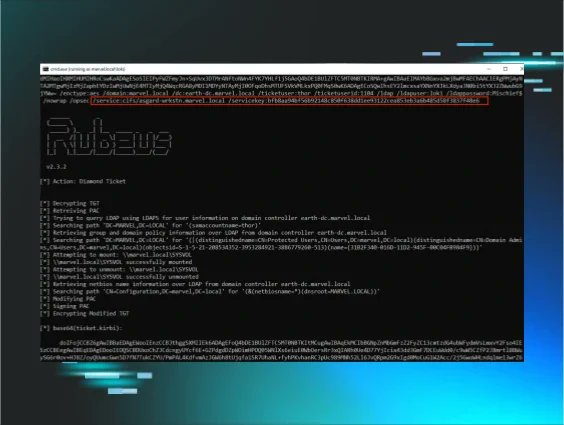
Back to blogging with @exploitph! Not the post title, just a little snippet 👀 Coming soon 😈

“Of course I got two words for ya…” “BOF WHEN?!”
BadSuccessor ports: ◾️.NET github.com/logangoins/Sha… ◾️Python github.com/cybrly/badsucc… ◾️PowerShell github.com/LuemmelSec/Pen… 🎯 Implemented in these tools: ◾️Netexec: github.com/Pennyw0rth/Net… ◾️BloodyAD github.com/CravateRouge/b…
Late Friday blog drop! @HuntressLabs had some fun with #DefendNot by @es3n1n 😈 This tool shows that defense evasion isn’t just about avoiding tools—it’s about bending them. Here’s how attackers turn your security products into blind spots. 🛡️ huntress.com/blog/defendnot…

Kerberos-KDCProxy Event 400: ‘An HTTP request was received.’ 🎉 After combing through Kerberos logs for ages, I’ve never felt more enlightened! 🤪

This shouldn’t be a topic up for debate and also applies to pentesting. You need to know your tools which often requires looking at code and running them in a lab for observable IoCs.
Serious question for the collective genius minds of infosec: who’s actually responsible for cleanup after a red team op? Me, mid-exfil, deleting payloads like a janitor with a C2? Or is that someone else’s job? Just tryna do it right before I get yelled at again
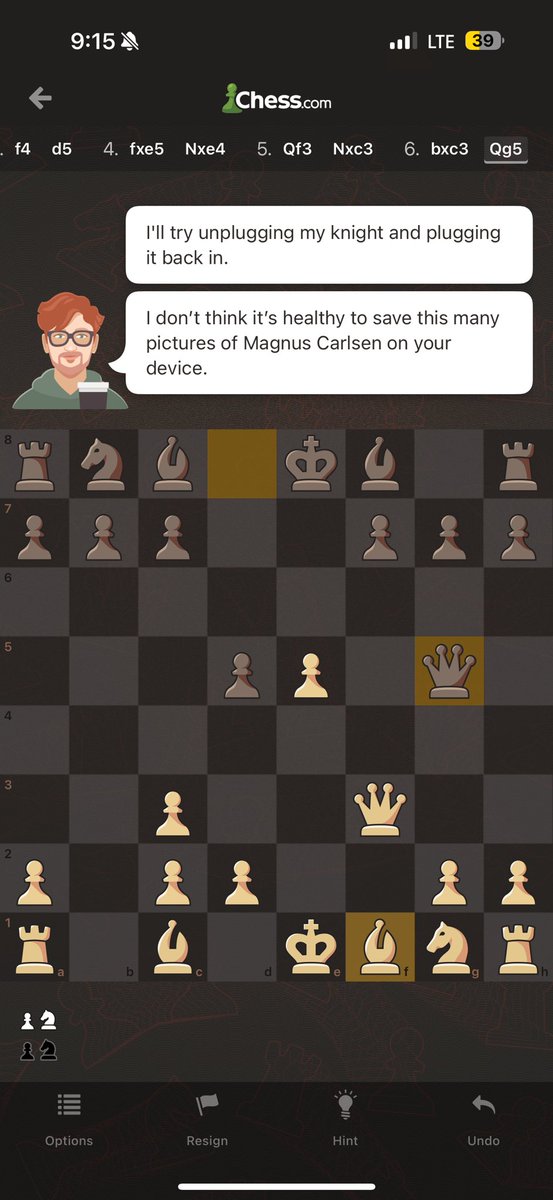
Looks like @_JohnHammond got turned into a @chesscom bot 🤖!! They might have nerfed his Elo, and even gave him an @MagnusCarlsen obsession. 🤣 But at least the wit, jokes and sarcasm made the cut!
🕵️♂️ Bridging criminal justice and detection engineering… I’m excited to share my latest blog with @HuntressLabs, where I merge my academic background in criminal justice with my passion for detection engineering. By applying criminological theories, we gain deeper insights into…