
2OURC3
@2ourc3
building things - breaking others | @auditor_codes
Introducing Havoc Professional: A Lethal Presence We’re excited to share a first look at Havoc Professional, a next-generation, highly modular Command and Control framework, and Kaine-kit our fully Position Independent Code agent engineered for stealth! infinitycurve.org/blog/introduct…
Joining @rektoff_xyz bootcamp about Solana Rust Security! Really thrilled and thankful to start this one :D
Releasing this fun tool Golem based on @0xdea, LLVM, LLM and @semgrep Golem automates C/C++ vulnerability discovery by combining Semgrep rule scans, LLVM call-graph & CFG slicing, and AI-driven context analysis. Tool: github.com/20urc3/golem Article: bushido-sec.com/index.php/2025…
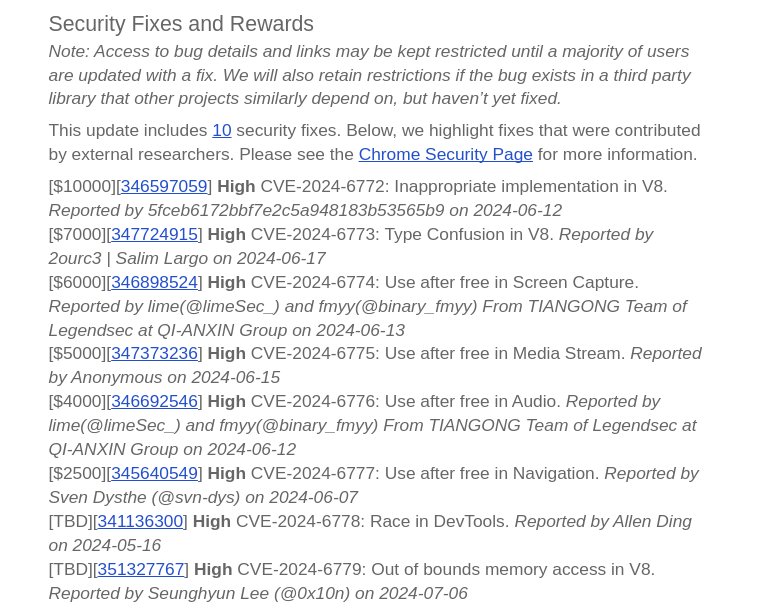
Write-up of my v8 bug: Critical type confusion in V8's Turboshaft compiler allowed stale pointers to bypass GC, leading to exploitable memory corruption. Full details + PoC: bushido-sec.com/index.php/2025…

I wrote a comprehensive guide on harnessing libraries for effective fuzzing with AFL++ ! Have a look => github.com/20urc3/Publica…
Going to #38c3 was on my wishlist for MANY years. I am extremely happy to have been able to attend this super fun con for the first time, I've watch many great talks, met a bunch of really cool nerds and loved the hacking atmosphere! ✨️




🥳CVE-2024-53589: I discovered a heap buffer-overflow vulnerability in objdump affecting version 2.43, during a fuzzing campaign with @aflplusplus More details: bushido-sec.com/index.php/2024…

Following 7zip 24.08 release, @thezdi disclosed yesterday my vulnerability in 7zip 24.07: CopyCoder Infinite Loop Denial-of-Service Vulnerability - CVE-2024-11612 I found this vulnerability last summer during a fuzzing campaign with @aflplusplus bit.ly/4fZUnfz

It was a fantastic experience giving a talk about automated vulnerability research for SANS today. Grateful for this opportunity, very happy to meet all the other fantastic speakers there.


Really proud! My vulnerability in Chrome v8 has been disclosed today! CVE-2024-6773 Type confusion in the v8 engine. chromereleases.googleblog.com/2024/07/stable…
Join meet at @_leHACK_ for my talk: Hacking satellites: From SDR to RCE. 👾
[🎙️ #Talk] Discover #leHACK 2024 talk: Hacking satellites: From SDR to RCE presented by @2ourc3 📅 Saturday, July 6th ⌚ 14:45 ℹ️ Details: buff.ly/3VNMOl3 🎟️ Tickets: buff.ly/3Vcrbtg
Thats a wrap! Except the mandatory bug in the demo, it went pretty smoothly! Thanks Stephen for the invite, hope you all liked the talk
Introduction to Fuzzing
Thanks @Steph3nSims for this opportunity! Hope you all will enjoy this one!
Super excited about tomorrow's Off By One Security stream at 11AM PT. We have @2ourc3 coming on to present on Fuzzing. This one will be a demo & workshop and you can choose to follow along! Install instructions: github.com/20urc3/Talks/t… Stream link: youtube.com/watch?v=gTISW-…